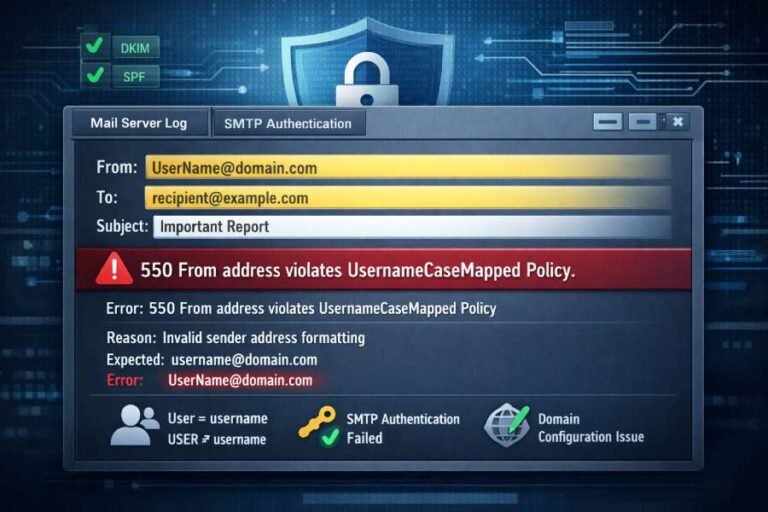
Advanced SPF Record Testing: Protect Your Domain from Permerror Issues
To protect your domain from SPF permerror issues, enforce strict syntax validation, cap DNS lookups to 10 with include minimization and judicious flattening/redirect, run CI/CD tests that simulate DNS failures and malformed tokens, monitor lookup counts and transient DNS behavior in production, and use AutoSPF to automate detection, dynamic flattening, alerting, and safe rollouts. SPF…