SPF (Sender Policy Framework), one of the three email authentication protocols, enables recipient email servers to verify whether or not the email received is an authorized one. However, SPF comes with its own set of intricacies, as there is a limit of 10 DNS lookups. Once the SPF record has reached the maximum limit of 10, even the legitimate emails can fail the authentication check, and you will get to see a “PermError”. A malicious email, too, can go undetected and lead to false negatives.
This blog aims to explore why SPF lookup limit exists, how cyberattackers can misuse it, the degree of risks involved, and the best practices organizations must stick to in order to tackle this issue effectively.
Why does the SPF lookup limit exist?
When a recipient email server retrieves your SPF record for email authentication, it follows mechanisms that involve DNS lookups such as a, mx, include, exists, etc. The maximum limit of unique DNS lookups per SPF record is 10.
Here’s why there’s a constraint on SPF DNS lookups:
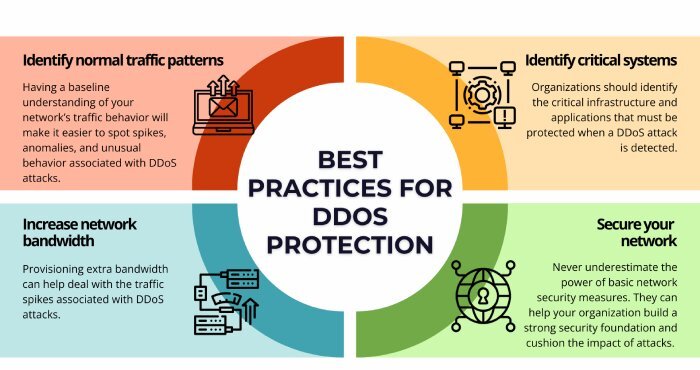
Preventing DDoS attacks
Too many SPF lookups enable cybercriminals to abuse vulnerable DNS servers. They do so by creating spoofed SPF lookup requests and misusing the recipient’s IP address as the main source. Next, the DNS server sends bulk responses to the IP address of the victim, thereby directing massive traffic to the victim and eventually leading to a risk of a DDoS attack.
Network latency
Too many DNS lookups can lead to network latency, thereby delaying email delivery. Such delays can hamper user experience and create issues in communications that are time-sensitive. Also, network latency is considered an indicator of misconfigured or malicious servers by spam filters. So it can also lead to your legitimate emails being marked as spam or getting rejected right away.

DNS query overload
Excessive DNS lookups can lead to DNS server overload, which can further create technical issues, leading to false negatives or positives.
Unnecessary complications
Unlimited SPF lookups would mean intricate and highly dynamic email processing algorithms. Also, if the limit was higher than 10, it would have invited bugs and vulnerabilities, making the email communications susceptible to threat attacks.
Excessive consumption of resource
DNS servers come with limited resources (memory, bandwidth, and processing power). It is, therefore, not feasible to have unlimited DNS lookups.

SPF lookup limit exploits and abuse potential
1. DNS amplification/DoS via SPF
Threat actors can create SPF records with recursive or excessive includes in order to start a massive series of DNS queries. This trick can overwhelm the DNS servers, leading to downtime or service degradation.
2. SPF record bombing
This is quite similar to email bombing and involves the manipulation of SPF records or injecting bloated SPF records in order to come up with recursive or excessive DNS lookups. Such an attack leads to the victim domain’s SPF validation failure, thereby hampering email deliverability. At the same time, it also overwhelms the DNS infrastructure.
3. Risk to deliverability
When you reach the 10 lookup limits, it will show a “permerror” or Permanent Error. This affects your email deliverability, leading to your legitimate emails getting rejected. Spam filters, too, may get confused and move an authorised email into the spam box. This can affect your brand goodwill and user experience.
How to know if your SPF record has exceeded the DNS lookup limit?
In order to make sure that your SPF configuration is within the safe range of DNS lookups, you can use certain tactics. These are:
Tools and methods
There are extensive tools for SPF record testing, such as the DMARC analyzer, MXToolbox, and Kitterman SPF validator. With these tools, you get an elaborate breakdown of all mechanisms, potential issues, and DNS lookups.
Logs from email services or providers like Microsoft 365 or Google Workspace help you analyze your SPF record manually and count mechanisms. In case it adds up to more than 10, consider yourself in trouble!

Signs of SPF failure because of lookup limits
You will get to see SPF failure signs, such as false positives or negatives. There will be a delay in email deliverability, too. Such signs will make you realize that something is not right with the DNS lookup limits.
Mitigations and optimization techniques
In order to maintain the 10 DNS lookup threshold and ensure smooth email deliverability, consider the following techniques:
Flattening SPF records
This tactic easily replaces domain-based includes with resolved IP addresses, thereby reducing DNS lookups to 0.

Use of subnet IPs instead of domains
It is better to use a known static IP range over a domain include. This significantly reduces lookup counts.
Avoiding overuse of ‘include:’ statements
Each ‘include:’ adds up to one DNS lookup and can even lead to nested lookups. It is, therefore, advisable to include only necessary services that actually send email communications on behalf of your domain.
Minimize/remove unused mechanisms
Carry out regular audits and clean up the unused ‘mx’ or ‘a’ mechanisms, ‘include’ statements of vendors that are not in use any longer, and unnecessary wildcard entries. Remember that less is more when it comes to SPF records.

Leverage the ‘redirect’ mechanism wisely
With ‘’redirect,’ it is possible to delegate SPF checks to a completely different domain. This technique comes in handy for organizations that manage multiple domains. It helps in avoiding duplicate SPF logic across multiple domains.
Best practices to stay within the SPF limits
Regularly audit SPF records
A monthly or quarterly review of your SPF record can be a great way to stay within SPF limits. Focus on validating lookups, and don’t forget to keep a check on redundancies. Keep cleaning on the go.
Keep a central SPF management policy for your organization
Create a centralized system or spreadsheet in order to maintain details of services that are authorised to send out emails, their SPF requirements, etc. This helps the entire team to operate in close coordination.

Limit third-party senders and vet their SPF practices
Know that not all third-party senders are SPF-friendly. Before integrating an email service provider, double-check its SPF footprint. Also, check whether they offer a flattened SPF record or IP ranges. Always go for vendors who have minimal SPF impact.
Combine SPF with DKIM and DMARC for layered security
SPF alone is not adequate to safeguard your email communications. Combine it with DKIM (DomainKeys Identified Mail) and DMARC (Domain-based Message Authentication Reporting and Conformance) for an all-encompassing and robust email security system.





