Every year, cybersecurity enthusiasts celebrate October as the month of awareness. It is the time when we remind ourselves that digital safety is not limited to just installing antivirus software or using a strong password. Rather, online safety is about cyber education—the knowledge of how to detect a potential threat attack, stop it, and report it to relevant authorities before they gain access to your personal data.
And one of the biggest threats in the world of cybersecurity is phishing. This age-old cybersecurity tactic has evolved 180 degrees over the last few decades. Phishing scams are no longer just full of spelling mistakes and bad grammar, but now include polished, AI-generated emails that look completely real.
It is 2025, and phishing actors are highly skilled and have access to state-of-the-art tools. The scams are smart, hyper-personalized, and way harder to detect and evade.
This article explores the intricacies of phishing in 2025 and the steps and tricks to protect yourself and your business from phishing scams.

What is phishing?
One of the most common and oldest yet successful forms of cyberattack, phishing is an online cybercrime where threat actors pretend to be legitimate individuals or organizations who try to trick the victim into sharing personal details like passwords, user IDs, and financial data.
Phishing scams take place through malicious emails, SMS, social media DMs, and phone calls.
Phishing landscape in 2025
In 2025, the phishing game has gone to a whole new level. Easy and affordable access to AI has literally opened the floodgates of opportunities for phishing actors. They can now easily come up with believable, compelling, grammatically perfect, and contextual messages. In simpler words, phishing attacks in 2025 have become faster, hyper-targeted, and believable.

Phishing attacks in the workplace
Business enterprises are one of the major targets of phishing actors because even a single compromised employee can open the door to the entire network of the organization. Phishing scams in workplaces often look like:
- Payment requests or invoices from a threat actor who poses as a trusted vendor
- Fake HR emails asking employees to share or update their personal details
- Urgent IT messages asking the employees for a quick password reset via a malicious link
The hybrid and remote work culture has further made it convenient for phishing actors to exploit employees.
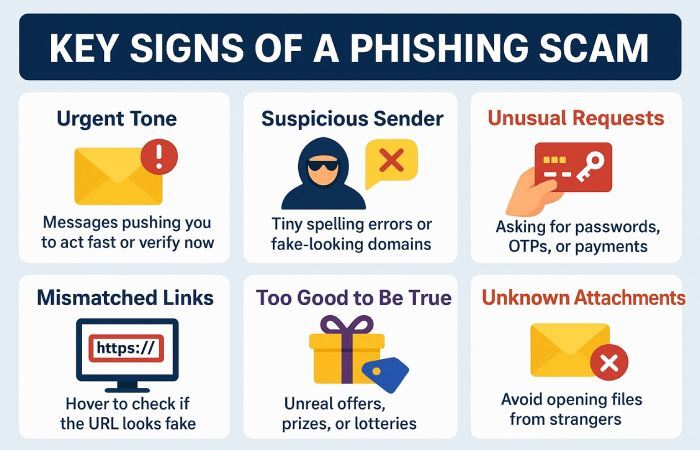
Common red flags to identify potential phishing scams
Below are some warning signs that you must never take lightly:
Element of urgency
Emails that carry the sense of extreme urgency and contain words like “act immediately” or “verify now otherwise…” are highly likely to be coming from phishing actors.
Suspicious email address
Make sure that the sender’s email address doesn’t contain even a single misplaced letter. Keep an eye out for domain changes as well.

Unusual requests
Always remember that if an email is asking you to share payment details, passwords or OTPs, then in all probability, it is coming from a threat actor.
Mismatched links
Before clicking on any link, hover over it. If you notice any mismatch between the sender’s website and the URL, then it can be a malicious link.
Too good to be true
If the message claims that you have won a lottery out of the blue, or offers you a meeting with a celebrity you absolutely adore, go through the email content again. Most probably, it is a phishing scam trying to mint money from you by abusing your preferences.
Extremely personal
If the emails seem overly personal and the details sound highly relevant, then take a step back. Maybe the scammers have gathered your data from social media to convince you to share your sensitive details.
Attachments from unknown senders
If you don’t know the sender of the email, then you MUST NOT download or open any attachment, as it can be dangerous malware.
How to safeguard your data from phishing scams
Now that you know how to identify a potential phishing scam, your next job is to protect your data from phishing actors. Here’s how to do that:
- Turn on the MFA (Multi Factor Authentication) system.
- Avoid using public wi-fi for carrying out any financial transactions.
- Update your device software from time to time.
- Invest in good-quality anti-virus software.
- Back up your data on a regular basis.
- Trust your instincts, and if anything feels off, then avoid doing it at any cost.
- Organizations should conduct simulated phishing drills from time to time to spread awareness.
- Limited access control can be a great way to safeguard sensitive business data.

Enhance your email security by enabling automatic SPF flattening, implementing SPF, DKIM, and DMARC authentication, and ensuring that all incoming emails are verified against trusted senders.
Final thoughts
The success rate of phishing scams is high because threat actors have finally cracked the code to manipulating your trust. But being proactive, mindful and aware can actually make your data phishing-proof. Remember that we are living in a world where threat actors are getting smarter- one phishing attack at a time. So, staying cyber aware is not smart; it is non-negotiable.
How are you celebrating Cyber Awareness Month 2025?






