
Did you know that email was never meant to be secure because cybercriminals were never meant to target it in the first place?
When email came into being, back in the 1970s, it was designed with just one intent— to make communication quick and seamless. Security was not even a question; perhaps this is why the original Simple Mail Transfer Protocol never bothered with identity validation or encryption. Its main job was to direct messages between servers efficiently while assuming that anyone sending email was who they claimed to be.
But as you know, in today’s modern digital ecosystem, this is no longer the case. Communication is getting more complex, cybercriminals are becoming smarter, and attacks are becoming more sophisticated. That’s why it became clear to security teams that their email ecosystems could no longer be protected by trust alone; they needed something systematic and robust. And that’s how the foundations of modern email authentication were laid.
In this article, we take you through the history of email authentication, how it came to be, and how these protocols evolved over the years.

What makes emails insecure?
It goes without saying that email has become a prime target for attackers. This is not only because it is convenient, but also because email has now become almost ubiquitous, which means it gives attackers a way in to reach any company, individual, or institution across the world, often bypassing physical and network defenses entirely.
But what makes your outgoing emails so vulnerable?
Protocol weakness
As we discussed earlier, when email was created, the core mail protocols were built for reach and speed, not security, because they operated inside trusted academic and government networks like ARPANET. At that time, unauthorized users couldn’t freely access the system, so verifying sender identity or encrypting messages wasn’t part of the original protocol design.
It was in the 1990s that real encryption began as SSL came into being, which then evolved into TLS for securing mail servers. The real concern then became that even after 20+ years of TLS support, there was a major gap in email encryption across the world.
Service Provider & Endpoint Weaknesses
After the inherent loopholes of how email was designed, the next big area that causes a gap in security is the way email service providers (ESPs) and endpoints handle emails. Even though using major service providers like Gmail, Yahoo, and Outlook does not raise any concerns as they feel secure and easy to use, they are still built on top of the same old email protocols that were never meant to deal with modern cyberthreats.
The reason that these ESPs become a major threat vector is that they store an enormous amount of sensitive information; everything from personal conversations to financial details and business data. This makes them a lucrative target for attackers. Let’s say, if someone finds a way to your company’s email account, they will instantly gain access to all the important and sensitive information that they could use to launch further attacks.
Human weaknesses
There might be gaps in how email operates, but another factor that makes email truly vulnerable is how we ourselves use email. This is because attackers know that it’s easier to bypass people than to bypass technology. Instead of trying to break complex security systems, they simply craft emails that trick users into clicking a link, downloading a file, or sharing sensitive information.

This is exactly why phishing attacks become so common. They use familiar names, urgent language, and official-looking branding to push people into quick decisions.
How did email security come into the picture?
As the email ecosystem became more dynamic and complex, it became easier for attackers to slip into conversations, impersonate trusted senders, and take advantage of the gaps in how email was originally built. So clearly, it became a prime target for attackers, not because email was flawed by design but because people and businesses started relying on it for almost everything. Attackers quickly noticed that one believable email could make someone send money, share private information, or give access to important systems.
This is when security teams realised that it is now more important than ever to have a proper way to verify who was actually sending an email, and that’s how email authentication came into being.
How did email authentication evolve: SPF, DKIM, and DMARC?

As we know, email was never meant to be secure; as such, it was only meant to make communication easier. But by the early 2000s, organizations realised that email’s native security features cannot stand a chance against modern cyberattacks. Attacks like phishing, domain spoofing, and fraudulent emails became so severe and sophisticated that organisations could no longer rely on guesswork ormanual checks to figure out which emails were real. There had to be a way for receiving servers to confirm whether an email was actually sent by the domain it claimed to come from. And that’s how the first generation of email authentication protocols, SPF, DKIM, and DMARC, began to take shape.
Now, let’s dig deeper to understand how each of these protocols evolved.
Sender Policy Framework (SPF)

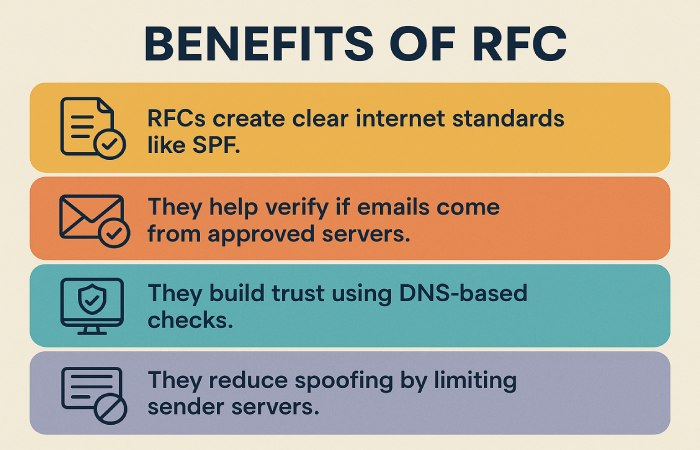
SPF was first introduced in the early 2000s when email spoofing became a common problem, and the receiving server needed a way to check whether an email was actually sent from an approved source. With SPF, a domain can publish a list of servers that are allowed to send email on its behalf.
By 2004, the name Sender Policy Framework (or SPF) was officially agreed upon, and in 2006, it became a formal Internet standard through an RFC. The idea behind SPF was simple: if you own a domain, you should be able to publish a list of servers that are allowed to send email for that domain. Since only the domain owner can make DNS changes, this list can act as a trusted reference for the receiving server to check against whenever an email arrives. If the email is sent from an approved list, the receiving server treats it as genuine.
DomainKeys Identified Mail (DKIM)
Another problem that gripped the industry in the early 2000s was header spoofing, where attackers change the visible “From” information in an email to make it look like it came from someone trustworthy. This made it very easy for the scammers to fool recipients into believing that the email was sent by a genuine person or organisation, even when it wasn’t. To tackle this issue, Yahoo and Cisco developed two separate solutions in 2004, which were later merged and we now know them as DKIM.
DKIM introduced a way for organisations to add a digital signature to their outgoing emails. When an email is sent, the sender’s system signs certain parts of the message and publishes a matching public key in their DNS. The receiving server then uses this key to check if the email really came from the claimed domain and whether it stayed unchanged during delivery.
When DKIM was introduced, it worked as an added layer of protection on top of what SPF could do. With SPF in place, the receiving servers could check whether the email was sent from an authorised server. And now with DKIM in the picture, they could also ensure that the email wasn’t changed along the way. This made it much harder for the attackers to spoof domains or tamper with your outgoing emails.

Domain-based Message Authentication, Reporting and Conformance (DMARC)
To ensure well-rounded protection for outgoing emails, a new protocol was introduced that built on SPF and DKIM. This led to theintroduction of DMARC in 2012. The authentication protocol worked to bring together both SPF and DKIM, and added a clear set of rules that told receiving servers what to do if an email failed either check. With DMARC, as a domain owner, you could finally decide whether suspicious emails should be allowed, sent to spam, or rejected completely.
Another notable feature of DMARC is its reporting, which has made a significant mark in the email security landscape. These reports provided insights into how your domain was being used across the internet, which emails passed authentication, which failed, and whether any unknown or unauthorised servers were attempting to send emails using your domain name.

What should you do today?
Clearly, we have come a long way since the inception of email back in the 1970s, but let’s not forget that cybercriminals have also become smarter and more creative. Even with modern authentication protocols like SPF, DKIM, and DMARC in place, attackers continue to find new ways to exploit gaps in configuration, user awareness, and outdated systems. This is why it is important to see email authentication not as a one-time setup but as an ongoing process that requires regular attention and updates. While implementing SPF, DKIM, and DMARC for your domain, make sure that you review them regularly and update your configurations whenever you add new tools or services that send email on your behalf, or you want to tighten your approach.
To get started with your authentication journey, reach out to us!






