In today’s email-driven world, securing your domain’s email communication is non-negotiable. Cyber threats like spoofing, phishing, and unauthorized senders are constantly evolving, and relying on default email systems without proper authentication puts your business reputation, deliverability, and customer trust at risk.
At AutoSPF, we specialize in empowering IT teams, MSPs, and domain owners with clear, actionable guidance for email authentication standards — especially SPF and DKIM configuration. In this comprehensive guide, we dive into how to properly configure SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) for Proofpoint Essentials environments, why this matters, and how to avoid common pitfalls.
Why Email Authentication Matters in 2025
Before we dig into configuration steps, let’s establish why this is essential.
Email authentication protocols like SPF, DKIM, and DMARC work together to:
- Prove authenticity for email senders
- Reduce fraud and spoofing
- Improve deliverability
- Protect brand trust
- Support compliance with major email providers like Google, Yahoo, Microsoft, and others
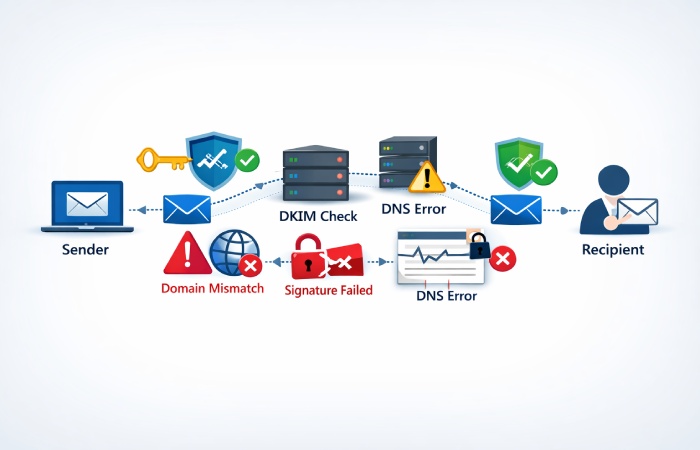
SPF verifies which mail servers are allowed to send on behalf of your domain. DKIM adds a cryptographic signature that validates email integrity and origin. Together, they help your domain pass DMARC checks — which is crucial for passing modern spam filters and protecting recipients.
Additionally, many large providers (Gmail, Yahoo) now require both SPF and DKIM to be configured before they will fully trust and deliver your mUnderstanding SPF and DKIM in Proofpoint Essentials
🔹 SPF (Sender Policy Framework)
SPF is a DNS record that contains a list of all authorized mail senders for your domain. When an email is received, the receiving server checks the SPF record to confirm the sending server is authorized.
If your SPF is misconfigured or missing, your emails:
- May fail authentication
- Could be redirected to spam or rejected
- Might hurt your domain’s reputation
With Proofpoint Essentials, you must include Proofpoint’s sending infrastructure in your SPF record so that emails passing through Proofpoint are recognized as legitimate.
🔹 DKIM (DomainKeys Identified Mail)
DKIM adds a signature to the header of outgoing emails. This signature is generated using a private key and checked against a public key published in DNS. If the keys match, the email is confirmed to be unaltered and authentic.

With Proofpoint Essentials, DKIM requires:
- Generating a signing key in the Proofpoint admin console
- Publishing the accompanying public key in your DNS zone
- Verifying that Proofpoint confirms the DNS entry
This ensures outbound messages can be validated by receiving servers.
How SPF and DKIM Work Together
Individually, SPF and DKIM are valuable. But when paired with DMARC, they provide powerful defense:
- SPF checks IP authorization
- DKIM validates header integrity
- DMARC enforces alignment and policy decisions based on SPF/DKIM results
Most modern email providers will only fully trust your domain if both SPF and DKIM are correctly implemented and aligned.
Step-by-Step Configuration: SPF in Proofpoint Essentials
Below is a detailed walkthrough for configuring SPF for your Proofpoint Essentials domain.
✅ Step 1: Document Your Email Sources
Before you make any DNS changes, take an inventory of all systems that send email on behalf of your domain:
✔ Proofpoint Essentials
✔ Marketing platforms (e.g., MailChimp, SendGrid)
✔ Office 365 / Microsoft 365
✔ CRMs or internal systems
✔ Transactional email services

This ensures you include all legitimate senders in your SPF record to avoid accidental failures.
✅ Step 2: Log Into Your DNS Provider
Navigate to the DNS dashboard where your domain’s DNS records are hosted (GoDaddy, Cloudflare, AWS Route53, etc.).
✅ Step 3: Create or Update the SPF TXT Record
If you have an existing SPF record (begins with v=spf1), you will modify it. If not, you will create a new one.
Example record with Proofpoint Essentials included:
v=spf1 include:dispatch-us.ppe-hosted.com ~allFor domains served out of Europe (EU), you may need:
v=spf1 include:dispatch-eu.ppe-hosted.com ~allKeep in mind:
- Only one SPF record is permitted per domain
- Include all legitimate sending sources with include: mechanisms
- The final term (~all, -all, etc.) determines the strictness
Allow up to 72 hours for DNS propagation.
Common SPF Config Mistakes
❌ Multiple separate SPF records
❌ Exceeding DNS lookup limits
❌ Forgetting to include third-party providers
❌ Updating DNS without verifying propagation
DKIM Configuration in Proofpoint Essentials
While SPF authorizes servers, DKIM validates the message itself.
Let’s walk through how to set this up:
✅ Step 1: Generate DKIM Keys in Proofpoint Essentials
Log into the Proofpoint administration dashboard and navigate to:
Administration → Account Management → Domains
From here:
- Select your domain
- Click the vertical ellipsis next to it
- Choose Configure DKIM
- Generate a new signing key
At this point, Proofpoint creates:
- A selector (identifier used in DNS)
- A public key you must publish to DNS
This step ensures outbound messages can be cryptographically verified.

✅ Step 2: Publish the DKIM Public Key in DNS
In your DNS provider’s panel:
- Create a new TXT record
- Enter the DKIM hostname (a combination of the selector and _domainkey)
- Paste the public key value exactly as given
This process ensures receiving servers can validate the DKIM signature.
✅ Step 3: Verify the DKIM Record
After publishing, go back to the Proofpoint dashboard and click Verify Key. If successful, Proofpoint will begin signing outgoing messages for this domain.
Once verified, outbound DKIM signing is active.
Best Practices After Configuration
✔ Use online tools (like SPF/DKIM checkers) to verify correctness
✔ Monitor DMARC reports to track authentication results
✔ Regularly update records when sending sources change
✔ Use relaxed alignment modes initially to minimize delivery issWhy DKIM Matters Even If SPF Is Present
Some email forwarding or intermediate gateways can break SPF authentication (because SPF checks the path). In contrast:
DKIM survives message forwarding because the signature stays intact — so it is your most resilient authentication method in complex email flows.
Aligning Proofpoint Authentication with Modern Standards
In recent years, email providers and standards bodies have emphasized that authentication must be aligned — meaning the domain in SPF and DKIM should match the visible “From:” domain in the email. This is critical for DMARC compliance and deliverability.

What Happens If You Don’t Configure SPF & DKIM
If SPF and DKIM aren’t configured properly:
🚫 Emails may land in spam folders
🚫 Domain reputation can suffer
🚫 Your domain may get flagged for spoofing
🚫 You lose visibility into failed delivery/authentication
Major inbox providers may even block your messages entirely.
Testing and Monitoring
Once your records are published:
🔹 Use DNS lookup tools
Test your SPF and DKIM TXT entries for syntax and propagation.
🔹 Turn on DMARC reporting
Enable RUA/RUF reporting to receive authentication feedback from receivers.
Monitoring is the key to long-term success. By regularly reviewing reports, you can detect issues early and adjust records as needed.