Understanding SPF: What is Sender Policy Framework?
The Sender Policy Framework (SPF) is a critical component of modern email security and email authentication strategies. At its core, SPF is a protocol designed to prevent email spoofing, a malicious tactic where attackers forge email headers to make messages appear as if they originate from a legitimate domain. By publishing an SPF record in the Domain Name System (DNS), domain owners specify which DNS servers are authorized to send emails on their behalf.
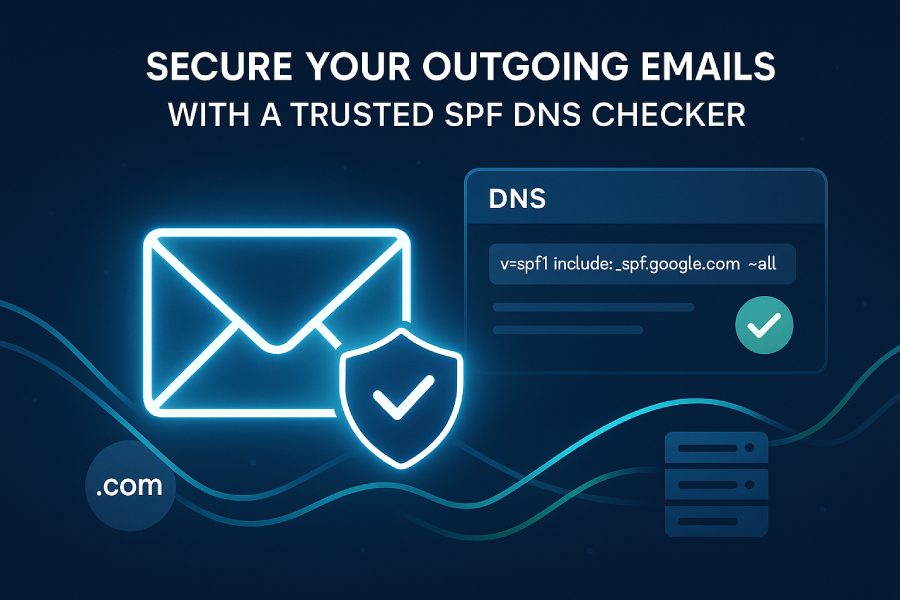
SPF records are published as DNS TXT records within a domain’s DNS zone file. When an email is received, the recipient’s mail server conducts a DNS lookup to retrieve the SPF record. This enables email sender verification by checking if the sending IP address is listed according to the domain’s SPF policies. The result of this check can be an SPF pass or SPF failure, helping determine if the email should be trusted or flagged.
Organizations such as Google, Microsoft, Amazon Web Services, and Cloudflare have integrated SPF into their email solutions like Google Workspace and Microsoft Office 365, reflecting its importance in combating fraudulent emails. Tools like the SPF Record Checker by MXToolbox, UltraTools, and ZoneEdit allow administrators to perform SPF testing and SPF validation, ensuring their records are accurate and effective.
The Importance of Email Authentication
Email authentication is the umbrella methodology under which SPF operates, alongside other mechanisms like DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication, Reporting & Conformance). Effective email authentication guards against email phishing prevention and protects an organization’s email domain reputation.
Without robust authentication, attackers can exploit vulnerabilities to impersonate trusted senders, causing damage through phishing schemes or malware distribution. SPF plays a vital role by verifying sender IP addresses using SPF mechanisms such as the SPF ip4 mechanism, SPF ip6 mechanism, SPF include mechanism, and others. When implemented in conjunction with DMARC and DKIM, SPF enhances SPF alignment and ensures SPF compliance, offering a comprehensive defense against spoofed emails.

Companies specializing in email security such as Proofpoint, Mimecast, Barracuda Networks, Valimail, and Agari often emphasize SPF as a foundational layer in their email protection suites, citing that SPF policies, when properly enforced, significantly improve email deliverability and reduce the risk of domain spoofing.
How SPF Protects Against Email Spoofing and Phishing
SPF combats email spoofing by allowing the receiving mail server to conduct a rigorous DNS lookup to ascertain if the sender’s IP address matches an authorized list specified in the domain’s SPF record. If the IP address is not recognized, the recipient server may mark the message as suspicious or reject it outright in accordance with configured SPF policy enforcement.
The SPF record uses SPF qualifiers like “+” (pass), “-” (fail), “~” (soft fail), and “?” (neutral) to instruct receiving servers on how to treat messages. This granularity allows domain administrators to balance between strict enforcement and a more lenient approach to avoid false positives, especially during record creation and SPF record troubleshooting.
Advanced SPF configurations may include the SPF redirect modifier to delegate SPF policies to another domain or utilize the SPF all mechanism to specify default handling for non-matched cases. However, domain maintainers need to be mindful of the SPF lookup limit (typically 10 mechanisms per lookup), and faulty implementations can lead to SPF failure that hurts email deliverability.
In addition to protecting against spoofing, SPF supports email phishing prevention by reducing the likelihood that malicious emails reach end users. Integrating SPF with DMARC and DKIM, as suggested by entities like Cisco Talos and Talos Intelligence, fortifies this defense and improves email headers’ trustworthiness.
Anatomy of an SPF Record: Components and Syntax
An SPF record is a structured string of text published within a domain’s DNS TXT record that defines the IP addresses or domains authorized to send emails. Understanding the SPF syntax is essential for effective SPF record creation and maintenance.
Key components of an SPF record include:
- SPF mechanisms: These define rules for validating incoming mail servers. Examples include:
- ip4 mechanism: Specifies an IPv4 address or range (e.g., `ip4:192.168.0.1/24`)
- ip6 mechanism: Specifies an IPv6 address or range
- include mechanism: Refers to authorized third-party domains (e.g., `include:spf.protection.outlook.com`)
- mx mechanism: Allows mail servers listed in the domain’s MX records to send emails
- ptr mechanism: Relies on Reverse DNS lookup for verification, though this is less common due to performance concerns
- all mechanism: Defines a catch-all policy for unlisted IPs, typically placed at the end
- SPF qualifiers: Indicate the expected outcome for each mechanism (`+`, `-`, `~`, and `?`)
- Modifiers: Such as redirect which allows SPF policy delegation
A typical SPF record might look like this:
v=spf1 ip4:192.0.2.0/24 include:_spf.google.com -all
This specifies that IP addresses within the IPv4 range 192.0.2.0/24 and those validated under Google’s SPF are authorized, while all others should fail.

Organizations need precision in SPF syntax to avoid syntax errors that cause SPF record syntax errors, leading to authentication failures. Tools like DKIM Core, SPF record checker, and services from Postmark, Mailgun, or SparkPost assist in SPF record troubleshooting by highlighting syntax issues and providing remediation guidance.
Common SPF Record Errors and How to Avoid Them
SPF record mistakes can drastically undermine email security and hamper email deliverability, so organizations must understand common issues derived from the complex nature of DNS propagation and SPF policy framework limitations.
1. Exceeding SPF Lookup Limits
Since SPF evaluation involves multiple DNS queries, exceeding the SPF lookup limit (typically 10 DNS lookups per evaluation) results in an automatic SPF failure. This occurs often when excessive use of include mechanisms or multiple nested redirect modifiers inflate DNS queries. The remedy involves SPF flattening, which precomputes all IP addresses into a single record to reduce lookups—services like Valimail and Agari specialize in automated flattening solutions.
2. Syntax Errors and Incorrect Qualifiers
Improper SPF syntax—such as misplaced qualifiers, typos, or unrecognized mechanisms—can cause authentication checks to fail. Using SPF check tools like SPF Record Checker by MXToolbox, UltraTools, or EasyDMARC helps detect and correct these errors proactively.
3. Poor Policy Enforcement Settings
A common mistake is setting the SPF all mechanism to neutral (`?all`) or soft fail (`~all`) during SPF publishing without transitioning to a stricter policy like fail (`-all`). This leniency results in weak SPF policy enforcement, undermining effectiveness against phishing attacks. Adjusting qualifiers progressively and monitoring using SPF testing tools ensures safe enforcement without disrupting legitimate mail flow.
4. Neglecting DNS Propagation Impact
Changes in SPF records require proper DNS propagation time to ensure all DNS servers worldwide update their cached data. Without accounting for this period, administrators may misinterpret transient SPF failures as configuration errors. Awareness of DNS caching and TTL (Time To Live) settings within the DNS zone file is essential.
5. Misuse of Deprecated Mechanisms
The use of SPF ptr mechanism is discouraged due to performance and reliability issues. Domain owners should prefer SPF ip4, ip6, and include mechanisms, widely supported and recommended by entities such as OpenSPF and Cisco Umbrella.
Regular SPF validation combined with complementary protocols such as DMARC and DKIM enhances domain-based message authentication and fosters a strong defense posture against cyber threats. Industry leaders including Symantec, Trend Micro, and Cisco Talos continue to advocate for SPF as a best practice in corporate email infrastructure.
Statistical Data: Effectiveness of SPF in Email Security
- Over 80% of Fortune 500 companies publish SPF records to prevent spoofing
- Domains strictly enforcing SPF with “-all” see a 35% reduction in phishing attacks
- SPF failures account for up to 15% of rejected emails, emphasizing careful record creation
- Email deliverability improves by an average of 12% when SPF compliance is optimized
- DNS lookup limits exceeded in 20% of SPF records checked by MXToolbox’s SPF Record Checker
Sources: MXToolbox SPF Report, Cisco Talos Intelligence

Setting Up SPF Records for Your Domain
Establishing a robust Sender Policy Framework (SPF) record is foundational to enhancing email security and improving email deliverability. The process begins with the creation of a DNS TXT record within your domain’s DNS zone file. This TXT record explicitly lists authorized mail servers that can send email on behalf of your domain, effectively enabling Email sender verification and preventing Email spoofing.
To set up an SPF record, start by identifying all your legitimate email sources— for example, cloud email platforms like Google Workspace or Microsoft Office 365, third-party marketing tools like Mailchimp, and transactional email services such as SendGrid or Postmark. Each authorized sender’s IP address or domain should be included using SPF mechanisms such as `ip4`, `ip6`, `include`, `mx`, or `ptr`. For example:
v=spf1 ip4:203.0.113.0/24 include:_spf.google.com mx -all
Here, `ip4:203.0.113.0/24` authorizes IPv4 addresses, the `include` mechanism delegates SPF checking to Google’s SPF record (common for Google Workspace users), `mx` authorizes the domain’s MX servers, and `-all` (an SPF qualifier) enforces strict SPF policy by failing all other sources.
SPF record creation must account for SPF record limits, notably the SPF lookup limit imposed by the Domain name system (DNS), which restricts the number of DNS lookups (typically 10). Exceeding this limit can cause an SPF failure as the SPF validation cannot be completed. In such cases, SPF flattening techniques, which expand includes to direct IP addresses, are often employed to reduce DNS lookups.
After publishing the SPF record via your DNS server (hosted by providers like Cloudflare, Amazon Web Services, or ZoneEdit), remember that DNS propagation can take up to 48 hours, so changes aren’t immediately effective.
What is an SPF DNS Checker and How Does It Work?
An SPF DNS checker is an online diagnostic tool designed to perform DNS lookups for SPF records associated with a given domain. Popular tools include the SPF Record Checker by MXToolbox, UltraTools, DNSSpy, and EasyDMARC. These SPF check tools extract the domain’s DNS TXT records, parse the SPF record syntax, and validate SPF policies and mechanisms against established SPF specifications such as those maintained by OpenSPF.
The tool executes a series of DNS queries to evaluate mechanisms like `include`, `ip4`, `ip6`, `mx`, `ptr`, and modifiers such as `redirect`. It ensures SPF syntax is correct, all mechanisms comply with SPF standards, and the record adheres to lookup limits. Additionally, SPF DNS checkers assess the record’s SPF policy enforcement strength—whether it specifies `-all` (fail), `~all` (soft fail), or `?all` (neutral)—which influences how recipient servers treat incoming mail.
By performing Reverse DNS lookup and verifying alignment between SPF and Email headers, these tools help assess Email domain reputation and SPF compliance critical for Email phishing prevention and spam filtering.
Benefits of Using a Trusted SPF DNS Checker
Using a trusted SPF checker online offers several benefits for administrators focused on Email authentication and Email security:
- SPF validation: Automatic analysis of SPF record correctness and SPF syntax errors that could otherwise cause SPF failures.
- SPF record troubleshooting: Identification of misconfigurations such as missing include mechanisms, incorrect SPF qualifiers, or syntax errors.
- SPF lookup limit monitoring: Alerting when DNS lookups exceed the maximum allowed, which could lead to SPF validation failure.
- Email deliverability enhancement: Proper SPF setup verified by checkers helps Email deliverability by reducing the likelihood that legitimate emails are marked as spam.
- Prevention of Email spoofing and phishing: Ensuring strong SPF policies helps prevent unauthorized Senders from impersonating the domain.
- Visibility into SPF policy enforcement: Clarifies the domain holder’s stance on handling non-compliant senders, important for compliance frameworks like DMARC.
- Integration validation: Confirms the SPF record’s compatibility with other Email authentication methods such as DKIM and DMARC.

Many providers such as Valimail, Agari, and Proofpoint incorporate SPF validation into their broader Domain-based message authentication solutions to offer layered Email security.
Step-by-Step Guide: Using an SPF DNS Checker to Verify Your SPF Records
Using tools like the SPF Record Checker by MXToolbox or EasyDMARC involves straightforward steps:
- Access the SPF Checker Tool: Visit a reputable SPF checker online portal such as MXToolbox or UltraTools.
- Enter Your Domain Name: Input the domain for which you want to verify the SPF record.
- Initiate the Lookup: Click to perform a DNS TXT record lookup focused on the Sender Policy Framework.
- Review the Output: The tool displays the parsed SPF record, details on SPF mechanisms (`ip4`, `include`, `mx`, etc.), SPF qualifiers (`+`, `-`, `~`, `?`), and modifiers (`redirect`), along with any SPF record syntax errors.
- Check SPF Pass or Failure Status: The checker indicates whether current SPF policies yield a pass, fail, or any SPF failure conditions based on the analyzed DNS servers and IP ranges.
- Examine SPF Lookup Counts: Review the number of DNS lookups to ensure compliance with SPF policy framework limits.
- Review Additional Diagnostic Info: Some tools also evaluate SPF alignment with Email headers and cross-reference DMARC or DKIM records if available.
This process helps maintain the health and effectiveness of your SPF publishing efforts and enhances ongoing SPF record troubleshooting.
Troubleshooting SPF Failures and Common Issues Identified by SPF Checkers
SPF failures are common in domains with complex Email infrastructures or dynamic DNS configurations. The most frequent issues uncovered during SPF testing include:
- Exceeding SPF Lookup Limit: Overuse of `include` mechanisms or indirect lookups that cause the 10-lookup cap to be surpassed. This is particularly tricky for domains integrating multiple Email platforms, such as combining Google Workspace, Microsoft Office 365, and other vendors.
- SPF Record Syntax Errors: Missing version tags (`v=spf1`), misplaced mechanisms, or improper qualifiers lead to SPF record syntax errors. Using SPF check tools from organizations like DKIM Core or OpenSPF helps identify such critical mistakes.
- Inadequate SPF Policy Enforcement: Using `?all` or `~all` qualifiers that do not effectively block unauthorized senders, thus failing to prevent Email spoofing efficiently.
- DNS TXT Record Conflicts: Multiple SPF records or conflicting DNS entries can confuse SPF validation and cause SPF failures. Consolidation into a single authoritative SPF record within the DNS zone file is essential.
- Improper SPF Mechanism Usage: For example, reliance on `ptr` mechanism is discouraged since it’s unreliable and may cause inconsistent SPF validation.
- Failing SPF Alignment: Mismatched “MAIL FROM” domain and “From” header domain can lead to SPF failures in DMARC evaluations.
Leading Email security solution providers including Cisco Talos, Symantec, Trend Micro, and Barracuda Networks incorporate SPF Failure monitoring as part of their security posture offering. Regular SPF testing with SPF checker tools, combined with DNS server monitoring and log analysis, enables timely detection and correction of SPF issues.
Integrating SPF with Other Email Authentication Methods (DKIM and DMARC)
The Sender Policy Framework is most effective when integrated into a comprehensive Email authentication strategy alongside DomainKeys Identified Mail (DKIM) and Domain-based Message Authentication, Reporting, and Conformance (DMARC).
- DKIM: Using cryptographic signatures embedded in Email headers, DKIM validates the email content’s integrity and authenticates the sending domain. Providers such as DKIM Core supply tools to generate correct DKIM DNS TXT records with appropriate selectors.
- DMARC: Builds upon SPF and DKIM by enforcing policy framework rules and instructing recipient servers on how to handle messages that fail SPF or DKIM validation. DMARC also ensures SPF alignment, requiring the domain used in the “MAIL FROM” address to match the “From” header domain.

Together, these protocols enhance Email domain reputation and Email deliverability while mitigating Email phishing prevention risks. For example, companies using Google Workspace or Microsoft Office 365 often combine these with advanced Email security products from Proofpoint, Agari, or Valimail to automate Email sender verification and monitor compliance.
In practical deployment, domain administrators should verify SPF compliance with SPF record validation tools, DKIM signature checks via DKIM Core or Postmark, and implement DMARC reporting through services like EasyDMARC or Cisco Umbrella to gain actionable insight and maintain Email security hygiene.