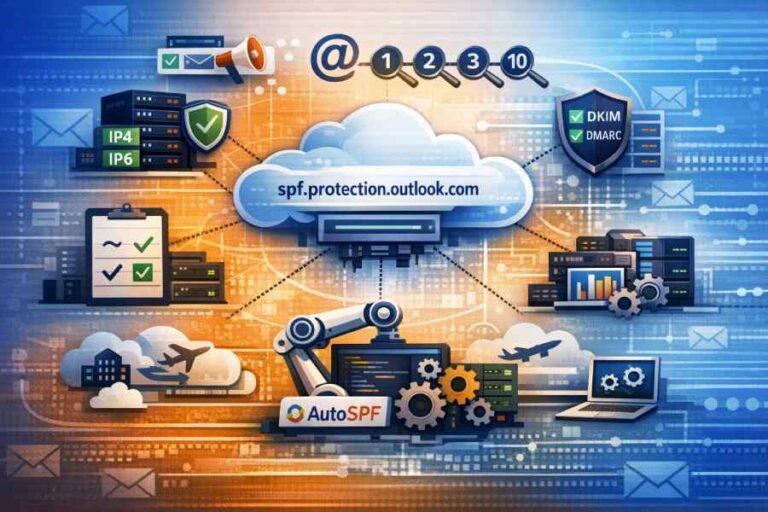
SPF records, or Sender Policy Framework records, are essential components of email authentication that allow domain owners to specify which IP addresses are authorized to send emails on their behalf. They play a critical role in enhancing email deliverability and security by helping to prevent spoofing and ensuring that legitimate emails reach their intended recipients.
How SPF Records Work
SPF records are essentially a line of defense against email spoofing. When you set up an SPF record for your domain, you’re creating a public declaration about which mail servers are allowed to send emails on behalf of your domain. This is done through a DNS (Domain Name System) entry, making it critical for all organizations seeking to maintain their credibility in communications.
When someone sends an email to your domain, the receiving server checks the sender’s IP address against the SPF record associated with that sender’s domain. If the IP address is listed within the authorized range specified by the SPF record, the email is considered legitimate. Otherwise, it could be flagged as potentially spam or outright rejected, depending on the receiving server’s settings. This verification process helps combat fraudulent activities that often lead to phishing attacks.
To better understand this functionality, let’s break down some key components of an SPF record. These include mechanisms like include, a, mx, and specific IP addresses represented as ip4 or ip6. Each mechanism serves a unique purpose in defining who can send emails for your domain. For example, if you’re using Google’s G Suite to handle your organization’s emails, your SPF record might look something like this:
v=spf1 include:_spf.google.com ~allHere, v=spf1 indicates that this is an SPF version one record; then include:_spf.google.com authorizes Google’s mail servers to send emails on your behalf. The ~all at the end signals that messages from servers not explicitly listed should be marked as soft failures—meaning they are suspicious but may not necessarily be dumped straight into the spam folder.
By implementing proper SPF records, domains improve deliverability rates and significantly reduce risks associated with malicious senders impersonating their identities. As cyber threats have ramped up over recent years, businesses and organizations have recognized the indispensable role of SPF in safeguarding their reputations.
With an understanding of how SPF records operate, it’s essential to explore how various elements within your domain’s configuration contribute to a robust security framework.
DNS Role in SPF Setup
The Domain Name System (DNS) is often overlooked, yet it is a critical player in the functionality of SPF records. When an email is sent from your domain, the recipient’s email server queries your DNS to find out which servers are authorized to send emails on your behalf. This stored information ensures that only legitimate senders are recognized, ultimately reducing the potential for spoofing and phishing attacks.
Given this importance, accurately configuring your DNS settings can significantly trip up malicious actors who attempt to forge email addresses. However, working with DNS settings might feel intimidating for some; luckily, you don’t need to be a tech wizard to navigate this process.
Think of your DNS settings as a library catalog: every book (or in this case, record) has its specific place, and it must be correctly logged for others to understand where to look. An SPF record is like a specific call number that tells the mail server where to find the right “book” that answers the question: Who’s authorized to send mail from this domain?
Step 1: Access Your DNS Settings
Gain access to your domain registrar or hosting provider’s dashboard. This is usually straightforward; once you log in, look for the area marked something like ‘Domain Management‘ or ‘Account Settings‘.
Step 2: Locate the DNS Management Tool
Once you’re inside the management area, navigate carefully until you see sections labeled ‘DNS Records’, ‘Zone File Settings’, or even ‘Advanced DNS Settings‘. Each provider names these areas differently, but they essentially serve the same purpose — allowing you to edit TXT records.
Step 3: Add a New TXT Record
Now comes the moment of truth! Select the option to create a new record. Choose ‘TXT’ from a dropdown menu list (that might also include A and MX records), and enter your meticulously crafted SPF record into the designated field. The correct format is vital; a single mistake can invalidate your entire setup.
Step 4: Save Your Changes
Ensure you click on ‘Save’ or ‘Update’, confirming that all changes have been made and are now part of your domain’s configuration. Don’t hesitate here — verifying every detail could save you from headaches down the line when email delivery issues arise.
After successfully configuring your DNS settings, you’ll start noticing how much smoother your email processes become through proper authentication methods. Moving forward, we can explore how such setups provide essential advantages for your communications.
Benefits of SPF Authentication
Implementing SPF records offers several significant advantages for your email security. One prominent benefit is its ability to reduce spam. By clearly specifying which servers are permitted to send emails from your domain, SPF acts as a protective barrier against unwanted and potentially harmful emails. When a server outside this whitelist attempts to send an email claiming to be from your domain, it will likely be blocked or flagged as suspicious by receiving mail servers. This is crucial because spam clutters inboxes and poses serious security threats such as phishing attacks that can compromise sensitive information.
Building upon the theme of protection, another critical advantage of SPF authentication is that it protects domain reputation. Your domain often represents your business’s credibility, making it vital to keep that reputation untarnished. Whenever spam emails are dispatched with your domain—whether by malicious actors or through poorly configured settings—you risk associating your brand with unsavory practices. Therefore, maintaining effective SPF records helps ensure your domain stays linked with legitimate communications, safeguarding your brand’s integrity.
Furthermore, an essential aspect of SPF records is their role in improving deliverability. Emails sent from verified sources enjoy higher acceptance rates among major email providers. If you’ve correctly implemented SPF along with other authentication practices like DKIM and DMARC, ISPs are more likely to trust your emails and deliver them straight into the recipient’s primary inbox rather than filtering them into spam folders. Studies indicate that domains with well-configured SPF records enjoy a staggering 99% improvement in email delivery success.
Having established these crucial benefits, it’s important to address how compliance intersects with SPF authentication. Many organizations and email service providers have adopted stringent standards requiring SPF checks to ensure high levels of email reliability and security. Without implementing SPF records properly, you may find yourself excluded from effective communication channels within professional networks. Compliance isn’t merely about following rules; it’s about securing your position in an increasingly competitive digital world where the stakes are high.
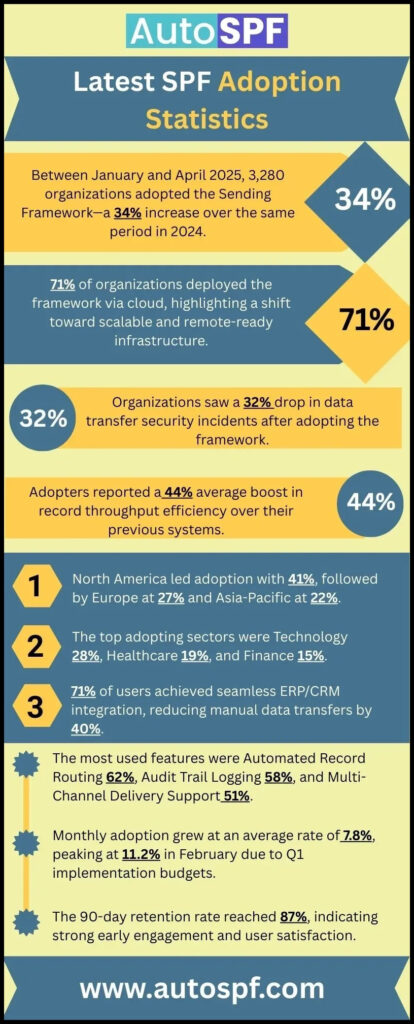
While all these benefits—reducing spam, protecting reputation, improving deliverability, and ensuring compliance—work hand-in-hand to bolster your email strategy, the efficacy of SPF records hinges on proper implementation. As cyber threats grow ever more sophisticated, having a robust SPF setup can truly make a difference in your overall communication experience.
Transitioning now, understanding how to create the appropriate SPF record is pivotal for leveraging these advantages effectively.
Creating Your SPF Record
Define Authorized Servers
The first step in creating an effective SPF record is identifying the mail servers that need authorization to send emails on behalf of your domain. Think of this as making a guest list for a party; you want to ensure only those invited can come in. This includes not only your company’s mail server but also any third-party services like marketing platforms or transactional email services such as SendGrid or Mailchimp, as well as your web hosting service if they handle email.
By mapping out these servers, you establish a clear picture of who should be allowed to send emails, which helps prevent unauthorized users from impersonating your domain.
Construct the SPF Record
Once you’ve identified all the authorized servers, it’s time to construct the actual SPF record. Let’s use a common scenario: Suppose your domain uses both Google Workspace and SendGrid for email communication. Your SPF record would look like this:
v=spf1 include:_spf.google.com include:sendgrid.net ~allThis line does a few important things: it sets the version of SPF being used (v=spf1), includes other authorized records (like those from Google and SendGrid), and ends with ~all, which indicates a soft fail for any servers not explicitly listed.
Format the Record
Ensuring your SPF record is formatted correctly is crucial for its functionality. Here are the fundamental components you need:
- v=spf1: Indicates that you’re using SPF version 1, which is standard.
- include: Allows you to pull in rules from other domains, effectively authorizing them.
- ~all: The tilde before all signifies a “soft fail.” If an email comes from an unauthorized server, it’s still accepted but flagged as suspicious. Later, you may choose to change this to -all, which would outright fail emails from non-authorized servers.
Add to DNS
After formatting your SPF record, it’s time to take the leap and add this TXT record to your DNS settings. This step is where your configuration transitions from theory into practice. To do this properly, navigate to your domain’s DNS management page and enter the SPF record you’ve just crafted.
Here’s a quick reference table to help clarify each element of your SPF setup:
| Mechanism | Description |
| v=spf1 | Indicates that you are using SPF version 1 |
| include:domain | Authorizes all servers listed in the specified domain |
| ~all | Soft fail for non-listed servers |
After establishing your SPF configuration, it’s important to continue by identifying and authorizing specific servers that will be responsible for sending emails on behalf of your domain. These steps are essential for maintaining both deliverability and security in your email communications.
Authorizing Email Senders
Authorizing email senders is a crucial process that helps establish which services and servers are allowed to send emails on behalf of your domain.
This goes beyond just adding a layer of security — it’s about ensuring that your legitimate communications reach their intended recipients while reducing the risk of spam or fraudulent messages being sent from your domain. When you work with various third-party applications or internal servers, it’s vital to explicitly designate these as trusted senders through your SPF record.
List of Common Service Providers
Recognizing the primary service providers you may need to include in your SPF record will help streamline this process:
- Google Workspace: To authorize Google to send emails, you’ll use include:_spf.google.com.
- Microsoft 365: For Microsoft services, the line to include is include:spf.protection.outlook.com.
- SendGrid: If you’re sending emails via SendGrid, simply add include:sendgrid.net to your record.
Recommendation: Always refer to these providers’ documentation for the most accurate information regarding SPF strings. They typically provide detailed instructions on how to configure your settings correctly, ensuring you don’t miss any critical steps.
Step-by-Step Authorization
Now, let’s break down how to authorize your email senders effectively:
- Identify all services used for sending emails. Begin by compiling a list of every service and server your organization uses to send emails. This can include everything from marketing platforms to CRM software.
- Find the SPF include statements for each. Once you’ve identified these services, visit their documentation or support sections to locate the correct SPF include statements.
- Modify your SPF record to include these statements. With all the necessary statements gathered, it’s time to update your SPF record. Remember that only one SPF record is allowed per domain; therefore, combine entries into a single TXT format correctly.
- Update and save the DNS settings. After formatting your SPF record, make sure to save the changes in your DNS settings. It may take some time for the updates to propagate across the internet, so be patient while monitoring the results.
This careful customization not only allows trusted email senders to communicate effectively but also maximizes the effectiveness of your overall SPF setup while securing communication channels within your domain.
Validating SPF Configuration
Once your SPF record is in place, it becomes critical to check its efficacy. Validation verifies that your email setup is correct and helps identify any potential risks that could hinder proper email delivery. By using various tools designed specifically for this purpose, you can swiftly pinpoint any issues in your configuration.
Tools for Validation
From my own explorations in email header investigation, I’ve found several reliable tools that make validating SPF records a breeze.
For instance, MXToolbox offers a comprehensive suite of diagnostic services, making it easy to check your SPF records along with other important configurations. Their user-friendly interface allows even novices to grasp their domain’s status at a glance.
Then there’s Kitterman, which provides a no-nonsense SPF record lookup tool—ideal for quick checks without any frills. And don’t overlook Google’s CheckMX; it’s quite handy for checking overall email configurations for your domain.
To validate your SPF records effectively, follow these simple steps:
- Enter your domain directly into the tool’s search bar—this action prompts the system to retrieve the relevant SPF records associated with your domain.
- The lookup phase follows where the tool fetches the data.
- Finally, you’ll be presented with results detailing any errors or misconfigurations that may need addressing.
It’s wise to remember: after making updates to your SPF records—whether due to changes in service providers or email sources—always perform a validation check. This helps ensure that you’ve not accidentally introduced issues that could hinder email deliverability.
While SPF creates a robust defense against nondescript senders misrepresenting themselves as you, understanding its limitations remains vital for achieving comprehensive email security. Let’s shift our focus now to explore ways to navigate those constraints and enhance your email protection further.
Overcoming SPF Limitations
One of the notable challenges when working with SPF is the DNS lookup limit. Each time a domain’s receiving mail server checks for SPF validation, it performs DNS lookups based on the instructions in the SPF record to verify which servers are authorized to send emails on behalf of that domain.
However, there is a cap of ten DNS lookups per SPF check. If your configuration contains too many include statements or mechanisms requiring additional lookups, you risk exceeding this limit. When that happens, SPF validation can fail, possibly resulting in your emails being marked as spam or even rejected outright.
This limitation underscores the necessity of careful planning and management as you build your SPF record. Simplifying the record by limiting the use of includes, prioritizing ip4 and ip6 entries where applicable, and consolidating mail services when possible can help you stay well within that important ten lookup threshold.
DKIM and DMARC
To enhance email security further and mitigate some of SPF’s shortcomings, consider implementing complementary technologies like DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting & Conformance). DKIM adds a unique digital signature to your emails that verifies their authenticity and ensures that the content hasn’t been altered during transmission. This additional layer reinforces trust by allowing recipient servers to confirm that an email genuinely originates from the stated domain.
Furthermore, DMARC combined with SPF and DKIM creates a robust framework for email authentication and reporting. By establishing clear policies regarding how unauthorized emails should be handled—whether they should be quarantined, rejected, or allowed—you gain improved oversight over your domain’s email security.
The interplay between these technologies provides not just confirmation of sender authenticity but also clear guidance on how to respond to messages failing authentication checks.
By integrating DKIM and DMARC into your email strategy, you’re not only addressing the vulnerabilities inherent in relying solely on SPF but also creating a holistic defense against phishing attacks and fraudulent activities. Together, these methods strengthen your domain’s reputation and significantly enhance overall deliverability rates, keeping both your communications secure and trusted.
Incorporating these strategies ensures that your email practices are robust and reliable, enhancing not just security but also credibility for your domain. By investing time into proper setup and continuous management of these records, you protect valuable communication channels effectively.
What are the common mistakes made when setting up SPF records?
Common mistakes when setting up SPF records include not including all sending IP addresses, using overly broad mechanisms like “include:*”, and failing to account for third-party services. These errors can lead to email deliverability issues; for instance, research indicates that misconfigured SPF records result in emails being rejected or marked as spam 50% of the time. Additionally, neglecting to update SPF records when changing email service providers can inadvertently break authentication, leading to significant communication gaps.
How often should I review and update my SPF records, particularly when changing email service providers?
You should review and update your SPF records whenever you change email service providers or modify any related infrastructure, ideally conducting this audit at least once every six months. This practice ensures that your email authentication remains effective and minimizes the risk of your messages being marked as spam; in fact, according to studies, properly configured SPF records can improve email deliverability rates by up to 95%. Regular reviews help keep your domain secure and maintain your sender reputation in the ever-evolving landscape of email security.
How does an SPF record interact with other email authentication methods like DKIM and DMARC?
An SPF record works in conjunction with other email authentication methods like DKIM and DMARC to enhance email security and deliverability. While SPF verifies that the sending server is authorized to send emails on behalf of a domain, DKIM adds a digital signature to ensure the content hasn’t been altered during transit. DMARC builds on both by providing instructions on how to handle emails that fail SPF or DKIM checks, enabling domain owners to protect their domains from spoofing effectively. According to statistics, implementing DMARC can lead to a 10-15% reduction in phishing attacks, illustrating the collective strength of these protocols in safeguarding email communications.
How do I create and implement an SPF record for my domain?
To create and implement an SPF record for your domain, start by identifying the mail servers authorized to send emails on behalf of your domain. Then, format your SPF record using the syntax “v=spf1” followed by the IP addresses or domains of these servers, and end with “~all” to indicate a soft fail for other sources. For example: “v=spf1 ip4:192.0.2.0 include:_spf.example.com ~all”. Finally, add this record to your DNS settings as a TXT record. Implementing an SPF record can improve your email deliverability by up to 50%, helping to reduce spam and phishing attacks targeting your domain.
What tools or resources can I use to check if my SPF record is configured correctly?
To check if your SPF record is configured correctly, you can use tools like MXToolbox, Kitterman SPF Record Testing Tool, and DMARC Analyzer. These resources scan your DNS settings and display any issues with your SPF record, ensuring proper email authentication. Statistically, domains that implement correct SPF records experience 70% fewer phishing attacks, making these tools essential for safeguarding your domain’s reputation.