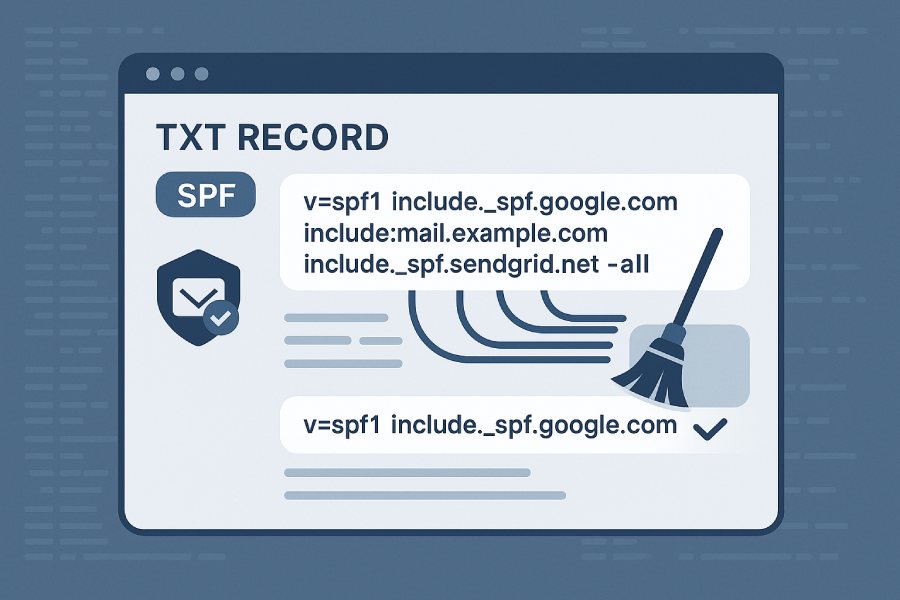
The Sender Policy Framework (SPF) is a vital component of email security and email authentication, designed to prevent email spoofing and protect domains from unauthorized use. At its core, an SPF record is a type of DNS TXT record that specifies which email servers are authorized to send email on behalf of a domain. When an email arrives at the recipient’s email server, the server performs an SPF check by querying the domain’s DNS for the SPF record, ensuring the sender is permitted as per the SPF policy.
An SPF record follows a defined SPF record syntax, beginning typically with the SPF version (e.g., `v=spf1`), followed by various SPF mechanisms and modifiers that collectively define the sending policy. These mechanisms include IP addresses, CIDR ranges, and importantly, the include mechanism, which allows for delegation of SPF validation to other domains—vital when multiple third-party services send emails on a domain’s behalf.
Organizations such as Microsoft, Google, and Amazon Web Services (AWS) offer comprehensive guidelines and best practices for SPF record setup to maintain smooth email deliverability and enforce strict domain authentication. Leading platforms and tools like MxToolbox, DMARC Analyzer, and spf-record.com facilitate SPF validation by parsing records and alerting administrators to possible SPF syntax errors or exceeding the DNS lookup limit.
The Role of TXT Records in SPF Implementation
SPF records are primarily published as DNS TXT records, making the DNS system central to SPF’s functioning. When an email server or intermediate mail exchanger (MX) receives an inbound email, it performs a DNS query on the recipient domain for the SPF record stored in TXT format. This process uses the domain’s DNS resolver, which caches results subject to the DNS TTL (Time-To-Live) setting, thereby influencing DNS propagation speed during SPF record updates.
Despite the existence of dedicated SPF DNS records, the widespread adoption of DNS TXT for SPF provides flexibility and backward compatibility. However, administrators must exercise rigorous DNS management and DNS administration in the DNS zone file to avoid overlapping TXT entries and ensure accurate SPF record syntax and semantics.
Several domain registrars and DNS hosting providers like GoDaddy, Namecheap, Cloudflare, Gandi, and TUCOWS facilitate intuitive interfaces for SPF record deployment, empowering security-conscious organizations to mitigate risks related to email fraud prevention through effective SPF DNS record configuration.
Importance of SPF for Email Authentication
SPF is a foundational technology in the suite of email authentication protocols that also includes DKIM and DMARC. SPF functions by enabling receiving servers to verify whether an email claimed to come from a domain is transmitted from a valid source authorized in that domain’s SPF record.

By validating the sender’s IP against the SPF record, domains reduce the likelihood of SPF fail—a rejection scenario that signifies unauthorized senders. Conversely, a SPF pass outcome confirms the email’s authenticity per the SPF policy, thereby enhancing trust in the email headers and improving email deliverability.
SPF also supports multiple evaluation outcomes such as SPF neutral, SPF softfail, and SPF hard fail, which provide nuanced responses tailored to how strictly a domain wishes to filter potential spam or phishing attempts. Email security providers like Proofpoint, Valimail, Return Path, Barracuda Networks, and Symantec integrate SPF validation into their secure email gateways, strengthening enterprise-wide protections.
Effective SPF implementation not only reduces email spoofing but also aids in SPF email filtering—a crucial part of email security strategies that preserve domain reputation and user confidence in corporate communications.
What Does “Include” Mean in SPF Records?
The SPF include mechanism is an SPF syntax element that simplifies complex policies involving multiple sending sources. The `include:` directive instructs the SPF resolver to fetch and evaluate the SPF record of another domain and incorporate its authorization within the current domain’s SPF policy.
For instance, many organizations rely on third-party email service providers like SendGrid, Mailgun, SparkPost, Postmark, or cloud services from Microsoft 365 and Google Workspace. Instead of hard-coding each service’s IP addresses in their own record, they use multiple include statements referencing the SPF records of those services, which maintain their own SPF DNS records.
This delegation is critical for domains that utilize multiple vendors, as manually listing all IPs can lead to bloated records exceeding the DNS lookup limit (10-lookups maximum). Proper use of qualified include mechanisms (using prefixes like `+include:` implicitly) avoids SPF syntax errors and prevents erroneous SPF indirect includes that can cause lookup inefficiencies and SPF validation failures.
How Multiple Include Mechanisms Work in SPF
When a domain uses multiple include mechanisms within its SPF record, each `include:` triggers additional DNS TXT lookups on referenced domains’ SPF records. The DNS resolver follows these references recursively, compiling a composite list of authorized IPs and domain names.
However, SPF’s design enforces a critical constraint: the combined number of SPF DNS lookups during evaluation cannot exceed 10. Crossing this DNS lookup limit causes the SPF validation to result in an automatic SPF fail or a permerror, leading to potential email rejection or marked as spam by receiving servers.
To manage this, domain administrators employ strategies like SPF record flattening, which involves pre-resolving included domains’ IPs and embedding them directly, reducing reliance on multiple indirect includes. Tools from companies like OpenSPF, along with expert utilities like MxToolbox and DMARC Analyzer, aid in identifying excessive lookups and offer remediation advice.

Furthermore, enterprises using advanced solutions from IBM, Cisco, Oracle, or F5 Networks may implement dynamic SPF validation logic. Through DNS SPF management best practices, they optimize their SPF policies to maintain SPF alignment with DMARC requirements and ensure robust email fraud prevention.
SPF multiple include usage demands meticulous DNS administration to track all referenced domains’ SPF records and their changes, especially considering DNS propagation delay after record updates. This agility is essential in a landscape where third-party services, such as Fastmail, Zoho Mail, or enterprise providers like Adobe, often revise IP ranges, necessitating prompt SPF record changes to prevent failed SPF evaluations.
In summary, the multiple include mechanism in SPF records expertly balances the need for complex authorization scenarios with the inherent limitations of DNS lookups. A well-constructed SPF record employing multiple includes correctly enhances email security, safeguards against spoofing, and improves deliverability outcomes across diverse and distributed email ecosystems.
Common Use Cases for Multiple Include Statements
In the realm of email authentication, implementing multiple include statements within an SPF record is a practical approach to accommodate diverse email sending sources. Domains that leverage a combination of internal mail servers, third-party services such as SendGrid, Mailgun, or SparkPost, marketing platforms like Adobe Campaign, and cloud providers including Amazon Web Services or Microsoft Azure often utilize multiple includes to authorize all legitimate senders. The SPF include mechanism enables domain owners to reference SPF DNS records of external vendors, thereby incorporating their sending IP address ranges without manually enumerating them.
This modular approach is prevalent among enterprises that use Microsoft 365 alongside Google Workspace, and additional security layers from providers such as Proofpoint or Mimecast. Similarly, organizations employing third-party email security solutions from Barracuda Networks or Symantec integrate those senders via include statements to maintain alignment with SPF policies. Multiple include statements ensure that domain authentication is comprehensive, preventing improper SPF fail results which could negatively affect email deliverability and open doors to email spoofing attacks.
Challenges and Limitations of Multiple Includes
While multiple include statements offer flexibility, they also introduce complexity stemming from the SPF syntax and the DNS lookup limit. Each include directive triggers one or more DNS TXT queries, as DNS resolvers fetch the referenced SPF DNS records to evaluate the overall SPF policy. These queries accumulate rapidly, especially if included records nest other include mechanisms indirectly, a process termed SPF indirect include.
The primary limitation lies in the DNS lookup limit—specifically, the RFC 7208 specification caps the number of DNS lookups at 10 per SPF evaluation. Exceeding this threshold results in an SPF fail or SPF hard fail, causing receiving mail servers to reject or flag messages. Complex SPF policies with multiple vendors or loosely managed DNS zone files can inadvertently breach this limit, triggering SPF validation failures.
Additionally, improper SPF record setup can lead to syntax errors. Common mistakes include malformed include statements or unqualified includes, which disrupt SPF parsing. Unsupported or deprecated SPF versions or mixing mechanisms inconsistently may also hinder effective SPF email filtering, further impairing email deliverability.
The 10-DNS Lookup Limit and Its Impact
The 10-DNS lookup limit serves as a safeguard against SPF record abuse that might overload DNS infrastructure. However, it imposes a strict constraint on SPF record complexity. Each mechanism conditionally activating a DNS lookup—such as include, a, mx, ptr, and exists—contributes to this limit.
Domains utilizing multiple include statements across diverse vendors must carefully monitor cumulative DNS SPF lookups. For example, a domain authorizing Amazon Web Services EC2, Google mail servers, and a third-party service like Valimail or Return Path might rapidly exhaust this quota, especially if any include record internally references additional includes. Surpassing the lookup limit results in the SPF policy returning an SPF permerror or SPF fail status, increasing the risk of email rejection or misclassification.

The implications on email security and email deliverability are significant. A legitimate email marked as SPF fail due to lookup violations can be blocked outright or relegated to spam, undermining domain reputation and anti-phishing initiatives. Organizations need to balance comprehensive domain authentication with adherence to the lookup limit, applying strategic SPF record flattening methods or simplifying includes where feasible.
Best Practices for Structuring Multiple Include SPF Records
Efficient structuring of multiple include SPF records demands discipline in DNS management and DNS zone file organization. The following best practices are recommended to optimize SPF record setup while mitigating DNS query overhead:
- Prioritize and Consolidate Include Statements: Before adding multiple includes, assess whether providers support a unified SPF record or offer qualified include terms to reduce redundancy. Many vendors, such as Google, Microsoft, and Cisco, maintain optimized SPF DNS records designed for inclusion.
- Implement SPF Record Flattening: This technique involves replacing include mechanisms with a direct list of IP addresses, effectively pre-resolving DNS lookups before publishing the SPF record. Services like spf-record.com or MxToolbox provide tools to automate flattening, thereby reducing DNS queries at evaluation time.
- Monitor DNS TTL Values: DNS TTL (Time to Live) settings influence DNS propagation speed and cache effectiveness. Setting appropriate TTL values ensures DNS resolvers receive timely SPF records without excessive querying.
- Validate SPF Syntax Meticulously: Adhere strictly to SPF record syntax as defined by RFC 7208 and the OpenSPF standards, avoiding syntax errors that can cause SPF neutral or SPF softfail results. Use SPF expert tools, including the DMARC Analyzer and SPF record checker utilities, provided by providers like Valimail or Return Path.
- Leverage DNS Management Platforms: Modern DNS administration platforms such as Cloudflare, GoDaddy, or Namecheap provide interfaces for streamlined SPF record editing and real-time syntax validation, reducing administrative overhead.
- Regularly Audit SPF Records: Periodic reviews ensure that includes remain relevant and do not contain deprecated or unnecessary references, which can inflate DNS lookup counts.
- Prefer Mechanism Include Over Indirect Lookups: When possible, use direct SPF mechanisms rather than indirect or recursive includes to maintain transparency and control over the SPF policy.
Troubleshooting Common Issues with Multiple Includes
Diagnosing SPF-related problems typically involves analyzing email headers and evaluating the SPF policy as interpreted by receiving mail servers. Common issues with multiple includes include SPF hard fail due to exceeding the DNS lookup limit, SPF syntax errors, and incorrect domain authentication leading to SPF neutral or softfail results.
Administrators should begin troubleshooting by:
- Reviewing Email Headers: Inspect headers for SPF pass/fail results that indicate the SPF evaluation outcome. Fields such as “Received-SPF” offer insight into which component caused the failure.
- Using SPF Record Checker Tools: Utilities like MxToolbox’s SPF checker, spf-record.com, and OpenSPF validators provide detailed reports on the SPF record syntax, including mechanisms that trigger each DNS query.
- Monitoring DNS Queries: Employ DNS resolver logs or query the DNS TXT records directly to identify nested includes or additional lookups contributing to the DNS lookup count.
- Testing Simplified SPF Records: Temporarily replacing multiple includes with a minimal SPF policy can isolate whether complexity is the root cause of errors.
- Ensuring DNS Propagation: Confirm that recent SPF record changes have propagated fully by checking DNS TTL and querying DNS TXT records from multiple locations via DNS administration tools.
- Verifying SPF Policy Consistency: Cross-validate that the SPF policy aligns with DMARC and DKIM records, maintaining holistic email authentication and fraud prevention.
Tools and Resources for Validating SPF Records
A variety of specialized tools and services assist DNS administrators and email security professionals in authoring, validating, and maintaining SPF records, especially those with multiple include statements:
- MxToolbox: Offers comprehensive SPF record checks including DNS lookup simulation, syntax validation, and identifies potential overshoot of DNS lookup limits.
- spf-record.com: Provides visualization and flattening services facilitating optimization of SPF records with multiple includes.
- DMARC Analyzer: Integrates SPF validation within broader email authentication reporting and monitoring frameworks to improve domain-level protections.
- OpenSPF Validators: Community-driven tools that verify SPF syntax and compliance with RFC standards.
- Vendor-Specific Resources: Platforms like Microsoft’s Office 365 SPF documentation and Google’s Workspace email authentication guides provide templates and include strings for proper SPF record setup.
- DNS Management Services: Providers such as Cloudflare, GoDaddy, Namecheap, TUCOWS, and Gandi furnish DNS administration portals emphasizing SPF record editing with real-time validation.
- Commercial Email Security Solutions: Companies including Proofpoint, Valimail, Return Path, Barracuda Networks, and Mimecast offer SPF management as part of integrated email fraud prevention suites, simplifying deployment and monitoring.
By leveraging these tools, organizations can efficiently maintain SPF records that effectively utilize multiple include statements without violating the DNS lookup limits or introducing SPF syntax errors, thereby enhancing their email server’s domain authentication posture and sustaining high email deliverability rates.
Alternatives to Multiple Include Statements
In the realm of SPF record setup, managing multiple include statements within a single DNS TXT record can be challenging due to the inherent DNS lookup limit, typically capped at 10 DNS queries per SPF check. Exceeding this limit results in SPF fail responses, thereby negatively affecting email deliverability and domain authentication efforts. To mitigate this, administrators often explore alternatives to multiple include mechanisms.
One effective approach involves SPF record flattening, where third-party SPF expert tools such as those provided by spf-record.com or MxToolbox generate a single, consolidated SPF DNS record. Flattening replaces multiple nested includes and indirect includes with a comprehensive list of IP addresses and ranges, thereby reducing DNS SPF lookups and accelerating DNS query resolution via DNS resolvers.
Another alternative entails the use of qualified includes—strategically selecting and combining only essential SPF mechanisms include statements from trusted email providers like Microsoft, Google, Amazon Web Services, and Cloudflare. By consolidating the mail exchanger (MX) IP ranges and email servers into fewer include statements, DNS administration becomes more straightforward, and DNS zone file management is simplified.
Organizations increasingly utilize dedicated services such as Valimail, Return Path, or Proofpoint which automate SPF record optimization while ensuring compliance with SPF syntax standards. These platforms offer enhanced SPF record validation and policy alignment tools integrated with email authentication frameworks like DMARC Analyzer for better email fraud prevention.
How to Optimize SPF Records for Faster DNS Resolution
Optimizing SPF records to achieve faster DNS resolution without compromising email security is critical for maintaining high email deliverability rates. The SPF record syntax should be meticulously crafted to balance readability, adherence to SPF version guidelines, and DNS lookup efficiency.
Key optimization strategies start with minimizing the number of SPF mechanism include commands, as each mechanism include triggers a separate DNS SPF lookup. Using SPF record flattening effectively eliminates the overhead of indirect includes, helping stay under the DNS lookup limit threshold and thus avoiding SPF hard fail scenarios.
Setting appropriate DNS TTL (Time to Live) values on SPF DNS records aids in reducing DNS query frequency by allowing DNS resolvers to cache SPF TXT records longer, thereby speeding up SPF validation during SPF email filtering. DNS management platforms such as GoDaddy, Namecheap, Gandi, and TUCOWS provide intuitive interfaces for adjusting DNS zone file TTL values to optimize propagation time without compromising DNS propagation freshness.
Furthermore, utilizing multi-purpose SPF DNS records combining IP addresses, qualified includes, and direct IP specifications rather than overusing the include mechanism improves query response times. Maintaining correct SPF record syntax and validating configurations with SPF record checkers prevents SPF syntax errors which could cause SPF neutral or SPF softfail in email headers.

Another enhancement includes configuring SPF alignment properly alongside DMARC policies to reinforce domain authentication, ensuring the email server’s legitimacy is verifiable without unnecessary redundant DNS queries.
Security Considerations When Using Multiple Includes
While multiple include statements enhance flexibility in specifying authorized email sources, they introduce nuanced security considerations. The more includes embedded within an SPF record, the greater the risk of SPF record misconfigurations and inadvertent exposure to email spoofing vulnerabilities.
Improperly qualified includes may lead to SPF softfail or neutral results instead of definitive SPF pass or hard fail, weakening the SPF policy’s effectiveness in email fraud prevention. Attackers can exploit SPF syntax errors or indirect include loopholes to bypass SPF validation checks.
From an email security perspective, it’s crucial that each SPF include mechanism corresponds to trusted and verified DNS SPF records maintained by reputable providers like Mimecast, Barracuda Networks, and Symantec. Organizations should periodically audit their DNS TXT records and SPF DNS records using SPF expert tools and services provided by DMARC Analyzer or Valimail to detect and rectify potential vulnerabilities.
DNS administration should enforce strict SPF policy validation rules and monitor DNS TTL for timely SPF updates, especially when email infrastructure changes occur. Furthermore, understanding how DNS resolvers behave during DNS queries is pertinent; lookup failures or DNS propagation delays can give rise to SPF fail scenarios that disrupt legitimate email flows.
Lastly, administrators must stay vigilant against indirect includes pulling from third-party domains that may alter SPF DNS records unexpectedly, leading to unpredictable SPF record behavior and potential email deliverability issues.