SPF prevents spoofing by ensuring that only trusted sources can send emails using your domain. But for it to work well, the SPF record must be error-free. However, the problem is that SPF records are highly sensitive and can easily break if not managed carefully. A broken SPF record not only attracts phishing attacks but also hinders email deliverability, potentially damaging your domain’s reputation in the eyes of email service providers. Hence, it’s important that you regularly run your SPF record through credible lookup tools to discover if it has any errors and fix them at the earliest.
This blog focuses precisely on what all errors you can expect and how to resolve them easily.

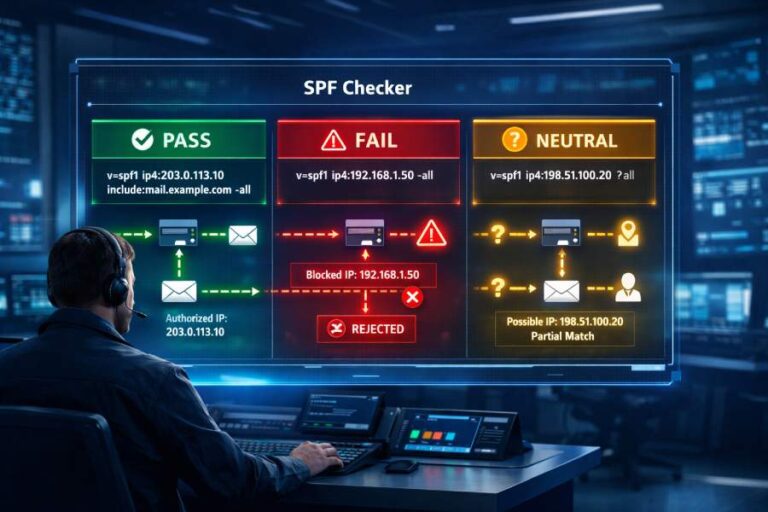
How does SPF work?
SPF works using a DNS TXT record that tells receiving mail servers which servers are allowed to send emails on behalf of your domain. So, when the receiving server gets the email, it checks the domain in the envelope “MAIL FROM” address and looks up its SPF record.
If the sender’s mail server is listed in the SPF TXT record, the email passes the verification checks and is placed in the inbox. If not, the result could be a Soft Fail, Hard Fail, or neutral—depending on how the record ends (like ~all or -all).
6 Common SPF errors and how to fix them
As stated at the beginning of the article, SPF is highly sensitive. Even a slight misconfiguration can trigger temporary or permanent errors. Here are the ones usually detected during a lookup.

1. Syntax error
The possible syntax errors are-
- Invalid mechanisms or qualifiers: e.g., writing ‘ip’ instead of ‘ip4’ or ‘+include’ instead of just ‘include.’
- Missing required elements: like forgetting the v=spf1 prefix.
- Malformed IP addresses: e.g., ip4=192.168.0.256 (invalid IP).
- Unescaped special characters: like @, ?, or spaces in the wrong places.
Here is how you can fix these-
- Always use valid SPF mechanisms, such as ‘ip4,’ ‘ip6,’ ‘include,’ ‘a,’ or ‘mx.’ Avoid unnecessary qualifiers like ‘+’ before mechanisms—SPF treats them as defaults, so ‘include’ is sufficient (not ‘+include’).
- Every SPF record must start with v=spf1. Without this prefix, the record won’t be recognized as a valid SPF entry. Always begin your record with this version tag.
- Double-check that all IPs in the ip4 or ip6 mechanisms are correctly formatted. Tools like MXToolbox or SPF Record Checker can validate IP formatting for you.
- Avoid using characters like @, ?, or extra spaces within the SPF record. Stick to standard SPF syntax and use quotes in your DNS settings if needed to prevent formatting issues during publishing.
2. Use of deprecated or risky mechanisms
It’s not encouraged to use deprecated mechanisms like ‘ptr’ and ‘exist’ in your SPF record. The ‘ptr’ mechanism is discouraged because it’s unreliable and can slow down email delivery, while ‘exist’ is complex and often leads to excessive DNS lookups. To avoid these issues, it’s best to remove or replace them with more stable options like ‘ip4,’ ‘a,’ or ‘include,’ which are widely supported and easier to manage.
3. Existence of multiple SPF records
Only one SPF record is allowed per domain. So, if you detect multiple ones, merge them into a single valid record. Please note that you can’t simply copy and paste them into a single string; you must ensure that no mechanism is repeated and that everything is syntactically correct.
4. Exceeding the character limit
SPF records have a strict character length limit— each string should be within 255 characters, and the total SPF record should not exceed 512 characters. If these limits are exceeded, the record gets truncated, causing verification issues.
To fix it, simplify the record by removing unnecessary or redundant mechanisms. You may also consider consolidating IP ranges.
5. Missing the ‘all’ mechanism
An SPF record without a final ‘all’ mechanism is considered incomplete and may lead to inconsistent handling of unauthorized emails. The ‘all’ mechanism—such as ‘-all,’ ‘~all,’ or ‘?all’—tells receiving mail servers what to do if a sender isn’t listed in the SPF record.
If you skip the ‘all’ mechanism in your SPF record, it confuses the receiving mail server—it won’t know what to do with emails from unauthorized sources. This can make it easier for fake or spoofed emails to get through. To avoid this, always end your SPF record with a clear rule. Use ‘-all’ if you want to strictly block all unauthorized emails, or ‘~all’ if you prefer a softer approach that allows monitoring without outright rejection.

6. Exceeding the DNS lookup limit
SPF allows a maximum of 10 DNS lookups per check, which includes mechanisms like ‘include,’ ‘a,’ ‘mx,’ ‘ptr,’ and ‘redirect.’ If your record crosses this limit, it results in a ‘permerror’ (permanent error), causing SPF authentication to fail—regardless of whether the sending source is legitimate.
To resolve this issue, reduce the number of lookups by removing unnecessary ‘include’ mechanisms, combining IP addresses under ip4/ip6, and avoiding the use of the deprecated ‘ptr’ mechanism. Additionally, you can use our automatic SPF flattening tool, which works by replacing lookups with direct IP addresses. This keeps your SPF record within the lookup limit while preserving its functionality.
Contact us if you need our assistance in flattening your SPF record.