Can You Have Multiple SPF Records?
The crux of the matter is that you cannot have multiple SPF records for a single domain. This is not merely a suggestion; it’s rooted in the technical specifications outlined in RFC 7208, which state unequivocally that only one SPF record should exist per domain. Straying from this guideline introduces a fatal error known as PermError, rendering all attempts at email verification fruitless and paving the way for delivery failures across the board.
Imagine trying to send letters from two different addresses simultaneously—confusion ensues for the postal service, just like it does for email servers when they encounter multiple SPF records.
The Consequences of Having Multiple SPF Records
When a domain contains more than one SPF record, email servers face a dilemma. They attempt to validate your email based on conflicting records but end up confused. This leads to authentication failures and might even trigger spam filters. The fallout? Your carefully composed emails could land in recipients’ junk folders or, worse, simply never reach them at all.
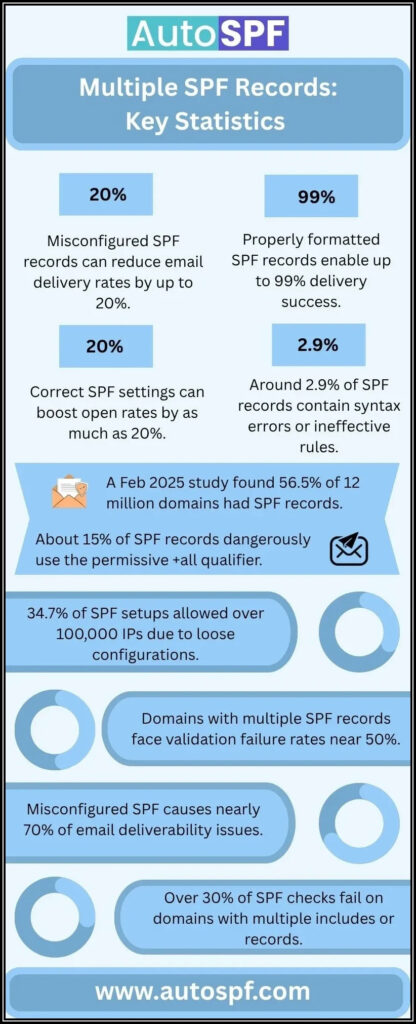
Statistically speaking, domains grappling with multiple SPF records experience validation failure rates approaching 50%. That’s alarming! For anyone managing a business or personal brand via email, this reality comes with significant implications for communication and reputation.
Finding Solutions
Instead of dual configurations, merging your entries into a single SPF record is essential. It’s straightforward: capture all necessary components in one tidy package. For example, rather than relying on separate declarations such as:
v=spf1 include:_spf.google.com -alland
v=spf1 include:servers.mcsv.net -allYou would combine them like this:
v=spf1 include:_spf.google.com include:servers.mcsv.net -allThis method secures functionality and maintains credibility by ensuring seamless delivery.

To reduce the risk of complications further, remember to consider your DNS lookups during this consolidation. Each lookup must stay under 10 total; exceeding this limit can similarly compromise email authentication.
Best Practices Moving Forward
To maintain pristine email deliverability and efficiency, keep these best practices in mind as you manage your SPF configurations:
- Use Include Statements: Rely on the “include” mechanism within your single SPF record to represent additional service providers while keeping your record size optimal.
- Regular Monitoring: Utilize tools tailored for SPF tracking and validation to alert you if any configuration issues emerge.
- Consult Resources: Employ merging tools found online to assist in streamlining complex SPF settings.
As you navigate through configuring your SPF records effectively, understanding the impact of these settings on email communication will prove vital in enhancing trust in your digital interactions.
Now that we’ve established the importance of proper record management, let’s explore how these configurations affect email delivery and overall performance.
Effects on Email Delivery
When it comes to email, every detail matters, and having multiple SPF records can significantly hurt your ability to get your messages into the inboxes they’re meant for. Many organizations experience drops in delivery rates due to misconfigured SPF settings. Imagine writing an important email and having it vanish into a black hole—this is what many businesses face because of conflicting SPF records.
Emails failing SPF checks are 70% more likely to end up in the spam folder or be rejected outright. The presence of multiple records sends a confusing signal to recipient servers, making them question which record should be trusted. This confusion ultimately leads to a denial of service where legitimate emails are mistaken for malicious attempts.
Consider this: If a company mistakenly includes separate SPF records like ‘v=spf1 include:_spf.google.com -all’ and ‘v=spf1 include:spf.mailgun.org -all,’ the inconsistency will trigger an authentication failure. When recipient servers encounter such conflicts, they may respond by blocking critical communications or relegating them to junk mail—a situation no one wants to experience.
The ramifications extend to your email reputation as well. Repeated delivery failures lead to increased bounce rates, further damaging the credibility of your sending domain. Studies show that domains with properly configured SPF records enjoy a 99% success rate in email delivery compared to those without. Conversely, having multiple SPF records can drop delivery rates by **up to 20%**—a stat that’s hard to overlook.
Organizations with multiple SPF records report a notable increase in phishing attacks, as attackers take advantage of the confusion in email authentication. Ensuring that you have only one consolidated SPF record is not just a best practice; it’s essential for maintaining email integrity and security.
To mitigate these risks, always check your SPF configuration regularly. Monitoring tools can help automate this process; for instance, DMARCLY offers alerts when multiple records are detected, allowing organizations to address issues before they escalate into delivery disasters. Remember, the key is simplicity—a single, well-defined SPF record can save you from a myriad of problems and ensure your emails reach their destinations reliably and securely.
The consequences of misconfigured records are far-reaching, affecting both deliverability and security aspects of emails. We should next explore how these configurations introduce vulnerabilities that could jeopardize your trust and safety in digital communications.
Security Concerns with Multiple SPF Records
From a security perspective, managing your system’s SPF records is not just about compliance; it’s about protecting your organization from dangers like spoofing and phishing attacks. Each time an email is sent from your domain, mail servers reference your SPF record to determine its legitimacy. If there are multiple SPF records, things can become chaotic. These inconsistencies introduce vulnerabilities that attackers exploit.
Imagine you have successfully established a reputation associated with your domain. Now, envision an attacker who knows about this trust. They can send fraudulent emails posing as communications from your organization, attempting to gain sensitive information or spread malware. When this malicious email lands in a recipient’s inbox, their server checks the SPF records. If it encounters conflicting records during verification, the authentication fails—raising red flags. Legitimate users might receive warnings or even miss important communications because they can’t differentiate between genuine messages and impostors.
Maintaining clarity within your SPF configuration is paramount in combating these threats.
Simplifying and consolidating your SPF records reduces the chances of ambiguous situations. A single, clear record delineating all authorized mail servers is crucial; not only does it streamline the authentication process but it ensures credibility throughout your email communications. By merging multiple entries into one comprehensive record, you reduce ambiguity while reinforcing your organization’s stance against potential fraud. This strengthens trust with clients and partners alike and lowers the risk of being used as a conduit for spam or phishing schemes.
Keeping track of SPF settings is not merely a technical task but a necessity for fortifying your domain’s overall security posture. Regular audits and updates are essential to ensure seamless integration of any new email services without duplicating entries that might lead to attacks. Prioritizing monitoring tools like DMARCLY can substantially enhance your vigilance in spotting inconsistencies before they develop into significant problems.
A proactive approach to managing SPF records lays the foundation for safeguarding your digital assets. With every element in order, you strengthen both email deliverability and secure communication practices.
Efficient SPF Configuration Alternatives
One effective strategy for managing SPF records is to utilize the include mechanism, which allows you to consolidate multiple entries into a single record. This is particularly useful if you use various third-party services for sending emails. For example, if you rely on Google and Mailgun for different communication needs, merging their SPF configurations saves you from potential pitfalls associated with maintaining separate records.
“A streamlined SPF record not only aids compliance with standards but also enhances deliverability rates.”

So, how do you achieve this consolidation? First and foremost, you’ll want to identify all authorized servers. Making a complete list helps avoid omissions and ensures your communications flow smoothly. This might include your web hosting provider, email marketing platforms, or any other service that sends emails on your behalf.
Identify Authorized Servers
- Make an inventory of all the platforms you utilize for sending emails.
- Include any applications that may send automated responses or newsletters.
- Don’t forget to factor in subdomains if they operate under different services.
Once you’ve compiled this list, it’s time to consolidate these entries into what will be your sole SPF record. For example, instead of having separate lines like “v=spf1 include:_spf.google.com” and “v=spf1 include:spf.mailgun.org,” combine them neatly into one record: ‘v=spf1 include:_spf.google.com include:spf.mailgun.org -all’. This approach keeps things tidy and eliminates confusion within DNS settings.
Consolidate into One Record
After merging everything together, it’s crucial to validate the record. Think of this as the final check before an important presentation; ensuring that your SPF syntax is correct is vital for preventing delivery failures. There are numerous online tools available, such as MXToolbox or Kitterman’s SPF validator, to help ensure everything looks perfect before implementation.
Monitoring your SPF records regularly following these changes is equally important. Email providers often update their systems, which might affect how your SPF records function over time. A little diligence here will save you frustration down the line.
Validate the Record
Regular audits of your email authentication strategy can catch issues early before they escalate into significant problems.
By implementing these configuration strategies effectively, you can enhance both the security and performance of your email communications while maintaining a proactive approach to email management. Let’s now look at some frequent errors that can occur during configuration that could jeopardize your efforts.
Common Configuration Mistakes
One of the first mistakes many domain owners make is succumbing to syntax errors. These simple typographical errors can lead to an invalid SPF record, rendering the whole setup ineffective. For example, improper use of colons or forgetting quotation marks can cause issues that block legitimate emails. It might seem trivial, but these minor details are significant in the world of email authentication—something as small as a misplaced space can lead to big problems.
Another frequent oversight comes from misunderstanding the limitations set by SPF specifications.

When it comes to DNS lookups, domains must not exceed ten total lookups specified in their SPF records. This total includes all include mechanisms, A records, and MX records. If you go beyond this limit, authentication will fail, which means your emails may end up in spam folders or be rejected entirely. Imagine sending out important emails only to find they never reached their destination simply because you overlooked something so fundamentally routine.
Yet another area where many struggle is with incorrect modifiers, particularly the use of “all.”
Misusing modifiers within an SPF record can lead to unintended consequences that jeopardize your email deliverability. For example, if you incorrectly place the “all” modifier in the wrong position within your syntax, it could inadvertently allow unauthorized servers to send emails on behalf of your domain. The best practice dictates that this modifier should appear at the end of the record to clarify exactly which senders are acceptable.
Being mindful of these common oversights is a vital step towards ensuring your domain’s email security.
Moreover, consider implementing a consistent review process for your SPF records. Regularly monitoring your configurations can help identify potential mistakes before they affect your email communications. Using tools like DMARCLY’s monitoring feature can aid in keeping tabs on your SPF settings, alerting you if issues arise due to misconfigurations or syntactical errors. Taking charge of your domain’s SPF management through vigilance can significantly simplify the complexities associated with email authentication and contribute to holistic email security for yourself and your clients.
As we further explore effective ways to maintain optimal configurations, understanding proper management techniques becomes paramount.
Best Practices for SPF Management
Managing SPF records effectively involves a few straightforward yet significant practices. One key guideline is the Single Record Rule, which means always ensuring that each domain has only one SPF record. This is critical because having multiple SPF records leads to confusion during verification processes and can cause email delivery failures.

When your recipients’ mail servers look up your domain’s SPF records, they might receive multiple conflicting answers, resulting in a failed authentication called PermError. To avoid such pitfalls, consolidate any existing SPF records into a single, comprehensive entry that includes all necessary permissions for email sending sources.
Beyond just creating a singular record, another vital step is ensuring Regular Monitoring of your SPF configuration.
Automating this process with tools designed for this purpose can save you time and reduce the risk of misconfigurations going unnoticed. For example, DMARCLY offers monitoring services that alert users whenever multiple SPF records are detected within a domain. Regular checks allow you to stay ahead of potential issues, whether someone has inadvertently added a conflicting record or if changes in email-sending services require adjustments to your configurations.
Additionally, coupling your SPF practices with DMARC Implementation significantly strengthens your domain’s overall security posture.
DMARC (Domain-based Message Authentication, Reporting & Conformance) provides a framework for aligning SPF and DKIM (DomainKeys Identified Mail), creating an additional layer of protection against email spoofing. By implementing DMARC, you gain insights through reports about how your emails are being treated by other servers, providing valuable data on delivery rates and any fraudulent use of your domain. The combined implementation of SPF and DKIM under the DMARC policy not only boosts trust in your emails but also enhances their deliverability.
Adopting these best practices isn’t merely about following a checklist; it’s about nurturing the relationship between your domain and its reputation in the digital realm. As you manage your SPF records with precision and vigilance, you’ll likely see improved email deliverability rates along with stronger defenses against malicious activities targeting your domain.





