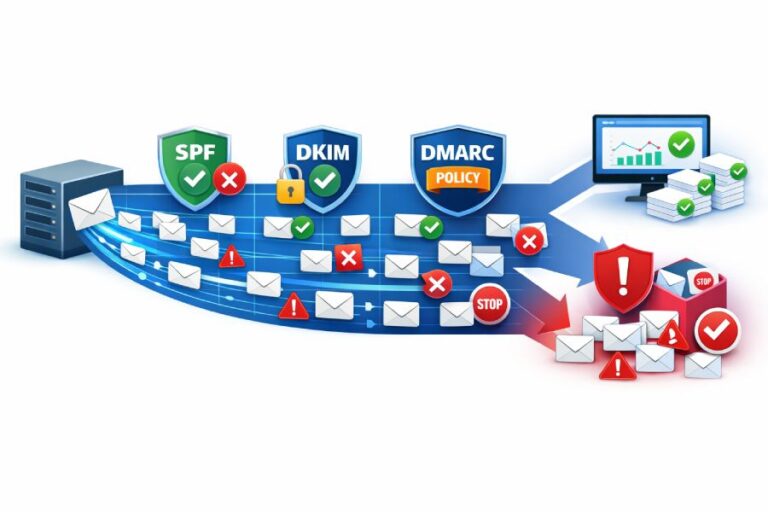
Email authentication is no longer a “set it once and forget it” task. In 2026, mailbox providers are applying stricter filtering rules, and even small SPF or DKIM mistakes can quietly push legitimate emails into spam folders or block them entirely. Many organizations believe their authentication is correctly configured simply because records exist in DNS, but outdated entries, missing sending sources, weak DKIM keys, or lookup limit errors often go unnoticed until deliverability drops or spoofing incidents occur.
As companies adopt multiple cloud platforms, marketing tools, and automated email systems, maintaining accurate SPF and DKIM configurations has become more complex than ever. Without routine validation and monitoring, small configuration gaps can quickly turn into large-scale deliverability problems. Understanding the most common SPF and DKIM mistakes and how to prevent them helps organizations protect domain reputation, maintain inbox placement, and ensure trusted email communication in an increasingly strict authentication landscape.
Why SPF and DKIM accuracy matter more in 2026
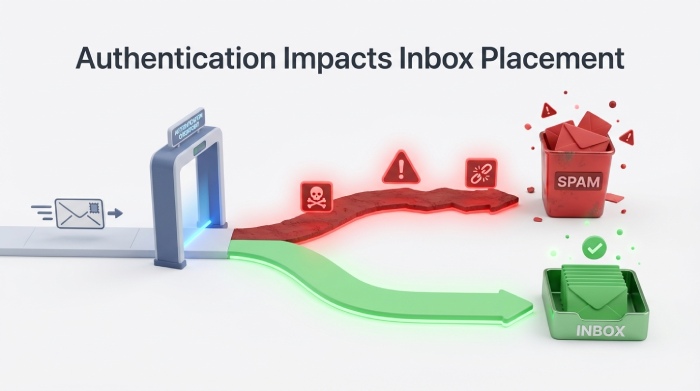
Mailbox providers such as Gmail, Yahoo, and Microsoft have strengthened their email authentication requirements in recent years, and these requirements will continue to tighten in 2026. Messages that fail SPF or DKIM validation are now far more likely to be filtered, quarantined, or rejected before they even reach the inbox. This means that even small configuration errors that previously went unnoticed can now directly affect whether emails are delivered successfully.
How authentication failures affect deliverability and sender reputation
When SPF or DKIM fails repeatedly, mailbox providers begin to treat the sending domain as less trustworthy. Over time, this reduces sender reputation, which makes it harder for even legitimate emails to reach the inbox. Marketing campaigns, transactional emails, and important customer communications may start landing in spam folders, causing engagement rates and customer trust to drop. Recovering sender reputation can take significant time and effort, which makes prevention very important.
The connection between SPF, DKIM, and DMARC alignment

SPF and DKIM do not work in isolation. They form the foundation for DMARC alignment, which determines whether a domain passes overall authentication checks. If SPF or DKIM is misconfigured, DMARC policies such as quarantine or reject may cause legitimate emails to be blocked. An accurate configuration ensures that all three mechanisms work together to verify the sender’s authenticity.
Business risks caused by misconfigured email authentication
Incorrect authentication settings can lead to more than deliverability problems. Attackers may exploit weak or incomplete configurations to spoof company domains and launch phishing campaigns. This can damage brand reputation, reduce customer confidence, and create compliance risks. Maintaining accurate SPF and DKIM records helps organizations protect both their email performance and their brand identity.
Most common SPF mistakes to avoid
Even when organizations publish an SPF record, configuration mistakes often reduce its effectiveness. These issues may remain unnoticed for months, yet they can quietly impact email delivery and increase the risk of spoofing. Understanding the most common SPF errors helps ensure that your domain remains properly authenticated.
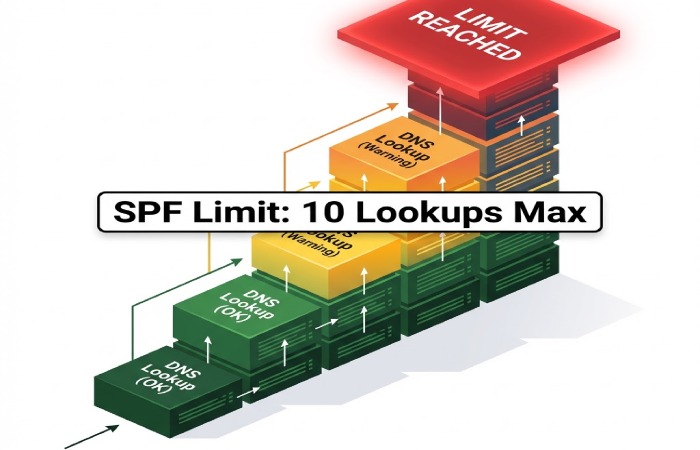
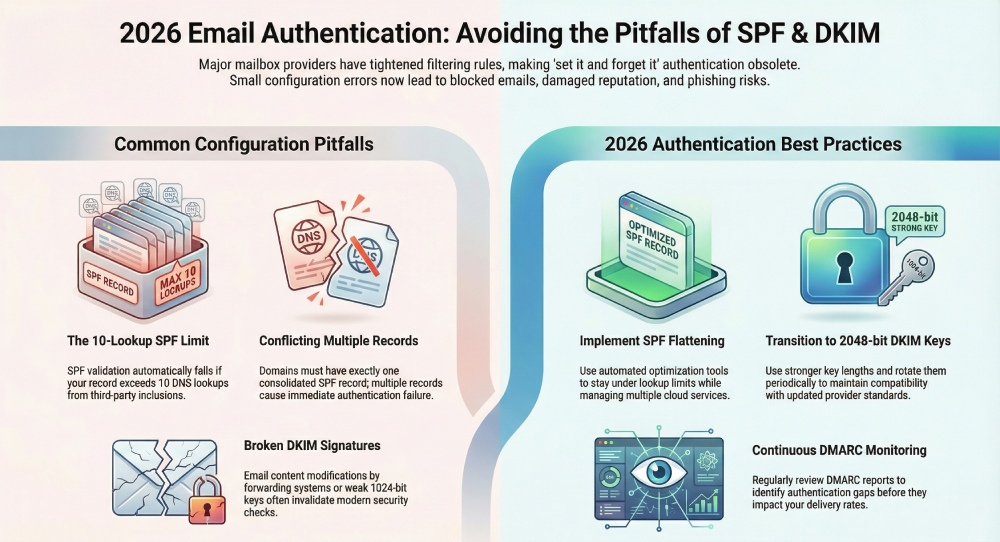
Exceeding the 10 DNS lookup limit
SPF evaluation allows a maximum of 10 DNS lookups. When a record contains too many include, a, mx, or redirect mechanisms, this limit can be exceeded. Once the lookup limit is crossed, SPF validation fails automatically, even if all sending sources are legitimate. Complex email environments that rely on multiple third-party services are especially vulnerable to this issue.
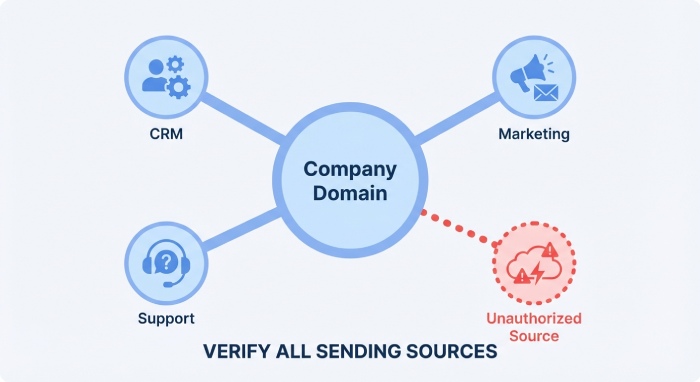
Missing authorized sending sources
Many organizations forget to update their SPF record when new email platforms, marketing tools, or cloud services are introduced. If a legitimate sending source is not listed in the SPF record, emails sent through that platform may fail authentication and be treated as suspicious by mailbox providers.
Using overly permissive SPF policies (~all)
Some domains use the soft fail policy (~all) for extended periods instead of moving to a stricter enforcement policy. While this approach allows monitoring during initial deployment, leaving it in place permanently weakens domain protection because unauthorized senders may still pass certain filtering checks.
Publishing multiple SPF records for the same domain
A domain must have only one SPF record. Publishing multiple TXT records containing SPF data can cause conflicts during evaluation and authentication failures. All sending sources should be combined into a single consolidated SPF record.
Not updating SPF records after switching email providers
When organizations migrate to new email platforms but keep outdated ‘include’ entries in the SPF record, unnecessary lookups and authentication problems can occur. Regular SPF reviews ensure that only active and authorized sending services remain listed.

Common DKIM configuration errors that cause failures
DKIM is designed to confirm that an email message has not been altered and that it truly comes from the claimed domain. However, even when DKIM is enabled, configuration mistakes can cause signatures to fail silently, leading to authentication issues and deliverability problems. Understanding the most common DKIM errors helps organizations maintain reliable email authentication.
Incorrect DKIM selector configuration
Each DKIM key is associated with a selector that tells receiving servers where to find the public key in DNS. If the selector used by the sending platform does not match the selector published in DNS, the verification process fails. This often happens when organizations change email providers or create new selectors without updating DNS records correctly.
Expired or rotated DKIM keys not updated in DNS
For security reasons, DKIM keys should be rotated periodically. Problems arise when the sending service starts using a new private key, but the corresponding public key is not updated in DNS. When the public and private keys do not match, DKIM verification fails for all outgoing emails from that service.

Email content modification breaking DKIM signatures
DKIM signatures are calculated based on specific parts of the email content. If an email is modified after signing, even small formatting changes introduced by forwarding systems, mailing lists, or security gateways can invalidate the signature. This can cause unexpected authentication failures even when the original configuration is correct.
Using weak or outdated DKIM key lengths
Short or outdated DKIM keys provide lower security and may not meet current mailbox provider recommendations. Using at least 1024-bit keys, and preferably 2048-bit keys, helps ensure both stronger protection and better compatibility with modern authentication standards.

DKIM signing not enabled for all sending services
Organizations often use multiple email platforms, including marketing tools, CRM systems, and support systems. If DKIM signing is enabled only for some of these services, emails from unsigned sources may fail authentication checks, resulting in inconsistent deliverability.
Best practices to prevent SPF and DKIM issues in 2026
Email authentication problems often do not appear suddenly. In most cases, they develop slowly as organizations add new email services, change vendors, or update systems without reviewing existing authentication settings. Following a few consistent best practices can help organizations avoid common SPF and DKIM failures and maintain stable email deliverability.
Maintain an inventory of all email-sending platforms
Many businesses use several platforms to send emails, such as marketing tools, CRM systems, ticketing platforms, and internal applications. Over time, some of these services may be forgotten or replaced, but their authentication settings may remain unchanged. Keeping an up-to-date list of all authorized sending platforms helps ensure that SPF records include all legitimate senders and that DKIM signing is properly configured across services.
Monitor authentication results regularly using DMARC reports
DMARC reports provide detailed insights into how receiving servers evaluate SPF and DKIM for incoming emails from your domain. Reviewing these reports regularly helps identify authentication failures, unauthorized sending sources, and configuration gaps before they begin affecting deliverability. Continuous monitoring enables organizations to resolve issues early rather than react after email performance declines.
Implement automated SPF optimization and record flattening
As organizations add more sending services, SPF records can become long and complex, sometimes exceeding the allowed DNS lookup limits. Automated SPF optimization tools help manage these records by flattening includes, removing unused entries, and keeping the configuration within technical limits. This reduces the risk of SPF failures caused by record complexity.
Rotate DKIM keys periodically and maintain key security
Regular DKIM key rotation is an important security practice. Replacing older keys with new ones helps reduce the risk of key exposure and strengthens domain protection. During rotation, it is important to update DNS records carefully and confirm that the sending service is using the correct private key. Proper documentation and scheduling make this process smooth and predictable.
Perform routine email authentication audits
Periodic audits help confirm that SPF, DKIM, and DMARC settings remain accurate as business systems evolve. These audits should include checking DNS records, verifying DKIM signing across all services, and validating authentication alignment. Routine reviews help organizations maintain strong authentication practices and avoid unexpected deliverability disruptions.
Final thoughts
SPF and DKIM authentication errors are often small configuration issues, but their impact on email deliverability and domain reputation can be significant. As mailbox providers continue to strengthen authentication enforcement in 2026, organizations can no longer rely on one-time setup. Continuous monitoring, regular updates, and clear visibility into all email-sending services are essential for maintaining reliable email performance.
By understanding common SPF and DKIM mistakes and following structured best practices such as record optimization, DKIM key rotation, and routine authentication audits, businesses can reduce the risk of delivery failures and domain spoofing. Strong authentication not only improves inbox placement but also protects customer trust and brand credibility. Taking a proactive approach today ensures that legitimate business communications continue to reach recipients safely and consistently in the evolving email security landscape.