For almost all major businesses today, email is the primary means of communication. It is through email that these organizations exchange even the most critical and sensitive information, like bank details, invoices, personal information, and more. This makes for the perfect bait and lures cybercriminals into exploiting the inherent trust that users place in emails.
And this is exactly why email is known to be one of the most targeted attack vectors in 2025, so much so that every one in four email messages today is either malicious or unwanted spam.
To make things worse, cybercriminals have become smarter and more creative. They are devising new techniques to deceive unsuspecting users and launching attacks that are difficult to detect and tackle.
Here are some of the most common and grave attacks that have targeted businesses this year.
Most common email-based cyberattacks of 2025

So far, 2025 has been all about smarter, faster, and more deceptive email attacks. Cyberattackers are using artificial intelligence, automation, and social engineering to craft messages that look uncannily real. These attacks are harder to spot and cause bigger damage.
Let’s look at some of the most common ones:
Phishing attacks
Every year, phishing attacks top the charts by becoming the most prevalent attack techniques in the cybersecurity landscape. This year too, phishing remained the most dominant and damaging email-based threat. Attackers continue to trick users into revealing confidential information, such as passwords, credit card numbers, or login credentials, by sending emails that appear completely genuine.
In the age of AI, the problem has become even worse. It has made it easier for cybercriminals to bypass traditional security measures. In a recent report that analyzed phishing attacks, it was found that 76.4% of all phishing campaigns used such tactics and were able to evade security measures.

Supply chain compromise
After phishing, supply chain compromise is another technique that cyberattackers are leaning towards in 2025. According to Gartner, 45% of organizations worldwide are expected to experience attacks on their software supply chains by the end of this year.
In this type of attack, the attackers don’t directly come after you; they target your vendors or the stakeholders in your supply chain. These could include your software providers, IT service vendors, logistics partners, or even hardware suppliers.
It is easy to think that targeting your vendors might have no impact on you, but unfortunately, that’s not the case. When an attacker breaches a trusted third party, they gain a backdoor into your systems through legitimate access points such as software updates, shared credentials, or data exchanges. This means, even if you had nothing to do with the attack, you could still be the target.
Domain squatting

In 2025, cyber attackers continued to bank on the power of deception with domain squatting. Domain squatting is when attackers create fake websites that look almost the same as real ones; they might change a single letter, add a hyphen, or use a different domain ending like “.co” instead of “.com.” These small changes are easy to miss, especially when you’re in a hurry.
As you skim over this tiny detail, the trap is already set. One click on a fake link can take you to a website that looks completely real, where you might enter your password or card details without a second thought.
In 2025, these attacks have become even harder to spot. To make things worse, cyberattackers are now resorting to AI tools to automatically generate thousands of look-alike websites, complete with real logos, company names, and even security padlocks to make them seem safe.
Adding malicious attachments

In most cases, if you believe that the email is from a trusted source, you’re more likely to open and engage with it. That’s exactly what attackers these days are relying on.
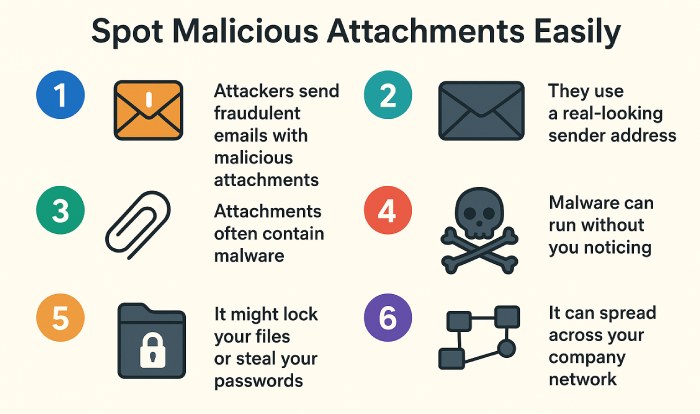
They send out fraudulent emails with malicious attachments, using a real-looking sender address, so you open them without giving it a second thought.
These attachments often contain malware inside them, and as soon as you download them, the malware can run without you even noticing. It might lock your files (which you can only access by paying ransom), steal your passwords, install a hidden backdoor so attackers can return later, or quietly spread across your company network.
It has become such a prevalent tactic that about one in every four HTML attachments sent by email in 2025 was found to be malicious.
Multimodal AI campaigns
As we already know, attackers, these days, are using AI to make their scams smarter and more believable, but there’s a lot more to it. In 2025, cyberattackers are using AI not just to craft real-looking emails, but they are also adding layers of deception to them.
They are doing this by combining multiple communication channels, like email, voice, and video, to make the trap almost impossible to escape.
For instance, you might get an email that looks like it’s from your company’s director, complete with the right name, tone, and signature. The email includes a link to a virtual meeting. When you join, the attacker could be there, using AI to clone the director’s voice and even their face through a deepfake video. This technique is called a multimodal AI campaign and has become more prevalent than ever.

To sum up
If there’s anything that we can take away from 2025, so far, it is that email is one of the easiest and most targeted attack vectors. And most importantly, its vulnerability isn’t just limited to the top five threats that we discussed. Threat actors are coming up with new tactics, such as blending AI, automation, and social engineering, which make detection and defence all the more difficult.
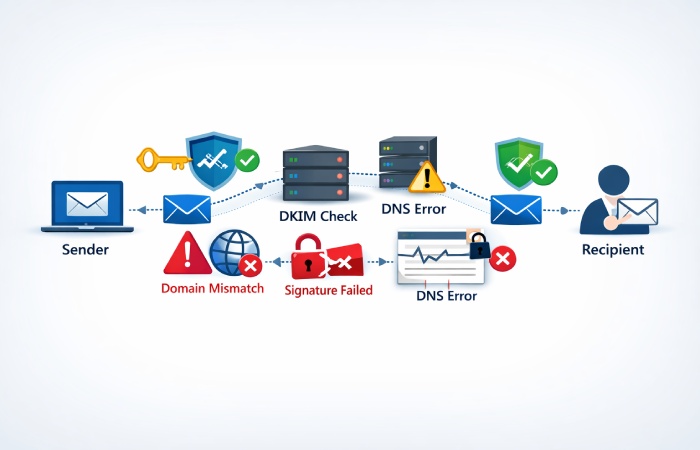
If you implement the right security measures, you can stay ahead of most of these attacks. This means using strong email authentication protocols like SPF, DKIM, and DMARC, enabling multi-factor authentication, regularly updating your systems and software, and investing in employee awareness training. With the right security measures, our automatic SPF flattening tool helps ensure your email domain stays protected and fully authenticated.
Not sure how to start your email authentication journey? Contact us today to know how!