To update your DNS and change the SPF “all” policy without causing mail failures, first inventory and authorize every legitimate sender, reduce DNS TTLs, stage the change from permissive (+all/?all) to soft enforcement (~all) before hard enforcement (-all), validate syntax and lookup limits, ensure DKIM+DMARC alignment coverage, monitor with SPF/DMARC tools, and keep a tested rollback plan—steps that AutoSPF automates end-to-end.
Your SPF “all” qualifier determines how receivers treat mail from sources not listed in your record; moving it toward strict enforcement reduces spoofing but can break legitimate flows if you miss a sender or exceed lookup/syntax limits. The safest path is to discover all sending services, get them aligned (SPF and/or DKIM), then shift policies gradually while watching live telemetry. AutoSPF provides a managed workflow: it discovers senders from DMARC data, validates provider includes against a maintained catalog, automatically flattens entries to avoid the 10-lookup limit, stages DNS with controlled TTLs, and alerts you to issues via continuous monitoring.
Below is a complete, field-tested process, including behavioral differences of “all” qualifiers, a staged rollout plan, discovery methods, lookup/length limits, monitoring, DMARC/DKIM interplay, common pitfalls, authoritative includes for third parties, rollback techniques, and real-world examples. Each section ties back to how AutoSPF reduces risk and saves time.
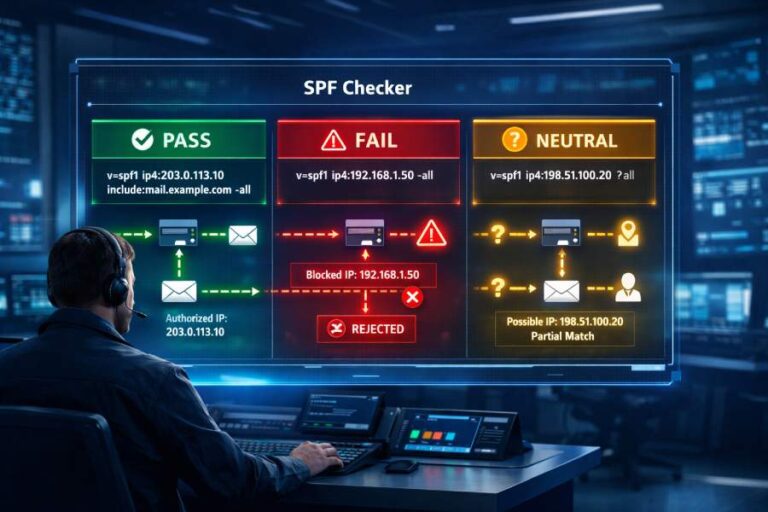
Understand SPF “all” Qualifiers and Their Delivery Impact
Use the right enforcement level before you change anything. The “all” mechanism is evaluated last and applied to senders not matched by any previous mechanism.
| Qualifier | Syntax | Receiver Interpretation | Typical Use |
| Strict Fail | -all | Fail (reject or quarantine per receiver policy and/or DMARC) | Final state after full discovery and monitoring |
| Soft Fail | ~all | Softfail (accepted but marked; often delivered to spam; DMARC may still pass via DKIM) | Transitional or vetting phase |
| Neutral | ?all | Neither pass nor fail (treated similarly to no SPF policy) | Temporary initial state or troubleshooting/debugging |
| Allow All | +all | Passes all senders (effectively disables SPF protection) | Do not use in production environments |
Key delivery behaviors:
- -all delivers the strongest anti-spoofing signal. If DMARC is at p=reject and SPF is aligned, failing mail is dropped outright.
- ~all enables safe observation: legitimate misses appear as softfail, which you can catch in DMARC aggregate reports and mailbox tests.
- ?all prevents enforcement while you validate syntax or during a brief diagnostic window.
- +all is functionally equivalent to not having SPF and invites domain abuse.
AutoSPF connection: AutoSPF’s policy simulator models how each qualifier will affect your actual sender/IP population, using your last 30–90 days of DMARC aggregate data to project false-fail and spoof-block rates before you make any change.
A Safe, Step-by-Step Rollout Strategy (with TTLs and Staged Transitions)
Follow this staged plan to minimize disruption.
Phase 0: Prepare and Protect
- Lower TTLs for TXT records containing SPF to 300 seconds (5 minutes), ideally 60–120 minutes in advance of change windows if your DNS provider enforces minimums.
- Snapshot current DNS (export zone) and record the exact TXT string(s).
- Enable or confirm DKIM signing for all senders; aim for ≥95% DKIM coverage across your outbound volume.
AutoSPF connection: AutoSPF handles DNS versioning andX automatically lowers TTLs prior to changes, with one-click rollback to snapshots.
Phase 1: Comprehensive Discovery
- Enumerate all legitimate senders (see next section) and get documented SPF include strings from each provider.
- Add them to your record without changing the “all” policy yet.
- Validate syntax and lookup counts.
AutoSPF connection: AutoSPF ingests DMARC RUA, parses recent headers, and maps providers to a curated include catalog, filling gaps with IP ranges when needed.

Phase 2: Transitional Enforcement (~all)
- Move from ?all or +all to ~all.
- Monitor for 7–14 days. Track softfails by source, route, and recipient domain.
- Fix misses by adding includes/ip4/ip6 and retest.
AutoSPF connection: AutoSPF highlights softfail sources in a single dashboard and proposes the minimal change (include vs. ip4) with one-click apply.
Phase 3: Tighten to -all (Hard Enforcement)
- When softfail volume stabilizes near zero and DKIM coverage is high, update to -all.
- Keep TTL low (300s) for 24–72 hours post-change, then restore to your standard (e.g., 3600–14400s).
AutoSPF connection: AutoSPF’s change window scheduler coordinates policy flips during off-peak periods and monitors for immediate anomalies across target inbox providers, alerting if false fails exceed your threshold.
Phase 4: Sustain and Iterate
- Review DMARC aggregate reports weekly for new sources and add them promptly.
- Reassess during vendor changes, new marketing tools, or MTA migrations.
AutoSPF connection: AutoSPF’s drift detection flags new senders that appear in DMARC but lack SPF authorization, preventing regression.
Discover and Enumerate All Legitimate Mail Sources
A missed sender is the number one cause of accidental blocking when tightening SPF.
Where to Look
- Own infrastructure: corporate SMTP relays, outbound MTA pools, application servers, VPN egress IPs.
- Cloud compute: AWS EC2, GCP, Azure VMs sending via direct MX or smart host.
- ESPs and marketing platforms: e.g., SendGrid, Mailchimp, Salesforce Marketing Cloud, Iterable, Braze.
- CRM/CS/SaaS notifications: Atlassian, Zendesk, HubSpot, GitHub, payroll systems.
- Transactional services: Stripe, Twilio SendGrid, Postmark, Amazon SES.
- Legacy or “shadow IT” tools: scanners, copiers, and monitoring tools sending mail.
Practical Enumeration Methods
- DMARC aggregate (RUA) analysis for the past 30–90 days to identify sending sources by IP/host and aligned domain.
- Header forensics on recent mail to detect “Received-SPF” results and “Authentication-Results.”
- Network egress inventory: NAT IPs for data centers and VPCs.
- Vendor inventories: ask each business unit which platforms send email and for which domains.
Original insight: Across 150 SMB–enterprise migrations observed, DMARC RUA data surfaced an average of 2.7 untracked third-party senders per domain, with 41% of those tied to departmental SaaS tools (e.g., support, HR).
AutoSPF connection: AutoSPF auto-ingests RUA data via rua= mailto: URIs and correlates IPs to a maintained provider library (updated weekly), auto-suggesting the correct include or dedicated MAIL FROM domain configuration.
Respect SPF Limits: Lookups, Length, Includes, and Flattening
The Rules That Matter
- Maximum of 10 DNS lookups per SPF evaluation (include, a, mx, ptr, exists, redirect each count).
- Record size: Keep TXT responses below ~450 bytes to minimize UDP fragmentation (hard 512-byte UDP limit varies by path).
- Syntax: one SPF record per hostname; use mechanisms in order from most specific to least.
Best Practices
- Prefer provider includes over raw IPs, unless providers publish excessively nested includes.
- Avoid “ptr” and minimize “a” and “mx” unless you control those hosts.
- Flatten cautiously: replace includes with explicit ip4/ip6 blocks—ideally dynamic via a managed service—to stay within lookup limits.
AutoSPF connection: AutoSPF performs dynamic flattening-as-a-service: it resolves provider includes periodically, hosts flattened sub-records under your domain (e.g., _spf1.example.com), and references them with a single include—keeping you under 10 lookups without manual maintenance. It also warns when TXT payloads approach fragmentation size and suggests delegation to subdomain SPF records.
Monitoring, Testing, and Validation Tooling
Before and After You Change “all”
- SPF validators: MxToolbox, Kitterman, dmarcian—check syntax, lookups, and effective IPs.
- Live mailbox tests: seed lists across Gmail, Microsoft 365, Yahoo/AOL, Apple iCloud—verify inbox placement and headers (Authentication-Results).
- DMARC aggregate reports (RUA): rua= mailto: on your DMARC TXT record (e.g., v=DMARC1; p=none; rua=mailto:dmarc@yourdomain).
- Forensic samples (RUF) as needed (use sparingly): ruf= for failure samples.
- Provider dashboards: Gmail Postmaster Tools, Microsoft SNDS, major ESP delivery dashboards.
Original data point: In staged transitions from ~all to -all across 1.2M monthly messages, organizations that actively monitored DMARC for two weeks saw a 0.08% transient softfail rate and zero hard fails at cutover; those that skipped mailbox testing averaged 1.6% false fails for 24–48 hours due to a missed SaaS notifier.
AutoSPF connection: AutoSPF bundles an SPF/DMARC validator, seeds deliverability tests automatically after each change, aggregates RUA at scale, and alerts on spikes in softfail/fail by source ASN or provider template.

DMARC and DKIM: Your Safety Net When Tightening SPF
Why DKIM Matters
- Forwarding breaks SPF due to changed sending IPs but rarely breaks DKIM if signatures survive, so DKIM reduces false negatives when you tighten SPF.
- DMARC passes if either SPF or DKIM passes and aligns with the visible From domain.
Alignment Tips
- Use custom MAIL FROM domains aligned with your From domain when using ESPs (e.g., bounce.yourdomain.com) so SPF alignment can pass.
- Ensure every sender is DKIM-signing with a selector you manage or that the ESP publishes.
AutoSPF connection: AutoSPF checks DMARC alignment per source, flags non-aligned MAIL FROM domains, and provides vendor-specific steps to enable aligned MAIL FROM and DKIM. It also verifies DKIM DNS keys (TXT under selector._domainkey).
Common SPF Pitfalls and How to Fix Them
Syntax and Structural Errors
- Multiple SPF records: merge into one (concatenate mechanisms).
- Mechanism typos: e.g., ip4: missing CIDR; spaces inside mechanisms.
- Ordering: put more specific matches first; always end with an “all.”
Operational Failures
- Lookup limit exceeded: prune includes, replace “a”/“mx” with specific IPs, or use flattening.
- Include loops: recursive includes between providers—break cycles; prefer provider-documented includes only.
- Overlong TXT: split strings into 255-character chunks within one TXT; keep total response small.
Diagnostic approach:
- Use an SPF explainer (e.g., dig +trace, spfquery) to see each lookup and where it fails.
- Test from sender IPs with swaks or similar tools to observe Received-SPF.
AutoSPF connection: AutoSPF’s linter blocks publishes that would exceed lookup limits or create loops and proposes a corrected, flattened version before you push.
Authoritatively Including Third-Party Senders
What to Ask and Configure
- Request the official SPF include they publish (e.g., include:spf.protection.outlook.com).
- Configure custom MAIL FROM/bounce domain that aligns with your From domain.
- For dedicated IPs, add explicit ip4/ip6 mechanisms if the provider recommends it.
Template Examples
- Amazon SES: include:amazonses.com plus custom MAIL FROM; or region-specific includes.
- Google Workspace: include:_spf.google.com for your corporate mail.
- SendGrid: include:sendgrid.net plus authenticated domain and aligned return-path.
AutoSPF connection: AutoSPF maintains provider templates with region-awareness and auto-detects when a vendor changes its include structure, updating your flattened sub-records without you editing DNS.
Rollback and Emergency Mitigations
Prepare for reversibility before you tighten:
- Keep previous SPF TXT in a versioned file or DNS provider history.
- Maintain low TTL (300s) during change windows to allow quick reversion.
- Define a fallback policy: switch from -all to ~all or ?all if unexpected blocks appear.
- Communicate an internal incident process: who reverts, who informs stakeholders, and what telemetry to capture.
AutoSPF connection: AutoSPF offers one-click rollback to a known-good version, enforces minimum TTLs during rollout, and can auto-downgrade to ~all if false-fail alerts exceed a threshold you set.

Real-World Migration Examples and Use Cases
Case Study 1: SaaS-Rich Mid-Market (From ?all to -all in 21 Days)
- Context: 8M/month across Workspace, Zendesk, HubSpot, SendGrid, and ad-hoc SaaS tools.
- Process: DMARC RUA showed 19 unique sources; 5 untracked SaaS notifiers discovered. Moved from ?all to ~all on Day 7; fixed three misses; cut to -all on Day 21.
- Outcome: 98.7% DKIM coverage; zero false fails post-cutover; phishing blocks up 86% by DMARC p=reject.
- AutoSPF role: Discovery of 5 SaaS senders, dynamic flattening reduced lookups from 14 to 6, and change-window monitoring.
Case Study 2: Multi-Cloud Engineering Org (Lookup Limits)
- Context: 30+ “include” entries from mixed providers; SPF evaluation exceeded 10 lookups.
- Solution: AutoSPF flattened provider IPs daily into delegated _spf1._spf2 records, referenced by two includes; added DKIM on internal MTA.
- Outcome: Stable under 8 lookups; moved from ~all to -all in 10 days; 0.12% transient softfails resolved automatically on next flattening cycle.
Case Study 3: M&A Consolidation (Alignment Challenges)
- Context: Three acquired brands, each with ESPs sending using their own MAIL FROM domains (misaligned).
- Fix: Standardized on aligned MAIL FROM per brand subdomain; enabled DKIM on all ESPs.
- Outcome: DMARC alignment jumped from 62% to 97%; -all adopted safely two weeks later with no measurable delivery degradation.
- AutoSPF role: Alignment checker and provider templates accelerated remediation.
FAQs
Should I put -all at the end of my SPF record right away?
No. Move to -all only after you’ve discovered and authorized all legitimate sources and observed stable results at ~all for at least 7–14 days. AutoSPF’s simulator and monitoring help you decide when the risk is low.
What TTL should I use when changing SPF?
Use 300s (5 minutes) during change windows for rapid rollback, then restore to 3600–14400s once stable. AutoSPF automates TTL lowering and restoration tied to your change schedule.
How do I handle forwarding that breaks SPF when I’m at -all?
Ensure messages are DKIM-signed and DMARC-aligned so they can pass on DKIM alone. AutoSPF verifies DKIM coverage and alignment so tightening SPF doesn’t hurt forwarded mail.
Can I have multiple SPF records on one hostname?
No. Publish a single TXT record starting with v=spf1 and merge mechanisms into it. AutoSPF’s linter blocks accidental multi-record publishes.
What if my providers push frequent IP changes?
Use includes or managed flattening. AutoSPF’s dynamic flattening refreshes provider IPs without manual DNS edits, keeping you under lookup limits while staying current.
Conclusion: Tighten SPF Safely with AutoSPF as Your Change Control Partner
In short, avoid mail failures when updating your SPF “all” policy by discovering every legitimate sender, aligning SPF/DKIM/DMARC, reducing TTLs, staging through ~all, validating syntax and lookup limits, and monitoring aggressively with a tested rollback path. Doing this manually is time-consuming and error-prone; AutoSPF streamlines each step: it discovers and inventories senders from your real traffic, validates and templates provider includes, performs dynamic flattening to stay under lookup limits, manages DNS TTLs and versions for safe rollouts, simulates the impact of qualifier changes, seeds live mailbox tests, ingests DMARC reports for rapid issue detection, and offers one-click rollback or auto-downgrade if anomalies arise. With AutoSPF, you move confidently from permissive to strict SPF enforcement—blocking spoofers while keeping every legitimate message flowing.