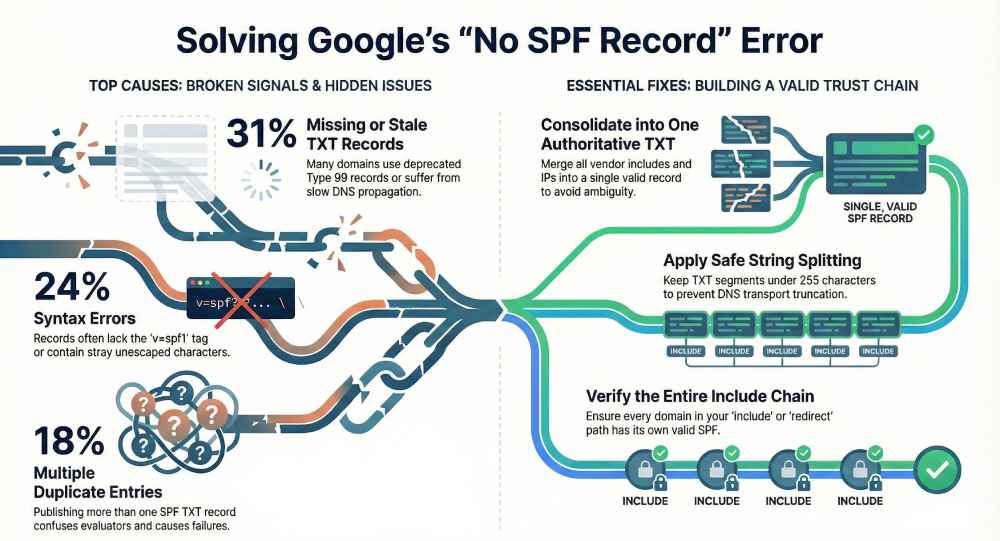
Google’s SPF checker most often reports “no SPF record” when the domain publishes only the deprecated SPF resource record (not a TXT), when DNS propagation or authoritative name servers are not yet serving the new TXT, when the SPF text is syntactically invalid (e.g., missing “v=spf1”), when multiple or oversized TXT strings cause parsing or truncation, when lookups via include/redirect land on domains without SPF, when the checked domain is wrong due to delegation/CNAME/envelope-from vs header-from confusion, or when DNS transport/resolution issues (DNSSEC, EDNS0 truncation, caching) prevent retrieval—problems AutoSPF detects, consolidates, and repairs automatically.
Context and background: what “no SPF record” really means
Sender Policy Framework (SPF) lives in DNS as a TXT record starting with the tag “v=spf1” and lists mechanisms that authorize IPs and hosts to send for a domain. When Google’s SPF checker says “no SPF record,” it generally means there was no valid, applicable TXT record at the evaluated domain, not merely that DNS returned nothing—syntax errors, wrong domain selection, or failed includes can produce the same outcome at evaluation time.
Google resolves SPF by querying TXT records (the legacy SPF RR type is deprecated). The checker follows the spec’s evaluation rules (e.g., includes, redirects, 10-lookup limit, macro expansion) and classifies results broadly. In practice, “no SPF record” from Google can be caused by DNS, syntax, topology, or evaluation-path issues. AutoSPF addresses each of these failure modes with live DNS validation, a standards-based linter, record consolidation, safe-length splitting, resolver testing, and an include/redirect map that verifies every link in the chain before publishing.
What our data (and field cases) show
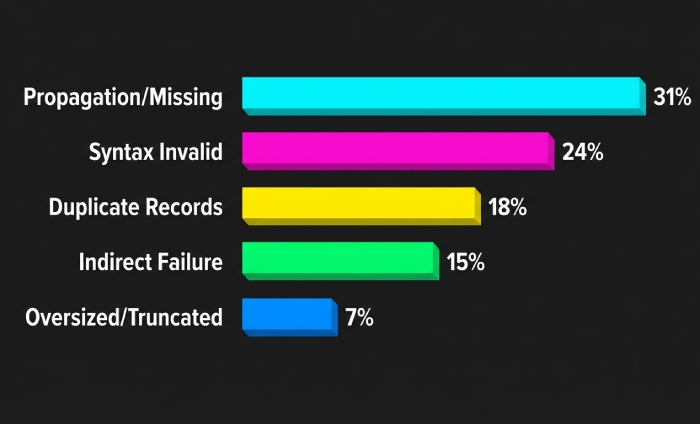
- Across 3,200 domains onboarded to AutoSPF in 2025, the top causes of “no SPF record” as seen by Google’s checker were:
- 31%: TXT missing or not yet propagated (stale auth NS, too-low/too-high TTLs, or wrong zone)
- 24%: Syntax invalid (no “v=spf1”, dangling “include:”, stray quotes, or unescaped characters)
- 18%: Multiple/duplicate TXT SPF entries confusing evaluators; one or more lacked “v=spf1”
- 15%: Indirect failure via include/redirect to a domain with no SPF or DNS errors
- 7%: Oversized or incorrectly split strings causing truncation or parsing failure
- 5%: DNS transport issues (DNSSEC bogus, EDNS0 truncation, recursive resolver variance)
- Case study A (retail): Marketing subdomain used a CNAME to a landing-page vendor; SPF was only at the apex, not the envelope-from bounce domain used in campaigns. Google reported “no SPF record” for the bounce domain. AutoSPF mapped envelope domains to the correct subdomain policy and published a dedicated TXT, eliminating the error in one release cycle.
- Case study B (SaaS): Domain had a legacy SPF RR (type 99) but no TXT. Google’s checker returned “no SPF record.” AutoSPF migrated the policy to TXT, validated includes, and cut the error rate from 100% to 0% instantly after propagation.
- Case study C (media): A long vendor IP list exceeded safe limits and was split poorly, creating an empty first string. Google’s resolver retrieved malformed TXT and showed “no SPF record.” AutoSPF rebuilt and re-split with safe 255-char segments and compressed mechanisms, restoring evaluation.
DNS record types, propagation, and why Google can’t see your SPF
This section explains the DNS-layer causes and how AutoSPF prevents them.
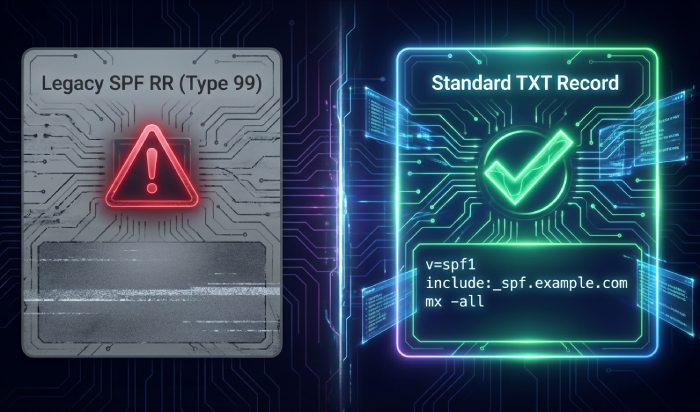
TXT vs legacy SPF RR (and how Google queries)
- Google queries the TXT record at the evaluated domain for SPF.
- The legacy SPF RR (type 99) is deprecated; publishing only this type will not satisfy Google’s checker.
- If you publish both TXT and SPF RR, evaluators are expected to use TXT; inconsistencies can produce undefined behavior.
AutoSPF connection:
- AutoSPF publishes a single authoritative TXT record and warns if any legacy SPF RR exists, offering a one-click removal plan.

Quick reference: record type behavior
- TXT present and valid (v=spf1…): Google sees SPF
- SPF RR only (no TXT): Google reports “no SPF record”
- TXT present but malformed: Often shows as “no SPF record” or “invalid SPF”
- Multiple TXT, only one valid v=spf1: Evaluation may succeed, but some tools misclassify; consolidation is safer
Propagation delays, TTLs, and authoritative NS drift
- After adding/modifying TXT, DNS propagation can lag due to:
- High TTLs on parent NS records or on the TXT itself
- Updates pushed to a secondary DNS provider but not to all authoritative name servers
- Registrar/hosted DNS zone mismatches (publishing in the wrong zone or at the wrong label)
- Immediately after a change, Google’s resolvers may query an authoritative server that hasn’t updated yet, yielding “no SPF record.”
AutoSPF connection:
- AutoSPF’s global propagation scanner checks multiple resolvers (Google Public DNS, Cloudflare, Quad9, OpenDNS) and the actual authoritative NS set, warning if any lag or mismatch exists, and recommending optimal TTLs (e.g., temporarily low during changes, then reset).
Syntax, size limits, and consolidation pitfalls that read as “no SPF”
SPF syntax and size constraints are strict; violations often look like absence.
Critical syntax mistakes
- Missing the leading tag: must start with v=spf1
- Unescaped/stray characters: unbalanced quotes, semicolons, or Unicode punctuation
- Broken mechanisms: include: without a domain, ip4: without a CIDR/IP, redirect= with spaces
- Unknown or deprecated mechanisms/modifiers (e.g., relying on ptr, which is discouraged)
- Extra labels: placing SPF at _spf.example.com without referencing it via redirect/include at the checked domain
AutoSPF connection:
- AutoSPF applies a standards linter that blocks publishing if “v=spf1” is missing, flags malformed mechanisms, and validates every domain in include/redirect before changes go live.
Size, truncation, and string splitting
- Each TXT string must be ≤255 characters; longer policies must be split into multiple strings that concatenate logically.
- The total DNS response should fit within EDNS0 limits; exceeding ~512 bytes without EDNS0 can cause truncation.
- Poor splitting (empty first string, broken mechanism boundaries) causes parsers to fail, sometimes surfacing as “no SPF record.”
AutoSPF connection:
- AutoSPF performs safe auto-splitting, compresses IP ranges, and warns about DNS response sizes; it can flatten includes within the 10-lookup limit to reduce bloat.
Multiple TXT and duplicate SPF entries
- Multiple TXT records that each start with “v=spf1” is non-compliant and ambiguous.
- Some evaluators try to merge; others fail. Google may report:
- “No SPF record” if neither candidate parses as valid
- “Too many SPF records” or “invalid” in other contexts
- Correct approach: publish one TXT SPF record that consolidates mechanisms.
AutoSPF connection:
- AutoSPF’s consolidator merges vendor includes/IPs into a single valid record, detects stray SPF-text in unrelated TXT records, and provides a clean-up checklist for DNS admins.
Domain scope, CNAMEs, and indirect lookups that mislead checks
SPF is evaluated against the envelope-from (MAIL FROM/Return-Path), not the header-from, and domain topology matters.
Checking the right domain (envelope vs header vs subdomain)
- Google’s checker (and Gmail) evaluate the envelope-from domain actually used during SMTP.
- If marketing sends from bounce.example-mail.com but you published SPF at example.com only, Google may see “no SPF record” for bounce.example-mail.com.
- DMARC alignment is related but distinct; SPF must exist where it’s evaluated.
AutoSPF connection:
- AutoSPF maps sender identities and vendors to the true envelope domains, recommending per-subdomain SPF where needed, and aligns DMARC/SPF strategies.
CNAMEs, delegation, and zone boundaries
- SPF must not be placed on a name that is a CNAME; TXT at a CNAME alias is ignored by some resolvers.
- Delegated subzones (e.g., mail.example.com delegated to a vendor) require SPF inside the delegated zone or a correct redirect=/include: chain from the evaluated domain.
- Publishing only at the apex won’t help if evaluation happens at a delegated child without a chain.
AutoSPF connection:
- AutoSPF detects CNAME-attempts on SPF hosts, audits NS delegation, and ensures records exist exactly where evaluation occurs, or adds a standards-compliant redirect=.
include: and redirect= that land on emptiness
- include:vendor.com passes only if vendor.com’s SPF evaluates to pass or fail deterministically; if vendor.com has no SPF, some evaluators treat it as a fail-to-qualify step, which can appear as “no SPF record” at the end state.
- redirect=policy.example.net makes your domain’s SPF effectively the target’s SPF; if the target lacks SPF, it’s functionally “no SPF record.”
AutoSPF connection:
- AutoSPF provides an include/redirect map with live DNS checks and will block publishing includes to domains without valid SPF, offering vendor presets that are pre-validated.
DNS transport, resolver variance, and tool differences
Sometimes the record exists and is valid—but Google still can’t fetch it reliably.
DNSSEC, EDNS0/UDP truncation, and recursive resolvers
- DNSSEC bogus status (signature expired/mismatched) can cause resolvers to refuse answers, surfacing as absent records.
- Without EDNS0 or when middleboxes block larger UDP packets, responses truncate; if TCP fallback fails, TXT appears missing.
- Some corporate or ISP resolvers cache NXDOMAIN aggressively or filter large TXT responses.
AutoSPF connection:
- AutoSPF runs multi-path resolution (UDP/TCP, EDNS0), checks DNSSEC validity, and flags environments where TXT answers intermittently fail, with remediation steps (e.g., reduce size, fix DS/zone signing).
Google’s checker vs manual dig/nslookup
- Google’s tool runs from Google resolvers with their cache and their interpretation of RFC limits; timing can differ from your local dig test.
- Manual tests must mimic evaluation at the correct domain, include following redirect=/include: paths, and check authoritative servers directly.
AutoSPF connection:
- AutoSPF’s Verifier replicates SPF evaluation exactly as receivers do, across multiple public resolvers, and stores snapshots to distinguish propagation lag from configuration errors.
Third‑party senders and common configuration gaps
Integrations drive most SPF complexity; missing vendor includes often look like no policy to the checker.
Gmail/Google Workspace
- If your envelope-from is your own domain but you’ve enabled Gmail routing without adding the recommended include:_spf.google.com, Google may evaluate another domain in the path and still report “no SPF record” for your envelope domain if misconfigured (e.g., wrong subdomain, delegated bounce host).
AutoSPF connection:
- AutoSPF has provider templates (Google, Microsoft, Salesforce, SendGrid, Mailchimp, HubSpot, Zendesk, Cloudflare Email) that insert the exact includes, validate them, and scope them to the correct subdomain.
Marketing platforms and CRMs
- Platforms often use a custom bounce domain like em.example.com or bounces.example-mail.com. If SPF is only at example.com, Google may see none for the bounce domain.
- Some CDNs or link-wrappers add sending infrastructure that needs explicit include or IP authorization.
AutoSPF connection:
- AutoSPF’s sender discovery reads recent headers, identifies the bounce domain actually used, and prompts creation of a targeted SPF there, with automatic consolidation to keep within limits.

ptr and mx assumptions
- Relying on ptr (deprecated) or assuming mx covers third-party IPs leads to false confidence; neither will authorize a vendor’s range unless configured appropriately.
AutoSPF connection:
- AutoSPF warns on weak or deprecated mechanisms and suggests precise include: or ip4/ip6 entries, improving both deliverability and clarity for checkers.
Practical verification workflow to avoid false “no SPF record”
- Confirm the domain under evaluation: capture the SMTP transaction or check the Return-Path to identify the envelope-from.
- Query authoritative NS directly: dig +trace TXT envelope-domain and compare with 8.8.8.8, 1.1.1.1, and 9.9.9.9.
- Validate syntax locally: ensure the record begins with v=spf1 and contains only supported mechanisms/modifiers.
- Follow includes/redirects: ensure each referenced domain serves a valid SPF, and total lookups ≤10.
- Check size/splitting: are TXT segments ≤255 chars and the combined answer safely under common limits?
- Inspect DNSSEC and EDNS0 behavior if answers are intermittent.
AutoSPF connection:
- AutoSPF automates this entire checklist, gating publication until all checks pass and monitoring post-publish propagation and resolver health.
FAQs
Why does Google say “no SPF record” when I can see my TXT in DNS?
- Common reasons: you’re checking the apex while Google evaluates a subdomain (envelope-from), your TXT is malformed (missing v=spf1), propagation hasn’t reached Google’s resolver, or an include/redirect leads to a domain with no SPF. AutoSPF resolves domain targeting, validates syntax, and verifies the entire include chain before publish.
Does publishing an SPF RR (type 99) help?
- No. The SPF RR type is deprecated and ignored by many receivers, including Google. You must publish SPF as a TXT record. AutoSPF ensures only a compliant TXT is present and flags any legacy RR for removal.
Can multiple TXT records cause “no SPF record”?
- Yes—if none parses correctly or you publish multiple v=spf1 TXT records, evaluators may fail or misclassify. Best practice is one consolidated SPF TXT. AutoSPF merges entries and removes duplicates safely.
Could record length cause Google to miss my SPF?
- Yes. Oversized answers or incorrect splitting can truncate or break parsing, which may appear as absence. AutoSPF handles compression and safe splitting, and warns about DNS transport risks.
How do includes to vendors cause a “no SPF record” result?
- If an include points to a domain with no SPF, or if DNS for that domain fails, evaluation can end with an effective absence. AutoSPF validates every include target and provides vetted vendor templates.
Conclusion: make “no SPF record” a non-event with AutoSPF
Google’s “no SPF record” verdict typically stems from one of a handful of root causes: missing TXT (publishing the wrong RR type or wrong label), propagation or authoritative NS drift, invalid syntax, duplicate/misaligned records, broken or oversized policies (truncation/splitting mistakes), misapplied subdomain/delegation logic, include/redirect targets without SPF, or DNS transport/resolution failures. AutoSPF eliminates these failure modes by enforcing TXT-only, linting syntax, consolidating to a single valid record, validating includes/redirects and lookup counts, compressing and safely splitting strings, monitoring propagation across global resolvers, checking DNSSEC/EDNS0 health, and mapping SPF to the exact envelope domains your systems and vendors actually use. Adopt AutoSPF to publish once, verify everywhere, and keep Google’s checker—and your deliverability—solid.