
As per the textbook definition of an SPF record, it is essentially a list of servers authorized to send emails on your behalf. This understanding of an SPF is correct but incomplete. This is only one part of it.
While it is essentially a list of authorized servers that send emails on your behalf, it is also a sequence of instructions that guide receiving servers as to how to evaluate those senders.
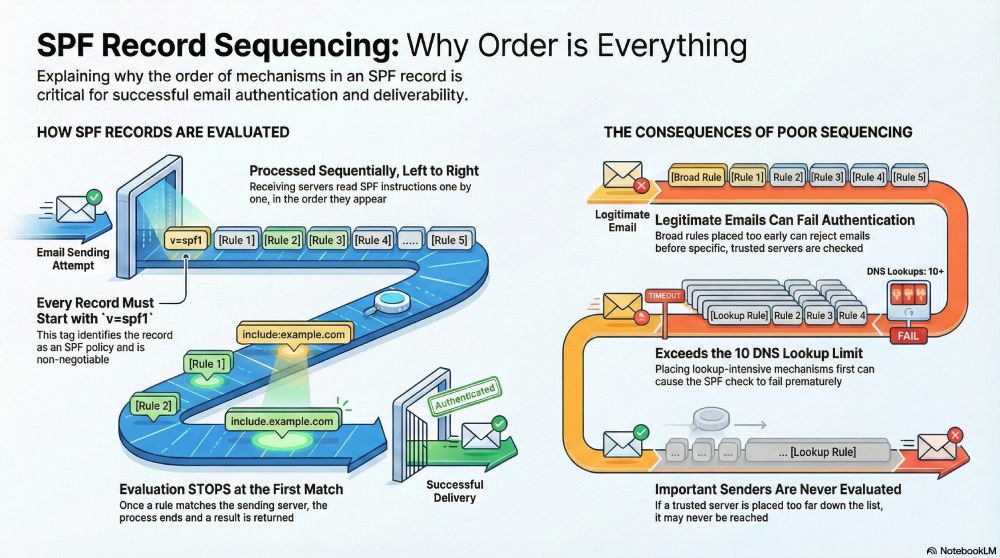
When evaluating these senders, it is not done arbitrarily but rather according to a defined order. The receiving mail server reads the SPF record from left to right, testing each instruction one at a time. The moment a rule matches the sending server, the evaluation stops, and an SPF result is returned. Any instructions that follow are not evaluated.
This is why the structure of the SPF record matters as much as its content. If you want your legitimate email servers to pass authentication tests, you cannot arbitrarily place any mechanism.
In this article, we will understand how the sequence of the SPF mechanism impacts deliverability and DNS lookup limits.

Understanding the order of SPF record mechanisms
As we established earlier, the SPF record is evaluated based on the sequence of mechanisms you follow while configuring it. This mechanism sequence cannot be random, since each mechanism is processed in order, and evaluation stops as soon as a match is found.
Because of this, the placement of the mechanisms within the record has to follow certain rules, or else your emails might not even reach their recipients.
Here are some mechanism sequencing rules that you should follow while setting up the SPF record:
- Every SPF record must begin with the v=spf1 tag. It is non-negotiable that the first element in your SPF record is v=spf1. This tag identifies the TXT record as an SPF policy and instructs the receiving server to interpret its contents according to the SPF specification. If you skip adding this tag or don’t start your SPF record with this tag, your SPF authentication will be rendered ineffective.
- Once the v=spf1 tag is defined, all the other SPF mechanisms are evaluated sequentially from left to right. These mechanisms test whether the sending server meets a specific condition and stop evaluation as soon as a match is found.
- The fact that the evaluation stops as soon as the first applicable mechanism makes the ordering all the more critical. That means, mechanisms that are placed earlier in the record have a greater influence on the final SPF result than those that follow. So, if you place a very broad or very restrictive mechanism too early, it can come to a conclusion even before more specific mechanisms are evaluated. This can lead to legitimate emails failing or even unauthenticated emails getting past these checks.
- For mechanisms like ip4, ip6, a, mx, and include, they must be positioned before the ‘all’ mechanism. Although you have the flexibility to tweak the internal order of these mechanisms, remember that some of these mechanisms require DNS lookups. So, if too many lookups are triggered, the SPF check can fail before all mechanisms are evaluated.

Why sequencing matters in an SPF record?
There is no fixed right or wrong when it comes to SPF mechanism sequencing, apart from a few non-negotiable requirements. However, this does not mean that sequencing is optional or even inconsequential.
Let’s understand why the order of the SPF mechanisms matters more than you realise.
Evaluation stops once a match is found
The receiving server evaluates your SPF record in a specific order. Moving from left to right, it processes each mechanism as it appears and stops the evaluation as soon as an applicable mechanism is reached. At this point, the evaluation process is stopped, and no further mechanisms are considered. For instance, if you place the ‘all’ mechanism early in the SPF record, the evaluation will stop as soon as it is reached.
Earlier mechanisms take priority over the later ones
Since these mechanisms are assessed sequentially, the ones placed earlier in the record have a greater impact on the final authentication result. If an early mechanism applies, the SPF check ends there, and later mechanisms are not reviewed. This is why important and regularly used sending servers should be listed first. If you place a legitimate sender too far down the record, it may never be evaluated.
Broad or restrictive rules can override specific ones
As your email ecosystem becomes more complex, your SPF record grows to include multiple sending services. In such cases, when you place a highly restrictive mechanism too early in the record, the evaluation may stop before legitimate sending servers are checked. This way, even your legitimate emails might fail authentication. To prevent this, make sure that your default mechanisms are placed only after all trusted and specific sending sources have been evaluated.
Poor sequencing can lead to DNS lookup limit failures
As you know, there are only 10 DNS lookups allowed during SPF evaluation. Mechanisms such as include, a, and mx consume these lookups as the receiving server processes the record. So, if you place all the lookup-intensive mechanisms early in the SPF record, the evaluation may exceed the lookup limit before reaching the important sending servers listed later. When this limit is exceeded, SPF fails, even if all legitimate senders are correctly included.

SPF works alongside DKIM and DMARC to strengthen email security, but managing SPF mechanisms and DNS lookup limits is essential to ensure proper authentication and reliable email delivery.
To sum up
It is important that you properly configure your SPF record because if any mechanism is skipped or misplaced, even the legitimate sending servers might be skipped during authentication. Moreover, poor sequencing can also cause SPF checks to exceed DNS lookup limits, resulting in authentication errors even when the record looks correct.
If you are not sure how to go about the SPF mechanism sequencing, our team is here to help! To know more, get in touch with us!






