
As per a report, more than 90% of the world’s top 1.8 million email domains are still at risk of spoofing attacks because only 7.7% of them have set up the strongest DMARC policy, called p=reject, which fully blocks unauthorized emails.
While Google, Yahoo, and Microsoft are encouraging users to implement DMARC, the configurations in most DMARC records are often loose or overly permissive. Since DMARC is based on SPF and DKIM, it’s also important that these two protocols are set up properly and that they don’t have alignment issues. We say this because for DMARC to consider the valid SPF results, the authenticated domain must be properly aligned with the domain visible to the recipient. This is exactly where most SPF records break and trigger the authentication process.
All this mess leads to SPF alignment failures despite emails passing SPF itself. This blog explains why this happens and how attackers take advantage of these misalignments.

What is identifier alignment in DMARC?
In email authentication, alignment simply means that the domain name involved in SPF and DKIM should be the same as the one visible to the recipients in the ‘From’ address. If these match, then it means the email is truly authorized and sent by a genuine sender, rather than just being technically authenticated by some unrelated server.
If the concept of alignment was not there, the threat actors could easily send emails using one domain for SPF and DKIM authentication, but then they would display a completely different domain in the ‘From’ address. This could fool the recipient into divulging private information.
With DMARC’s identifier alignment, the domains must match; otherwise, the emails will be tossed in the spam folder or get rejected. This closes a major loophole that attackers often exploit.

Here’s how SPF alignment technically works-
SPF alignment works by comparing the domain name in the ‘Return-Path’ and the ‘From’ header. The former is used behind the scenes during the delivery process, whereas the latter is the one visible to the recipient.
For SPF alignment to pass, these two domains must match. DMARC allows two modes of alignment:
- If the domains are exactly the same (strict mode), or
- If they belong to the same organizational domain (relaxed mode), alignment is considered valid.
If the domains don’t align, SPF alignment fails, even if the SPF check itself passes. That’s why a valid SPF result alone isn’t enough for DMARC compliance.

Example
Let’s say your company uses a third-party email service:
- The sending server uses mail.service.com as the Return-Path domain.
- But the email displayed to the recipient has the “From” address as company.com.
In this case:
- SPF may pass because mail.service.com is authorized to send on behalf of itself.
- However, DMARC fails because the Return-Path domain (mail.service.com) and the visible From domain (company.com) don’t align.
This is a very common scenario, especially when businesses rely on external vendors to send marketing or transactional emails on their behalf.
Strict vs relaxed alignment
There are two alignment modes in DMARC. Here’s how each of them functions-
Relaxed alignment
In the relaxed DMARC alignment mode, some flexibility is allowed. This means that the domains don’t have to match 100%. As long as the organizational domain or the parent domain is the same in the ‘Return-Path’ and the ‘From’ header, alignment is attained.
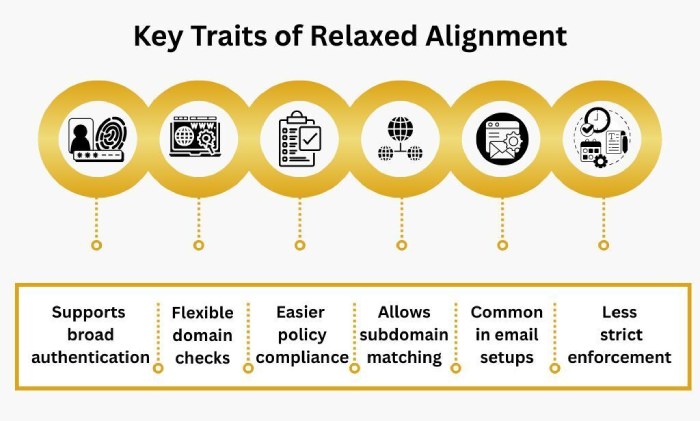
For example, if your email uses ‘mail.example.com’ as the Return-Path or DKIM signing domain, and ‘example.com’ as the visible ‘From’ address, relaxed alignment considers them aligned because they share the same organizational domain (example.com).
Strict alignment
In strict alignment, there has to be an exact match of the domain in the ‘Return-Path’ and the ‘From’ header. The alignment will fail even if one of the domains is a subdomain of the other.
This alignment mode establishes tighter security, eliminating the possibility of accidental misconfigurations or unauthorized subdomains. Yes, this alignment mode sounds way more foolproof than the ‘relaxed’ one, but the strictness can lead to unintentional false negatives, which can further be the reason for missed communication opportunities.

How to ensure SPF alignment works for you?
As mentioned above, SPF alignment is crucial for the proper functioning of DMARC and full compliance. Even if emails sent from your domain reflect a ‘pass’ result for SPF authentication, they can still fail the DMARC checks if the domains involved don’t align. Here’s how you ensure alignment between domains for optimal email delivery and enhanced sender reputation, resulting in uninterrupted communication and increased business opportunities.
1. Choose the right alignment mode
The relaxed alignment mode is ideal for businesses that:
- Use multiple email platforms and subdomains.
- Rely on third-party vendors who send emails on their behalf.
- Want fewer disruptions while still benefiting from DMARC protection.
The strict alignment mode is good for businesses that:
- Prefer maximum control over their email ecosystem.
- Primarily send emails from a single domain.
- Have a fully centralized and tightly managed email infrastructure.

Ultimately, the choice depends on your organization’s email setup, level of control, and security priorities. Many companies start with relaxed alignment to ensure smooth deliverability and later tighten controls once their email environment is fully documented and stable.
2. Configure the Return-Path smartly
For proper alignment, you have to ensure that your email service provider is using a Return-Path domain that matches your main sending domain. In case of relaxed alignment, it’s fine if there is an involvement of a parent domain and its subdomain. However, if you have set the strict alignment mode, the two domains have to be exactly the same.
At times, third-party email service providers use the default, generic Return-Path (like bounce.mailprovider.com), which doesn’t align with the visible ‘From’ address, causing DMARC to fail because of misalignment.
We suggest that you configure your email service provider to use a custom domain. Alternatively, you also delegate a subdomain to your email service provider so that the domains align.

3. Monitor DMARC reports
DMARC reports can be used as tools for diagnosing alignment and other issues that you can fix before attackers exploit them. These reports help you:
- Identify sources where SPF passes but alignment fails.
- Detect unauthorized senders spoofing your domain.
- Spot configuration gaps in your ESP or internal infrastructure.
We understand that adjusting the Return-Path settings or alignment mode can be a bit too technical for some people. This is precisely where the AutoSPF team can help you. We take care of anything and everything related to SPF, DKIM, and DMARC. So, reach out to get your email deliveries sorted.






