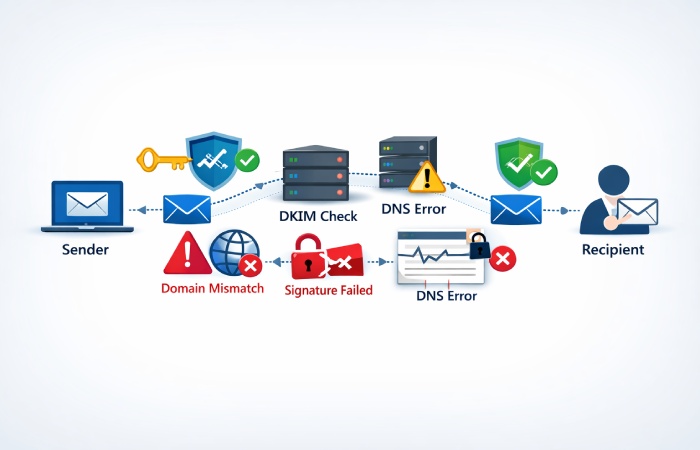
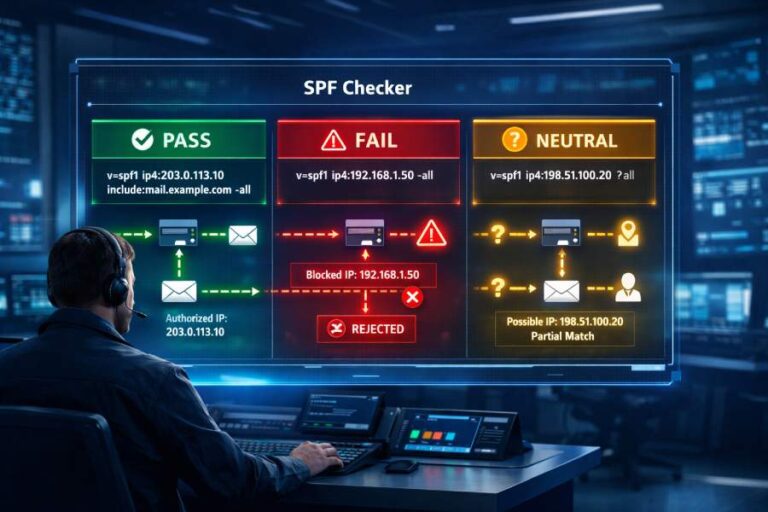
AutoSPF Explains: The Definitive Guide to Adding an SPF Record to Cloudflare
Email is one of the most powerful communication tools in the digital age — but with that power comes responsibility. If you’re running a domain that sends emails — whether transactional messages, newsletters, or internal team emails — you must authenticate those messages correctly. Without proper authentication, your emails risk being tagged as spam, blocked,…