Email channels were never considered a safe means of communication, and with the growing sophistication of artificial intelligence and machine learning, they’re being exploited even more.
That’s the reason why a staggering 93% of organizations are now planning to strengthen their email security, driven by the rising threat of AI-powered phishing attacks.
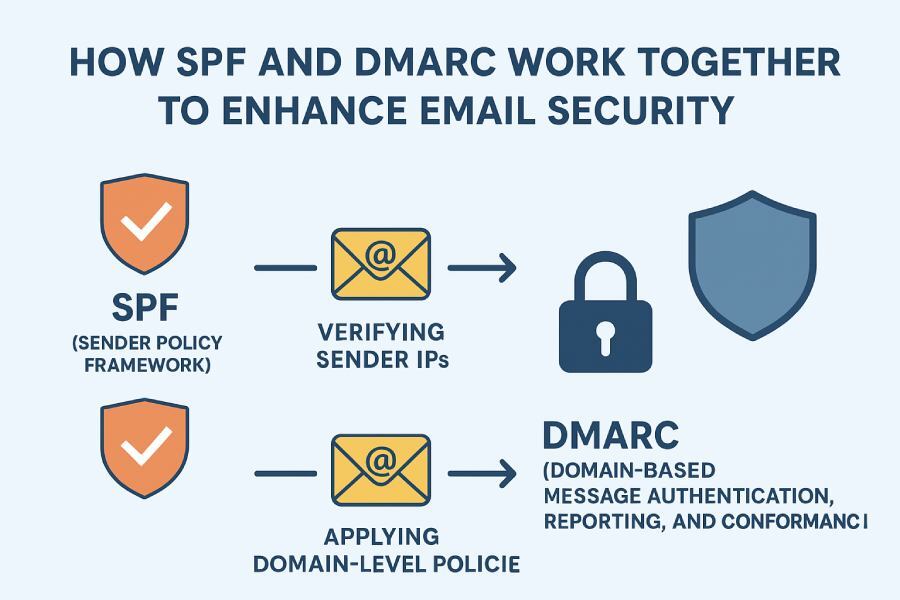
This is in situations like this where the powerful combination of SPF and DMARC works together to form a critical and proactive defense layer that essentially prevents threat actors from succeeding in email spoofing and phishing attacks attempted in your company’s name. This blog explains how that is done.

The basics of SPF
Your domain is undoubtedly your brand’s identity. Since it’s so critical for your business, you would want only the right people to send emails from it, so that your customers or prospects don’t get duped with fake emails pretending to be from you.
This is where SPF steps in and works like a guest list stored in your domain’s DNS. It’s the list in which you explicitly specify which IP addresses are allowed to send emails on behalf of your domain.
So when someone sends an email claiming to be from yourcompany.com, the receiving email server checks your SPF record to see if the sending server’s IP is on the approved list.

SPF’s limitations
SPF handles the guest list system well, but it’s not enough on its own. The issue is that when an email is sent directly from your server, SPF works well. However, it breaks on forwarding.
So, let’s say your customer forwarded your email to their colleague. Now, in this situation, the forwarded email is not sent from one of the servers mentioned in the SPF record (the guest list) because it came from the forwarding service’s server. Therefore, when the receiving server performs the SPF authentication checks, the email will not be considered authorized or legitimate.
Since SPF only looks at the IP address of the immediate sender, it doesn’t understand that the email was originally sent by your company and later forwarded. As a result, legitimate emails can end up in spam or get rejected, even though you did everything right.

That’s why SPF is a helpful but incomplete solution. To properly defend your domain against spoofing, SPF needs a powerful partner, that is, DMARC.
The basics of DMARC
So far, we’ve seen that SPF helps by telling the world which servers are allowed to send emails from your domain. But we also saw that SPF can get confused when emails are forwarded, and sometimes fake emails can still slip through.
This is where DMARC comes to fill the gap.
You can imagine DMARC as the smart supervisor that sits on top of SPF (and DKIM) to make clear decisions based on specific rules.
What’s interesting is the fact that DMARC doesn’t just say ‘pass’ or ‘fail.’ It instead tells the receiving server what to do with the emails that fail SPF and/or DKIM checks. Should the emails be delivered as usual, sent to the spam folder, or rejected entirely?
Plus, DMARC gives you regular reports. These reports show you who is sending emails using your domain and how many are passing or failing the checks. This helps you spot fake senders trying to spoof your brand and fix problems before they get out of hand.
How does DMARC use SPF (and DKIM) results?
Now let’s break down how DMARC actually makes decisions.
When an email arrives, DMARC looks at two things:
- The result of the SPF check.
- The result of the DKIM check (which is like a digital signature proving the email hasn’t been tampered with).

But an important twist is that DMARC checks for alignment. This means it doesn’t care only if the SPF check passed; it checks whether the domain in the ‘From’ address (the one people see) matches the domain authorized by SPF or DKIM.
For example:
Your company’s domain is yourcompany.com, and an email claims to be from yourcompany.com in the ‘From’ field. For DMARC to pass, either:
- The SPF check must pass, and the domain in the SPF record must exactly match yourcompany.com (this is called SPF alignment)
or
- The DKIM signature must be valid and also aligned with your domain.
If neither is aligned, DMARC marks the email as suspicious and tells the receiving server what to do (based on your DMARC policy).
So instead of just hoping SPF or DKIM works, DMARC makes sure the right domain is involved at every step.
Common pitfalls to avoid
When setting up SPF and DMARC, many people make simple mistakes that can cause big problems. Let’s look at the most common ones so you can avoid them.
1. Ignoring SPF alignment issues
Just having SPF pass is not enough. The domain in the ‘From’ field of your email must match the domain in your SPF record. If they don’t match, DMARC will fail the check. Always double-check that your SPF is aligned with your ‘From’ domain so legitimate emails don’t get blocked.

2. Setting DMARC to ‘p=reject’ too early
Many domain owners rush to set their DMARC policy to ‘reject’ too soon. This can block genuine emails if your setup is not yet perfect. Start with DMARC in ‘monitor’ mode. Check the reports regularly to understand what is passing and what is failing. Once you are confident, move to ‘reject’ for better protection.
3. Exceeding the DNS lookup limit
Your SPF record should not require more than 10 DNS lookups. It simply means that every time a receiving server checks your SPF record, it may need to look up multiple parts of your DNS to confirm which IPs are allowed to send emails. If there are too many lookups, the check fails automatically.

To avoid this, keep your SPF record simple. Use IP addresses directly when possible, and avoid too many include statements from third parties.
If it’s getting challenging to stay within the lookup limit, use our automatic SPF flattening tool or reach out to us. We will sort it out for you.