Threat actors try different tactics to intercept and steal data, which is further exploited for financial gain. One such tactic is an executive phishing attack. It’s a low-cost yet powerful way for threat actors to break into a company’s security. Cybercriminals trick junior-level executives through emails or phone calls made by impersonating top-level executives, and the outcome is usually serious damage.
The average cost of a phishing attack for a mid-sized company is $4.65 million, with most of the expenses coming from lost business and recovery efforts. Such statistics underscore the need to understand the different attack types and ways to ward them off. This blog primarily focuses on explaining how executive phishing unfolds and what companies can do to prevent it.
What is executive phishing?
Executive phishing, also known as CEO phishing, is one of the most threatening cyberattacks. It involves mimicking the emails or phone calls of the CEO, CFO, and other members of top management.

It aims to exploit the organization’s sensitive information, financial assets, or even transactions by taking advantage of a credible resource, such as a CEO.
The cybercriminals work by stealing digital business cards, emails, email signatures, writing style, etc., of executives so that the messages appear legitimate and convincing.
Cyberattackers create sophisticated phishing emails that look convincing and trustworthy, tricking employees or customers into believing the message is real. This breaks down the usual chain of command and damages trust within the company.
Such emails look absolutely real and are well-crafted to trick someone from the organization into sharing the details of ongoing contracts, financial deals, agendas, important meetings, and other sensitive information.
Thus, the attacker seeps in, finding a way to access credentials, confidential data, and the corporate network, or perhaps anything that is meant to be kept strictly within the organization/parties.

Executive phishing attacks also try to trick staff members into sending money, granting access to networks, or disclosing private information such as login credentials, passwords, and sensitive documents. After gaining access or obtaining these credentials, the attacker use them maliciously.
Why are phishing attacks usually targeted at C-level executives?
Hackers often target C-level and management executives because they have access to valuable information that they can sell on the Dark Web or even use to blackmail the company. These cyberattacks frequently use the credibility and trust that comes with the positions of CEOs and CFOs. Because if not requested by a top-level executive, a customer or staff member might not reveal such crucial data to anybody or everybody in the mail.
C-level executives can be easy targets for phishing attacks that try to collect sensitive information by any means possible because they usually have access to financial data, personally identifiable information (PII), and other private company documents.
Additionally, if their accounts are compromised, they can be utilised to execute extremely convincing attacks against partners or other employees.
A successful CEO phishing attack can have serious repercussions such as major financial losses, damage to the company’s reputation, legal issues, operational disruptions, data breaches, and a lot of stress for the people involved.
Major executive phishing attack types
Below are commonly witnessed forms of executive phishing attacks:
Business email compromise (BEC)
BEC attacks impersonate CEOs and other high-ranking people (commonly referred to as CEO fraud in this context) and ask for sensitive information or money transfers.

To fool the recipients into thinking the emails are authentic and urging them to fulfil the fraudulent request, BEC attackers send fake emails that look real; they might copy the company logo, use a spoofed email address, and even write like a company executive.
Invoicing attacks
This cyberattack involves stealing money through invoices. Here, the attacker creates a legitimate-looking invoice with unnoticeable errors and discrepancies, which generally direct payments to the attacker’s account.
Exploitation on video communication platforms
A hacker uses a video conferencing tool to pose as the top-level executive in this attack. For instance, they may pose as the CEO and request private information through a fictitious meeting or chat using Google Hangouts or comparable methods.

The employees may also receive an email from the hacker informing them that they will be meeting with a finance representative via video conference.
They provide them instructions to download a potentially harmful program and enter their login information, which could compromise credentials. Moreover, with the advent of generative AI, it’s now possible to create deepfake videos of the targeted executives, which are then used during video conferences.
Mitigations and preventions for executive phishing attacks
Executive phishing can be prevented at your company by using the following security measures:
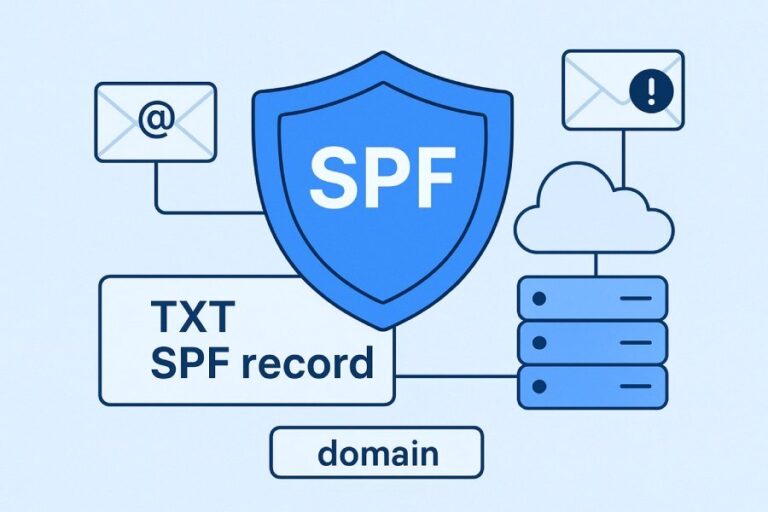
Implementing SPF, DKIM, and DMARC
Key email security protocols include SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance), which help verify sender identity and protect against spoofing.
SPF works by allowing domain owners to specify the email servers and IP addresses they authorize to be used for sending emails on their behalf. DKIM attaches a cryptographic signature that verifies the sender and ensures the message hasn’t been tampered with. DMARC is deployed to define a policy for handling emails that fail SPF or DKIM checks. When combined, these protocols significantly reduce the risk of email impersonation.

Security awareness training
Security awareness training teaches people how to spot suspicious emails based on their sender information (e.g., slightly changed email addresses), context (e.g., requests outside of regular procedures, unexpected communication methods or times), and content (e.g., unusual requests, urgency, poor grammar/spelling).
Employees should also be taught how to safely report these emails and confirm requests via independent, reliable channels of contact.
Multi-factor authentication (MFA)
By forcing users to input a code texted to their phones, created by an app, or used with a physical security key before obtaining access to accounts and systems, multi-factor authentication (MFA) adds an extra layer of security on top of passwords.
Even if credentials are stolen, attackers are greatly hampered when MFA is implemented across all important accounts.
Timely software updates and patch management
Regular updation of operating tools, email clients, system browsers, third-party applications, and software is essential. These should be well managed with the latest security patches that have safeguarding fixes to enhance prevention from malicious attacks.
The bottom line
Executive phishing incidents, such as CEO fraud, are extremely focused and can have a disproportionately detrimental effect on people and enterprises. Don’t click links, open files, or follow directions hastily if you receive messages from strangers or requests that appear strange or urgent.
You can significantly lower your risk of being a victim by remaining alert, putting strong technical defences in place, and cultivating a security-conscious culture that is backed by defined protocols.