Most large-scale businesses own multiple domains and subdomains, which are heavily used for sending emails. A multi-domain environment is more prone to email-based cyber threats. In fact, in a recent attack, malicious actors compromised more than 8,000 subdomains of top brands and institutions, including MSN, VMware, McAfee, The Economist, eBay, etc.
While using multiple domains and subdomains helps organize communication channels, it challenges SPF management. Let’s see how.
SPF management challenges in a multi-domain environment
These complexities emerge and multiply as the number of domains grows. Here is a rundown of what to expect-
Reaching the DNS lookup limit

There is a limit of a maximum of 10 DNS lookups to minimize the risk of a DDoS attack and not to overburden the resources involved in the process of DNS lookup. However, in a multi-domain environment, this limit is exhausted quickly, triggering SPF checks to fail and causing legitimate emails to undergo false positives.
Consistency and maintenance
If multiple domains are involved, it becomes your responsibility to ensure changes in the list of authorized sender servers are reflected across all domains. This practice induces more chances of human errors or outdated SPF records.
Delegated services
Organizations often use various third-party services (e.g., cloud-based email providers and marketing automation tools) that require SPF records to include their servers. In a multi-domain environment, each service might need to be integrated into the SPF records of multiple domains, further complicating the setup and increasing the risk of misconfigurations.
Interdependencies between domain
For most organizations, it’s common practice to have domains that are interdependent for email operations. For example, an email may be sent from support.domain.com, but it uses servers linked to domain.com.
These interdependencies trigger unintended conflicts between policies, leading to false positives or negatives; neither of which are in your favor.
Subdomain management
Subdomains in a multi-domain environment may inherit the SPF policy of their parent domain or have distinct policies. Managing SPF for a large number of subdomains can be cumbersome, especially when different subdomains have different requirements.
Strategies and best practices
While you can’t refrain from using a multi-domain environment for smooth and organized operations, there are some solutions to handle the complexities. By following these best practices, you can ward off grave phishing and spoofing attacks.
Centralized management of DNS records
Have a centralized DNS management system and use automation tools to ensure that any changes you make are implied across SPF records. Without tools, human errors, non-uniformities, and inconsistencies are possible.
Handling third-party services
We suggest you opt for third-party service providers who prioritize SPF deployment and optimization. Ask them about their SPF configurations and understand how their settings can impact your DNS lookup limits. If necessary, both parties should be willing to adjust their SPF records in accordance with each other.
Subdomain and cross-domain interdependencies
Often, domain owners forget about defining policies of subdomains, and that leads to conflicts of all kinds. So, ensure all subdomains have tailored SPF records if that’s needed. It’s not always a good practice to inherit the parent domain’s policy by default.
Also, if cross-domain sending is absolutely necessary for your operations, mindfully structure your SPF records and make reasonable use of ‘include’ statements.
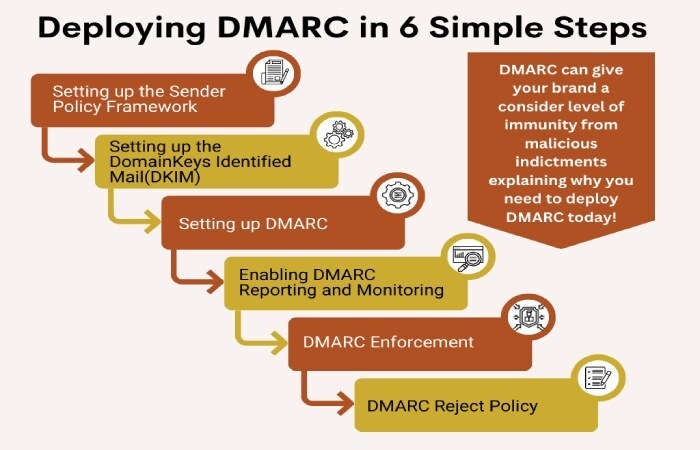
DMARC deployment
Consider implementing fallback mechanisms such as DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting & Conformance) alongside SPF. This provides an additional layer of authentication and helps mitigate issues if an SPF failure occurs.
If you deploy DKIM, then it will help recipients’ servers verify if anyone tampered with the content of an email sent from your domain while it was in transit. This is done using cryptography-based public and private keys.
Talking about DMARC, then it’s the latest email authentication mechanism that is built on SPF and DKIM. It allows domain owners to specify how recipients’ mail servers should deal with illegitimate emails sent from their domain.
DMARC also comes with a very useful reporting feature that gives domain owners or administrators visibility into SPF alignment issues (along with DKIM and DMARC issues) across your domains.
But if you plan to make the best use of the DMARC reporting mechanism, the SPF ‘return path’ domain should be the same as the ‘From’ domain or align with the organizational domain specified in DMARC.
Minimizing DNS lookups
Where possible, consolidate the IP addresses and ranges used by different services. Instead of including multiple include statements in your SPF record, you can directly list the IP addresses or ranges.
If your SPF record still exceeds the DNS lookup limit of 10, use our automatic SPF flattening tool that resolves all ‘include’ statements and directly lists the resolved IP address. Staying within the limits is important for keeping your record valid.
For more information related to SPF flattening, contact us.





