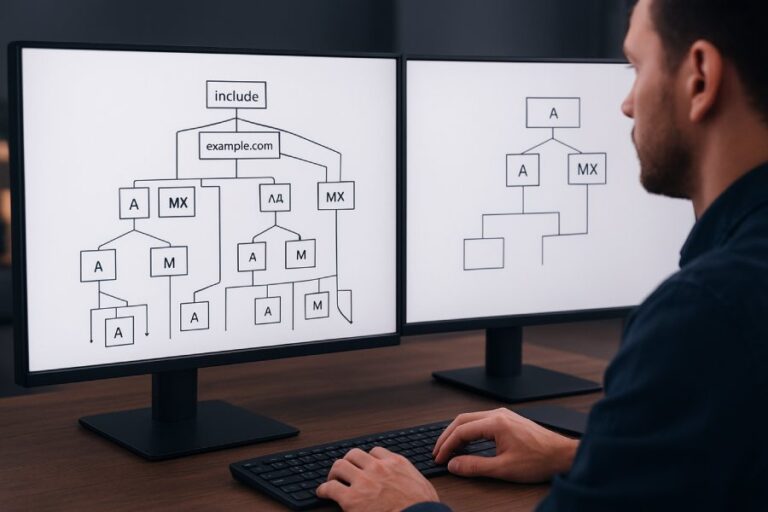
Sender Policy Framework (SPF) is a vital component of modern email security, designed to help protect organizations against email spoofing and phishing attacks. As part of email authentication, SPF allows domain owners to specify which Mail Transfer Agents (MTAs) are authorized to send emails on behalf of their domain. This is accomplished through the publication of SPF records in DNS TXT records, which are then retrieved by receiving email servers during SPF evaluation.
SPF operates by performing an SPF record lookup for the sender’s domain based on the information found in the email headers. These records include mechanisms—such as `ip4`, `ip6`, `a`, `mx`, `ptr`—and modifiers, which collectively define allowed sending sources. When an email arrives, the recipient’s mail server conducts an SPF validation by querying DNS for the domain’s SPF record, checking whether the sending IP matches any authorized IPs in that record.
SPF, alongside Domain-based Message Authentication, Reporting & Conformance (DMARC) and DomainKeys Identified Mail (DKIM), forms a triad of email authentication standards that enhance email security, improve email deliverability, and aid in phishing prevention. Proper SPF validation reduces the likelihood of spam filtering systems blocking legitimate emails and maintains the sender domain’s reputation.
What Causes SPF Sender Invalid Errors?
SPF sender invalid errors occur when the SPF validation process fails due to various reasons. In technical terms, these errors generally manifest as SPF fail, SPF permerror, SPF neutral, SPF softfail, or SPF hardfail results in the SPF evaluation.
Common causes include:
- SPF record misconfiguration: Due to the complexity in SPF syntax and mechanisms, domains often encounter SPF syntax errors or include incorrect IP ranges, resulting in permerror responses. These errors prevent the SPF check from completing successfully.
- Exceeding SPF record limit: The SPF record limit restricts the number of DNS lookups to 10 per SPF evaluation. If mechanisms like `include`, `a`, and `mx` result in excessive lookups, the lookup count may surpass this threshold, causing SPF permerror and triggering invalid sender errors.
- SPF DNS propagation delays: After publishing or updating SPF records, DNS propagation delays can cause receiving servers to access stale or incomplete SPF data, leading to SPF validation failures.
- Inaccurate sender domain verification: Emails sent through third-party services like SendGrid, Mimecast, or Google Workspace, without proper SPF record publishing for those services, trigger SPF hardfail or softfail outcomes.
- Missing or malformed SPF records: An absent SPF record defaults to an SPF neutral or fail outcome. Malformed records, often due to syntax errors or improper use of SPF macro expansion, can also lead to permerror statuses.
- Reverse DNS lookup issues: Some MTAs and spam filtering services, such as Barracuda Networks or Proofpoint, perform reverse DNS lookups to cross-check sender IPs against domain names. Inconsistent or misconfigured PTR records in DNS can cause validation problems, contributing to SPF sender invalid errors.

Common Symptoms and Consequenc
es of SPF Sender Invalid Errors
When SPF sender invalid errors occur, organizations often notice several symptoms directly impacting their email operations and security posture:
- Increased email bounce rates and delivery failures: Mail servers relying on SPF validation may reject or quarantine emails from domains with invalid SPF records. This results in reduced email deliverability and can harm business communication workflows.
- Emails flagged as spam or phishing: Spam filtering systems operated by vendors like Cisco, Return Path, ValiMail, or Microsoft Exchange interpret SPF fail, softfail, or neutral states as signals of potential threats, lowering the sender domain’s reputation and increasing the chances of emails landing in spam folders.
- SPF error logging entries: Detailed SPF troubleshooting involves reviewing SPF error logs, which frequently reveal permissions denied, lookup limits exceeded, or SPF permerror issues, helping diagnose invalid sender errors.
- Compromised sender domain reputation: Consistent SPF failures negatively impact sender domain credibility, which can propagate to other email authentication schemes like DMARC and DKIM, further damaging email security.
- Exposure to email spoofing and phishing: Failure in sender domain verification due to invalid SPF records enables attackers to send fraudulent emails impersonating legitimate domains, undermining phishing prevention measures.
How to Diagnose and Troubleshoot SPF Sender Invalid Errors
Effective SPF troubleshooting involves several systematic steps leveraging specialized tools and knowledge of SPF mechanisms:
- SPF record lookup and syntax validation: Use online tools provided by the OpenSPF Project or services integrated into Mimecast and ValiMail to perform real-time SPF record lookups and validate SPF syntax. This helps identify SPF syntax errors or policy conflicts.
- Check for SPF record publishing and DNS consistency: Confirm SPF records are correctly published in DNS TXT records through various DNS diagnostic tools. Verify SPF DNS propagation has completed globally, as a delayed propagation can cause intermittent SPF failures.
- Examine SPF record limit usage: Analyze the number of DNS lookups involved in SPF evaluation using SPF record parsing tools or services like Barracuda Networks’ diagnostic suites. Optimizing SPF mechanisms to reduce excessive includes or redirections prevents reaching DNS lookup limits.
- Review Email headers for SPF alignment: Inspect received email headers for SPF evaluation results reported by the MTA, such as Google Workspace or Microsoft Exchange. Proper SPF alignment, where the “Return-Path” domain matches the “From” domain, is crucial for consistent sender domain verification.
- Perform reverse DNS lookup checks: Ensure that your sending MTAs’ IP addresses are mapped to valid PTR records and that these align with SPF expectations. This is especially important when managing your own mailflow infrastructure or interfacing with third-party senders like SendGrid.
- Enable SPF error logging on your mail servers: Configure SPF error logging features available on platforms like Microsoft Exchange or Cisco email security appliances to capture detailed information about SPF failures, aiding deeper diagnosis.
- Coordinate with third-party senders: When using external emailing platforms such as SendGrid or Proofpoint, verify that their sending IPs are included in your SPF records and that SPF macro expansion is properly handled to cover these sources.

Best Practices to Prevent SPF Sender Invalid Errors in Your Email Infrastructure
To maintain robust email authentication and avoid SPF sender invalid errors, enterprises should implement the following best practices:
- Accurate SPF record publishing: Regularly audit your DNS TXT records to ensure SPF records are syntactically correct and accurately reflect your authorized sending MTAs, including third-party services.
- Optimize SPF mechanisms and modifiers: Use mechanisms like `include` judiciously and employ SPF modifiers like `exp` for enhanced error reporting in SPF evaluations.
- Monitor SPF record limit compliance: Stay within the 10 DNS lookup limit by minimizing complex nested includes and using consolidated IP ranges where feasible.
- Enable and enforce DMARC and DKIM: Complement SPF with DKIM signatures and a properly configured DMARC policy to reinforce sender domain verification and reduce the scope for spoofing.
- Use reliable email security providers: Leverage solutions from industry leaders such as ValiMail, Mimecast, Barracuda Networks, or Cisco, which not only support SPF validation but also provide comprehensive spam filtering and phishing prevention functionalities.
- Implement rigorous monitoring and logging: Continuously monitor SPF evaluation outcomes and error logs to swiftly detect and address SPF issues before they impact email deliverability or security.
- Conduct SPF DNS propagation checks after publishing changes: Use tools and services to verify global DNS propagation to avoid transient SPF validation errors.
- Educate administrators and developers about SPF macro expansion and syntax: Training around SPF record creation, including macro expansion and avoiding common syntax pitfalls, reduces misconfiguration risks.
- Coordinate SPF record strategies across platforms: When managing multi-vendor environments like Google Workspace, Microsoft Exchange, and SendGrid, maintain a unified SPF policy that accounts for all mail sources.
By adhering to these practices, organizations can reduce the risk of SPF sender invalid errors, bolstering their email authentication framework, safeguarding their email sender reputation, and enhancing overall email security.
Tools and Resources for SPF Diagnosis and Testing
Utilizing specialized SPF testing tools and resources is essential for effective SPF troubleshooting and ongoing email security maintenance:
- SPF Testing Websites: Platforms such as DMARC Analyzer, Dmarcian, EasyDMARC, and Valimail provide comprehensive SPF record validation, syntax checking, and real-time DNS TXT record analysis.
- Email Header Analysis Tools: Mail transfer agents and security appliances from Barracuda Networks, Cisco Talos, or Trend Micro offer detailed email header analysis that reveals SPF pass and fail outcomes alongside DKIM and DMARC results.
- SPF Record Creation and Publishing Utilities: Cloudflare DNS management and Google Workspace Admin Console include interfaces for SPF record creation that integrate SPF record syntax validation and DNS propagation tracking.
- Open-Source Utilities: CLI tools like `spf-query` or `dig` for SPF record lookup enable granular SPF DNS configuration diagnosis and SPF record creation verification.
- Security Intelligence Sources: Security vendors such as FireEye, Kaspersky, and IBM Security provide threat intelligence on SPF blacklist trends and emerging challenges in SPF policy enforcement.
- Community and Vendor Documentation: Resources from Microsoft Exchange, Okta, Oracle, and Amazon SES offer best practice guides on SPF record creation tailored to their SMTP authentication frameworks.

By leveraging these tools and insights, email administrators can proactively identify SPF sender invalid errors, refine SPF policies, and strengthen overall Email security posture to protect against Email spoofing and phishing threats.
SPF in Combination with DKIM and DMARC for Enhanced Authentication
To bolster email security and combat Email spoofing and Email phishing effectively, organizations increasingly implement a layered Email authentication approach by combining Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC). This triad helps create a robust SPF chain of trust and ensures comprehensive policy enforcement across email delivery ecosystems.
SPF provides validation by checking the SPF record — a DNS TXT record — published by the sender’s domain. This record specifies authorized Mail Transfer Agents (MTAs) using various SPF mechanisms such as the include mechanism, IP4 and IP6 mechanisms, MX mechanism, PTR mechanism, and all mechanism. Combined with DKIM, which authenticates the integrity of the message via cryptographic signatures embedded in email headers, and DMARC, which aligns SPF and DKIM results to the sender domain and specifies policy enforcement, organizations achieve a high level of Email security and improved Email deliverability.
SPF alignment is critical in this mixture; DMARC mandates alignment between the SPF authenticated domain and the “From” domain in the email header to prevent spoofers from exploiting discrepancies. When an email passes all three layers—SPF pass, valid DKIM signature, and DMARC policy enforcement—receiving servers like those from Google, Microsoft (Outlook.com, Microsoft Exchange), Yahoo, and Cloudflare are more likely to accept the message and avoid marking it as spam or rejecting it due to SPF fail or SPF hardfail.
Major security vendors including Barracuda Networks, Proofpoint, Mimecast, Agari, Valimail, and DMARC Analyzer offer tools for SPF record validation, DMARC compliance monitoring, and SPF troubleshooting that help organizations maintain proper SPF DNS configuration, ensuring SPF record syntax accuracy and mitigating errors such as SPF syntax error or exceeding the SPF lookup limit.
The Evolution of SPF and Future Developments
SPF has evolved significantly since its inception to address the growing sophistication of Email phishing and Email spoofing tactics. Early versions were limited by structural constraints such as the SPF record length and the SPF lookup limit (maximum of 10 DNS lookups per SPF record). These limitations prompted the development of more efficient SPF mechanisms and modifiers, including the redirect modifier to consolidate records and minimize recursion.
Despite these improvements, SPF’s inability to validate the email body or headers beyond the envelope sender domain has driven the adoption of DKIM and DMARC as complementary standards. Nokia, Cisco Talos, and Talos Intelligence Group continue to publish cybersecurity research and advocate for best practices including SPF record publishing strategies to optimize SPF DNS propagation and policy enforcement.
Future enhancements focus on improving resilience against SPF fail scenarios by refining SPF record creation tools and adopting SPF testing tools to simulate and troubleshoot SPF DNS propagation delays or SPF error codes caused by misconfiguration. AI-driven SPF record auditing solutions from companies like Okta and IBM Security are emerging to anticipate SPF misconfigurations before they impact email flow.

Additionally, ongoing work aims to extend SPF policy enforcement protocols to better address complex email forwarding scenarios and SPF recursion challenges, developing new SPF modifiers or augmenting SPF policies with dynamic updates possibly using blockchain or DNSSEC for better SPF chain of trust verification.
Case Studies: Real-World Examples of SPF Sender Invalid Errors
The complexity of SPF DNS configuration can lead to frequent SPF sender invalid errors, which translate into delivery setbacks and potential reputational damage. Consider Microsoft Exchange administrators frequently encountering SPF softfail due to incorrectly configured SPF record mechanisms or exceeding the SPF lookup limit. Such errors often stem from including multiple third-party services like SendGrid, Amazon SES, and SparkPost without consolidating SPF include mechanisms properly, which leads to SPF recursion and SPF record length exceeding DNS DNS TXT record limits.
Google’s Gmail spam filters also aggressively flag SPF fail or SPF hardfail results, especially when SPF record validation fails due to syntax errors or unsupported SPF mechanisms. Yahoo Mail, leveraging insights from security research groups like FireEye and Trend Micro, illustrates how incorrect SPF MX or PTR mechanism usage can inadvertently trigger SPF neutral results, allowing some spoofed emails to bypass SPF email filtering.
Another example involves enterprise deployments of Zoho Mail integrated with Mailchimp for marketing campaigns. Inaccurate SPF record creation with duplicated IP4 and IP6 mechanisms caused SPF blacklist occurrences and SPF fail scenarios, affecting Email deliverability and requiring SPF troubleshooting with SPF testing tools. Cisco’s security teams recommend best practices for SPF record publishing using SPF record length optimization and SPF policy fine-tuning with SPF modifiers to prevent SPF record lookup failures.
In all these cases, a comprehensive Email header analysis revealed the impact of poor SPF DNS propagation and improper SPF policy enforcement on the reputation of the SPF sender domain, emphasizing the importance of coordinated Email authentication strategies involving SPF, DKIM, and DMARC.
Maintaining Healthy SPF Records to Prevent Sender Invalid Errors
Maintaining a healthy SPF record is paramount in safeguarding email domains from spoofing, phishing attacks, and ensuring optimal Email deliverability. Effective SPF DNS configuration requires attention to SPF syntax, limiting SPF record lookups, avoiding SPF recursion, and utilizing SPF mechanisms and modifiers judiciously.
Organizations must engage in regular SPF record validation using SPF testing tools from providers such as Dmarcian, EasyDMARC, and DMARC Analyzer, and monitor SPF email headers for anomalies. The collaboration between email service providers like Microsoft Exchange, Google, Yahoo, and security firms such as Symantec, Kaspersky, and Oracle ensures continual SPF policy enforcement improvements enhancing domain protection frameworks.

Overall, adherence to SPF compliance best practices alongside complementary authentication via DKIM and DMARC equips enterprises to thwart Email spoofing attempts, reduce false positives in spam detection, and maintain trust within digital communication channels.
FAQs
What is the purpose of an SPF record in email authentication?
An SPF record specifies which mail servers are authorized to send email on behalf of a domain. Published as a DNS TXT record, it helps receiving servers perform SPF record lookup and verify the sender, reducing the risk of Email spoofing and phishing.
How does SPF fail differ from SPF softfail and SPF hardfail?
An SPF fail typically indicates the sender’s IP is not authorized by the SPF record. SPF softfail is a warning that the email may be unauthorized but still accepted, while SPF hardfail means strict denial, and the message should be rejected.
Can SPF alone prevent all spoofing and phishing attacks?
No, SPF primarily prevents spoofing of the envelope sender domain but cannot verify message content. Combining SPF with DKIM and DMARC enhances overall Email security and policy enforcement.
What causes SPF record syntax errors and how can they be fixed?
SPF syntax errors occur from malformed SPF records, for example, incorrectly formatted mechanisms or modifiers. These can be fixed by SPF record validation tools that check SPF record syntax and compliance before DNS TXT record publishing.
What is the SPF lookup limit and why is it important?
The SPF lookup limit restricts the maximum number of DNS lookups (usually 10) a receiving server performs during SPF validation. Exceeding this results in SPF fail or SPF neutral, affecting email deliverability.
How does the SPF redirect modifier improve SPF records?
The SPF redirect modifier points to another domain’s SPF record, simplifying SPF record management and avoiding SPF recursion or exceeding lookup limits, thus optimizing SPF DNS propagation and enforcement.
Which companies provide tools for SPF record validation and DMARC monitoring?
Organizations like DMARC Analyzer, Dmarcian, EasyDMARC, Agari, and Valimail offer sophisticated SPF record validation, DMARC compliance monitoring, and comprehensive Email authentication solutions.