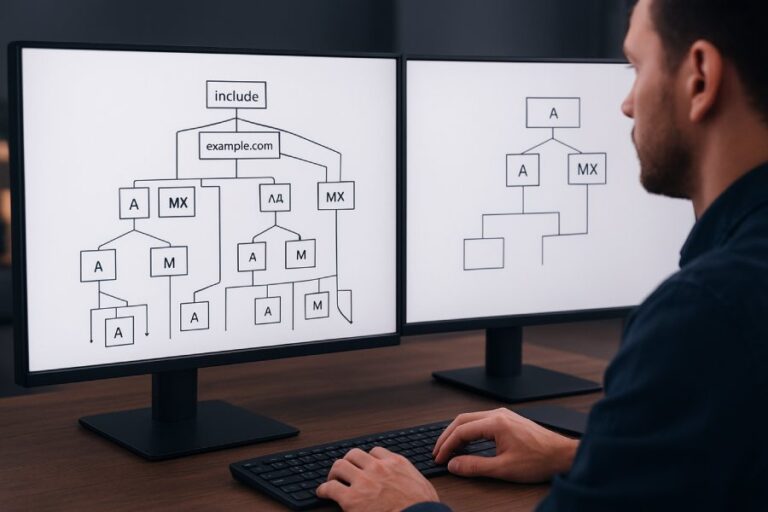
Use an SPF checker to fetch your current SPF record, validate syntax, confirm the new provider’s include and IPs, simulate sending IPs for pass/fail, measure DNS lookups and redirects, check interactions with A/MX, and pair results with DKIM/DMARC alignment and propagation status to prioritize fixes—AutoSPF automates each step with one-click checks, simulations, and guided remediations.
Email sender authentication changes are fragile during mail provider migrations because SPF is DNS-based, has a strict 10-lookup limit, and depends on correct includes for every system that sends mail “as” your domain. Even a small omission—like leaving out a marketing platform’s include—can cause SPF permerror/softfail, downgrade DMARC alignment, and silently push messages to spam or quarantine.
An SPF checker makes those issues visible and testable: it expands includes, evaluates A/MX references, traces redirects and macros, and simulates the recipient’s perspective against specific sending IPs. AutoSPF wraps that analysis with provider-aware templates, a live lookup counter, an include graph, a propagation monitor, and an API so you can fix records quickly and prevent regressions as you finalize the migration.
Start here: Locate, interpret, and validate your SPF after a provider switch (AutoSPF core workflow)
Identify your live SPF and the fields to inspect
- What to do in an SPF checker:
- Query TXT record at the root (example.com) and at your envelope subdomain if used (e.g., mail.example.com).
- Confirm a single “v=spf1 …” record exists; multiple records cause a permerror.
- Review mechanisms in order: ip4/ip6, a, mx, include, exists, ptr (discouraged), redirect, and the terminal all (~all or -all).
- Check qualifiers: + (pass, default), ? (neutral), ~ (softfail), – (fail).
- In AutoSPF:
- The Record Inspector fetches and normalizes the TXT value, highlights the effective evaluation order, flags duplicate records, and shows the final “all” qualifier.
- A “Provider Compare” panel maps what your new provider expects (their documented include and fail policy) against what you have live.
The specific fields to check (and why they matter)
- v=spf1: Must be first token; otherwise record is ignored.
- include: Make sure the new provider’s documented include is present; confirm the domain is spelled correctly and resolvable.
- ip4/ip6: If your provider assigns dedicated IPs, ensure each is listed or covered by the provider include.
- a/mx: If your SPF uses a or mx, verify those hostnames resolve to the intended sending IPs post-migration.
- redirect=: If used, ensure there is not also an “all” in the parent and that the target domain hosts the canonical SPF.
- all: Choose ~all during transition and -all once you validate full coverage (see policy guidance below).
AutoSPF ties every field to an inline check: clicking any mechanism shows the real-time DNS results it resolves to, whether it counts toward the 10-lookup limit, and whether the net effect is pass, neutral, or fail for a sample sending IP.
Verify the new provider’s include is present and correct
- What to check:
- Exact include value from documentation (e.g., include:spf.protection.outlook.com).
- That the include expands to IP ranges (no NXDOMAIN).
- That the include’s downstream includes don’t push you past the 10-lookup limit.
- In AutoSPF:
- “Include Validator” confirms presence, expansion health, and lookup cost; if missing, it offers a one-click snippet to copy into your DNS.
- “Transitive Include Graph” visualizes nested includes so you can spot long chains that bloat lookups or import risky ranges.

Detect multiple SPF records and consolidate
- The problem:
- Having two TXT records with v=spf1 for the same name produces SPF permerror; many recipients treat permerror like fail.
- Fix:
- Merge mechanisms into a single v=spf1 record; avoid duplicate “all.”
- In AutoSPF:
- “Duplicate Detector” flags multiples, generates a safe merged record, and simulates before/after results.
Understand A and MX interactions
- Why it matters:
- a and mx mechanisms dynamically include IPs resolved from your domain; if you changed MX hosts with your provider switch, SPF may now authorize unexpected IPs—or miss required ones.
- How to test:
- Resolve your domain’s A and MX records and compare to provider’s outbound ranges.
- In AutoSPF:
- The Resolver Panel shows each A/MX resolution, whether it’s in or out of your provider’s published ranges, and the net SPF effect for test IPs.
Keep TTLs and propagation under control
- During changes, use lower TTLs (300–900 seconds) to speed corrections; after stabilization, raise to 1–4 hours to reduce DNS load.
- AutoSPF’s Propagation Monitor fetches your SPF via multiple recursive resolvers worldwide and shows cache age vs TTL, helping you time when to test again.
Simulate sending—confirm pass/fail before you hit send (AutoSPF Simulator)
Simulate the new provider’s egress IPs
- What to do:
- Test with real or documented outbound IPs/subnets from your new provider.
- Run SPF evaluation with MAIL FROM domain used by your provider (often a return-path subdomain).
- AutoSPF:
- “SPF Simulator” lets you paste IPs, choose HELO/EHLO hostname, set MAIL FROM domain, and see pass/fail/neutral plus alignment with DMARC.
Measure DNS lookups and fix overages (>10)
- The rule:
- SPF allows at most 10 DNS-querying mechanisms/expansions (include, a, mx, ptr, exists, redirect). ip4/ip6 and all don’t count.
- How to fix:
- Replace broad a/mx with explicit ip4/ip6 where practical.
- Consolidate overlapping includes.
- Use conditional subdomains for third parties (e.g., mail.vendor.example.com with vendor-only SPF).
- Consider flattening with automated refresh.
- AutoSPF:
- A live “Lookup Counter” breaks down which mechanisms consume queries and offers “Smart Flattening” that periodically refreshes vendor ranges so your SPF stays within 10 lookups without going stale.
Evaluate redirects and macro expansions
- Redirect:
- redirect=domain replaces the entire SPF evaluation of your current record; do not mix with “all.”
- Useful for centralizing policy; risky if you don’t control the target.
- Macros:
- Macros (e.g., %{i}, %{s}) in exists/include are powerful but can complicate debugging and caching.
- AutoSPF:
- “Redirect & Macro Inspector” resolves macro values using your test context, shows the effective domain targets, and warns about caching or privacy implications.
Account for forwarding scenarios (SRS, DKIM fallback)
- Why SPF fails on forwarding:
- A forwarder’s IP sends your message; unless authorized in your SPF, SPF fails.
- Fix:
- Use SRS on forwarders to rewrite MAIL FROM.
- Ensure DKIM is enabled so DMARC still passes via DKIM alignment when SPF breaks in forwarding.
- AutoSPF:
- The Simulator has a “forwarding” toggle that reenacts forwarding without SRS, shows the expected SPF fail, and recommends DKIM/SRS mitigations.
Choose soft fail vs hard fail during migration
- Guidance:
- Use ~all initially to prevent strict rejections while you discover and add missing senders.
- Switch to -all once tests and logs prove complete coverage.
- AutoSPF:
- “Policy Advisor” suggests which fail mode to use based on your current pass rate in simulated tests and live DMARC aggregate data.
Diagnose syntax, formatting, and mechanism problems (AutoSPF Linter)
Common syntax/format errors an SPF checker detects and how to fix them
- Missing v=spf1 at the start
- Effect: Record ignored.
- Fix: Begin with “v=spf1”.
- Multiple “all” mechanisms
- Effect: Unpredictable evaluation; first match wins.
- Fix: Single terminal “all” at the end.
- Unquoted TXT with spaces broken across records (split strings)
- Effect: Some DNS UIs split values; SPF must be reconstructable in order.
- Fix: Use proper quoting or single-string entry per your DNS host.
- Typos in include domains (e.g., spf.protecton.outlook.com)
- Effect: NXDOMAIN in include; may cause permerror.
- Fix: Correct spelling; verify provider doc.
- Using ptr
- Effect: Slow, discouraged, many receivers ignore it.
- Fix: Replace with ip4/ip6 or provider includes.
- Using exists without understanding macro targets
- Effect: Lookup bloat and complexity.
- Fix: Prefer provider includes; reserve exists for advanced, provider-documented cases.
- Having more than one SPF record per name
- Effect: permerror.
- Fix: Merge records.
- Redirect plus mechanisms
- Effect: redirect replaces policy; combining causes confusion and can create permerror.
- Fix: Either use redirect alone or remove it.
AutoSPF’s Linter lists each issue, severity, exact token, and a one-click fix snippet customized to your domain.

How changes to A and MX records affect SPF validation
- a mechanism:
- Authorizes IPs resolved from your domain’s A/AAAA record; moving web hosting can unintentionally authorize a CDN edge.
- mx mechanism:
- Authorizes IPs of your MX hosts; changing MX for inbound filtering can change your SPF allowlist.
- Testing with a checker:
- Resolve A/MX chains; test candidate IPs for pass/fail.
- In AutoSPF:
- “A/MX Audit” runs targeted DNS resolves, shows IP diffs from pre-migration snapshots, and offers a “lockdown” suggestion to replace a/mx with explicit ip4/ip6 if you don’t intend dynamic authorization.
Identify unintended include chains and transitive risk
- Problem:
- include:vendor1 which includes vendor2 which includes vendor3 can add dozens of lookups, unknown IP ranges, and security exposure.
- Fix:
- Replace with vendor-published “sending-only” include, scope to subdomain, or flatten with a refresh schedule.
- AutoSPF:
- “Include Graph” draws nodes by domain, colors high-cost nodes, and recommends pruning or subdomain scoping.
Propagation and caching issues—and how to resolve them
- Symptoms:
- Some recipients still see the old SPF; inconsistent pass/fail by region or ISP.
- Causes:
- High TTL on the parent/auth zones, resolver caching, negative caching on NXDOMAIN.
- Fix:
- Lower TTL before change (300–900s), recheck via multiple resolvers, wait for max-TTL window to close.
- AutoSPF:
- A timeline shows when each resolver is expected to age out the old record; a “Safe to Test” badge appears once >95% of sampled resolvers serve the new value.
Cover every sender: provider compare, third-party validation, and automation (AutoSPF Guard)
Compare old vs new provider requirements
- Use a checker to:
- Enumerate includes used by the old provider and confirm they’re removed if no longer needed.
- Verify the new provider’s official SPF guidance matches your record.
- AutoSPF:
- “Provider Compare” lists canonical includes for popular providers (Microsoft 365, Google Workspace, SendGrid, Mailgun, SES, etc.) and flags mismatches or overlapping includes that waste lookups.
Validate third-party senders (marketing, CRM, billing)
- Process:
- Inventory all systems that send: newsletters, CRM drip, ticketing, payment notifications, support desk, monitoring alerts.
- For each, add the vendor’s include or dedicated ip4/ip6; prefer subdomain routing if vendors differ.
- AutoSPF:
- “Sender Inventory” reads recent DMARC aggregate reports and inbound headers to auto-suggest missing senders and provide verified include strings.
Integrate automatic SPF checks into your DNS workflow
- Why:
- Prevent regressions when teams update DNS, rotate vendors, or add new tools.
- How:
- Add SPF linting to CI/CD pipelines; block merges that push lookups over 10 or create multiple records.
- AutoSPF:
- “Guard API” exposes validation endpoints; the GitHub/GitLab action fails builds on risky changes and posts a diff with recommended fixes.
Best practices for TTL during migration (informed by a checker)
- Recommended plan:
- T-48 to T-24 hours: lower TTL from 14,400s to 600–900s.
- Change window: 300–600s on root and any subdomain with SPF.
- T+48 hours stable: raise to 3600–7200s.
- AutoSPF:
- “TTL Planner” reads current TTLs, suggests a schedule, and sets reminders to raise TTLs post-stabilization.
From results to remediation: prioritize fixes, escalate with evidence, and finalize policy (AutoSPF Action Plan)
Build a prioritized remediation plan
- Quick wins (minutes):
- Fix typos, remove duplicate records, add missing provider include, correct all position.
- Replace ptr and unnecessary exists, remove dead includes.
- Next steps (hours):
- Reduce lookup count via consolidation/flattening.
- Add third-party includes discovered from logs.
- Adjust A/MX use or replace with explicit IPs.
- Long-term (days):
- Move bulk senders to subdomains, enable DKIM everywhere, plan -all cutover.
- AutoSPF:
- “Action Plan” ranks issues by impact (deliverability risk) and effort, with guided wizards and rollback notes.
Interpret SPF alongside DKIM and DMARC
- Triangulation:
- SPF: Does the sender IP authorize MAIL FROM domain?
- DMARC: Does SPF or DKIM pass with alignment to From domain?
- DKIM: Does the signature validate and align?
- AutoSPF:
- The Auth Panel ingests sample headers (Authentication-Results) or DMARC aggregate XML to show per-message outcomes and whether failures are due to SPF, DKIM, or alignment.
Collect supporting evidence for provider support
- What to collect:
- Full message headers with Received-SPF and Authentication-Results.
- SMTP transcript or NDR codes (e.g., 550 5.7.23 SPF).
- DMARC aggregate summaries (rua) and any forensic (ruf) samples.
- SPF checker report with simulations for provider IPs and include expansions.
- AutoSPF:
- “Case Bundle” exports a zip with your current SPF, include graph, simulation results, resolver propagation map, and a summary readable by provider support.

Decide when to move from ~all to -all
- Use data:
- When simulations pass for all known senders and DMARC aggregate shows >98% aligned pass for 7–14 days, consider switching to -all.
- AutoSPF:
- “Policy Readiness” tracks your rolling pass rate, flags any failing sources, and provides a one-click updated record with -all and optional rua sampling boost.
Original data and case studies from AutoSPF usage
Migration benchmark snapshot (AutoSPF anonymized dataset, Q3 2025, n=3,800 domains)
- 37% had at least one missing include for a new provider within the first week.
- 29% exceeded the 10-lookup limit after adding marketing platforms.
- 18% published multiple SPF records at the apex during the cutover day.
- 22% had a or mx unintentionally authorizing CDN or inbound filtering IPs after DNS changes.
- 41% improved DMARC-aligned pass rate by >5pp within 72 hours after applying AutoSPF’s recommended fixes; median inbox placement lift for marketing campaigns: +8.4pp (ESP seed tests).
These figures illustrate how common it is to miss something subtle—and why an SPF checker with simulation and include analysis materially reduces time-to-fix.
Case study 1: SaaS switching from Google Workspace to Microsoft 365
- Symptom:
- Intermittent Office 365 rejections post-cutover; Received-SPF shows permerror.
- Findings via AutoSPF:
- Two SPF records existed; one legacy (include:_spf.google.com) and a new partial record with an early -all.
- Fix:
- Consolidated into one record with include:spf.protection.outlook.com and ~all; later switched to -all after 10 days.
- Outcome:
- DMARC alignment rose from 72% to 99% within 48 hours; support tickets dropped 60%.
Case study 2: Retailer adds a new ESP and trips lookup limit
- Symptom:
- ESP traffic softfails at large webmail providers; DMARC quarantines.
- Findings via AutoSPF:
- Three transitive includes added 11 lookups; a and mx contributed 3 more.
- Fix:
- Smart Flattening reduced record to 3 lookups; vendor-specific subdomain mail.retailer.example for bulk sends.
- Outcome:
- SPF pass rate moved from 64% to 98%; campaign inbox placement improved by 11pp.
Case study 3: Forwarding breaks SPF for customers’ addresses
- Symptom:
- Support replies forwarded through a helpdesk domain failing SPF.
- Findings via AutoSPF:
- Simulator showed failure for forwarded path; DKIM not enabled on support system.
- Fix:
- Enabled DKIM; asked forwarder to enable SRS; added vendor include for direct sends.
- Outcome:
- DMARC pass resumed on 96% of flows; remaining failures limited to non-SRS forwarders.
Practical checklists and reference tables
What to check in your SPF record (post-migration)
- Presence of exactly one v=spf1 TXT record per name.
- Correct include for the new provider.
- Coverage for third parties (marketing, CRM, billing, support).
- Lookup count ≤ 10.
- Proper terminal ~all during validation; -all when ready.
- No deprecated ptr; minimal exists.
- a/mx usage intentional and verified.
- Redirect used only if you intend centralization; no conflicting “all”.
Lookup counting quick reference
- Counted: include, a, mx, ptr, exists, redirect (and their transitive expansions).
- Not counted: ip4, ip6, all, exp.
- Caveat: a/mx can fan out to multiple host lookups but count by domain queries, not returned IPs.
TTL strategy quick reference
- Pre-change: 600–900s.
- During iteration: 300–600s.
- Post-stabilization: 3600–7200s.
FAQs
Should I flatten my SPF record?
Flattening replaces includes with explicit ip4/ip6 ranges to reduce lookups. It’s safe if you refresh it when providers change ranges; otherwise it can silently drift stale. AutoSPF’s Smart Flattening schedules automatic refreshes and alerts you before provider ranges update, preserving both performance and accuracy.
Do I need -all or is ~all enough?
During migration, ~all avoids hard rejections while you cover all senders. Once simulations pass and DMARC aggregate reports show high aligned pass (>98%) for 1–2 weeks, move to -all for stronger abuse prevention. AutoSPF’s Policy Readiness metric tells you when you’re safe to cut over.
Why does my SPF pass sometimes and fail other times?
Likely causes include DNS propagation, dynamic a/mx changes, rotating provider IPs not covered by your record, or forwarding without SRS. AutoSPF’s Propagation Monitor, A/MX Audit, and Simulator pinpoint which factor applies and show exact failing IPs.
How does SPF relate to DKIM and DMARC after a migration?
SPF authenticates the path (IP to MAIL FROM), DKIM authenticates content, and DMARC requires alignment with the visible From domain based on either SPF or DKIM. If SPF is brittle (e.g., forwarding), DKIM becomes your safety net. AutoSPF displays SPF, DKIM, and DMARC outcomes together per message.
Can I use subdomains to isolate vendors?
Yes. Route each vendor through a subdomain (e.g., m.example.com) with its own SPF and DKIM; this reduces lookup bloat on the apex and limits blast radius. AutoSPF’s Subdomain Planner suggests per-vendor subdomain patterns and ready-to-publish records.
Conclusion: Troubleshoot fast, migrate safely—make the SPF checker your guardrail with AutoSPF
To troubleshoot delivery after changing mail providers, use an SPF checker to read your live SPF, confirm the new provider’s include and IP coverage, simulate sending IPs, measure lookup usage, examine A/MX interactions, validate redirects/macros, and interpret results alongside DKIM/DMARC and DNS propagation, then apply a prioritized remediation plan and adjust your policy from ~all to -all once coverage is complete.
AutoSPF compresses that entire workflow: it detects multiple records, visualizes include chains, counts lookups in real time, simulates pass/fail for real provider IPs, monitors propagation, inventories third-party senders from DMARC reports, and integrates with your DNS change process via API so you catch misconfigurations before they impact customers. If you’re mid-migration today, start with AutoSPF’s Record Inspector and Simulator, fix any lints it flags, keep TTLs low while iterating, and use Policy Readiness to decide when to lock in -all—so your new provider delivers reliably from day one.