
The healthcare industry depends a lot on technology — whether it’s online appointments, digital health records, or connected medical devices. While this reliance has made patient care faster and more effective, it has also given cybercriminals more ways to break in. Now, it’s more frequent than ever to come across news of threat actors encrypting critical data, rendering systems until a ransom is paid. Since this specific industry is driven by the ‘urgency to treat patients in time,’ organizations are often left with no choice but to give in and pay the ransom to restore operations quickly.
Malicious actors leverage this very sensitive nature of the industry to pull off phishing and social engineering attacks, manipulating staff members or patients into revealing confidential data, downloading malware-infected files, gaining unauthorized access to systems, sharing health insurance details, and whatnot!
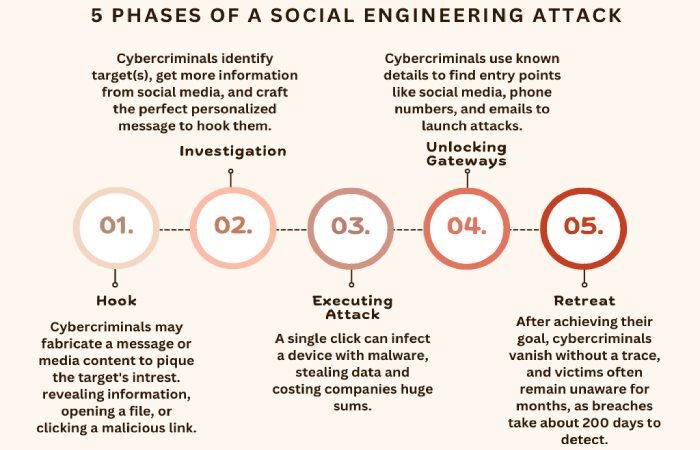
The growing menace of ransomware and BEC attacks
As per the Health-ISAC_2025-Annual-Threat-Report, ransomware remains the biggest threat for the healthcare industry in both 2024 and 2025. In fact, as a chilling reminder of how vulnerable the healthcare industry is to ransomware attacks, the infamous Medusa ransomware gang hit the UK’s HCRG Care Group and stole over 50TB of sensitive data. They then demanded a hefty ransom of $2 million to stop the public release!
Now, if we talk about the Business Email Compromise or BEC attacks, the situation is no better. In this type of attack tactic, threat actors impersonate C-level executives or other leaders and trick employees into wire transferring funds to bank accounts controlled by attackers or request confidential details via email.

Since the entire healthcare industry handles sensitive data and is driven by the urgency to treat people, cyberattacks often cause more harm than just financial loss! These incidents lead to legal issues and reputational damage.
Gen-AI is drafting flawless, convincing emails
Unprofessional tone, poor graphics, grammar mistakes, etc., are considered some of the red flags of a potential phishing email. But with the advent of generative AI, it’s so easy to draft hyper-personalized, professional-looking, and flawless phishing emails that easily convince the targeted recipient to believe that the message is absolutely safe. AI is not limited to synthetic emails; it’s, in fact, used for deep fake videos and voice recordings.

Moreover, AI-powered malware has the capability to learn from a system’s behaviour. This helps them avoid getting detected by security filters and adapt to the environment, as and when needed.
In short, AI has worsened the situation by lowering the entry barrier for cybercriminals and has empowered them to scale, personalize, and conceal their malicious moves. This has put the already-burdened healthcare systems at even higher cybersecurity risks.
Infostealers are the silent triggers behind the healthcare cyberattacks
Infostealers are malware programs that secretly enter a system to steal personal and sensitive information. These are usually spread by embedding them in phishing emails, fake software downloads, or links on fraudulent websites. Once they are inside your system, they silently operate in the background to collect data and send it to the hacker’s server.
Usually, cybercriminals deploy infostealers through deceptive phishing emails that include fake hospital notices, HR updates, software alerts, etc. They may even embed them in fake medical portals that staff access. After getting inside the system, they harvest login credentials to critical systems like EHR platforms, internal dashboards, payment portals, and cloud storage. But the damage doesn’t stop there.
The stolen credentials can be sold to Initial Access Brokers, or they themselves can exploit them to infiltrate deeper into the network. They try escalating privileges so that they can make changes or gather intelligence without tipping anybody off. What follows can be truly damaging— ransomware or data extortion that shuts down billing systems, delays surgeries, and puts patient care at risk, all starting from just one stolen login.
In February 2024, Change Healthcare became the target of an infostealer-driven massive ransomware attack that was attempted by exploiting stolen credentials (likely harvested by an infostealer).
This gave hackers unauthorized access to a Citrix service that ultimately halted billing, claims, and prescription systems across the US. It also exposed data from more than 100 million people, resulting in a reported $22 million ransom payment.

Prevention gives power in cybersecurity
In the healthcare industry, prevention isn’t just a best practice— it’s a necessity. In times when systems and people are vulnerable to ransomware, infostealers, and data extortion, it’s vital to activate the appropriate security measures. What is more important is a holistic, multi-layered defense strategy– you can’t just rely on a single antivirus to protect you from all the angles. You must deploy a combination of security tools that can work in tandem with each other to ensure not only operational continuity but also build patient trust and keep your organization aligned with compliance.
One critical area often overlooked is email security. Deploying protocols like SPF, DKIM, and DMARC helps authenticate emails and prevent impersonation-based attacks such as phishing and business email compromise. In a sector where seconds matter and data is priceless, investing in preventive cybersecurity isn’t optional—it’s the smartest form of defense.






