Having more than one domain registered under your organization’s name is not uncommon, but their security seriously is. Most organizations have multiple domains, out of which they use only one or two to send emails; the rest exist to protect brand identity, for future expansion, or to redirect traffic. Out of all these domains, the unused ones are often neglected when it comes to email security, because after all, they aren’t used to send any emails.
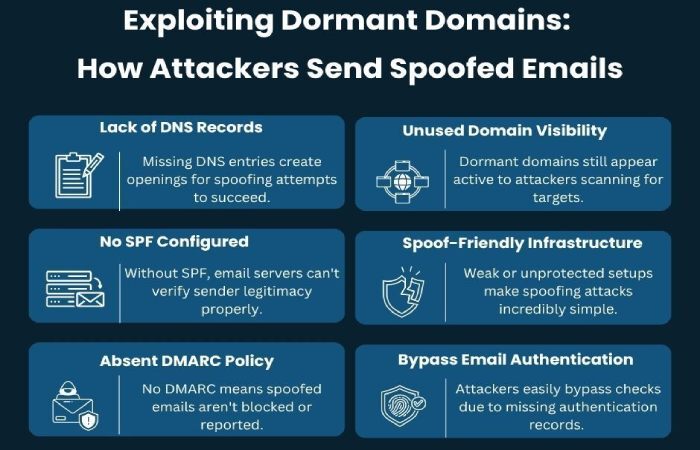
But here’s a catch: the attackers are waiting for you to leave gaps in your security, so that they can exploit these dormant domains to send spoofed emails that appear to come from your organization. And since these domains aren’t used to send any emails, chances are that you might not even bother setting up proper authentication records like SPF, DKIM, or DMARC for them. And that’s exactly what makes them vulnerable. If there are no records telling email providers what to do with messages that claim to come from these domains, attackers get a free pass.
In this article, we will understand how you can protect these dormant or parked domains by configuring SPF with a hardfail rule (-all). But before that, let’s take you through what these parked domains are and why attackers target non-email-sending domains.
What are parked or non-email sending domains?
As you might have already guessed, parked or non-email-sending domains are domains that your organization owns, but doesn’t actually use to send emails.
Let’s say your primary domain is yourcompany.com, and that’s the one you use for your website and email, like info@yourcompany.com. But maybe you also bought yourcompany.in, yourcompany.org, or some product-specific domains like yourproduct.com, just to protect your brand, or keep them for future use. So, these domains are parked domains, as they are not used to send emails, and nothing’s hosted on them.
It’s easy to think that you don’t need to protect these domains because you aren’t actively using them, but that’s where things go wrong. That’s exactly what attackers count on: the fact that these domains are ignored. Even if you’re not using them, you still need to protect them, or someone else might.
Why do attackers target non-email-sending domains?
Because they know you’re not watching them.
Even if your domain isn’t being used to send emails, it’s still on the radar of the attackers. Since these domains usually don’t have any email security set up, there’s nothing stopping those fake emails from being delivered. Most people won’t notice the small change in the domain name, and they’ll trust the email. That’s why cybercriminals consider these domains as their prime targets.
What is SPF, and how does it help in protecting your parked domains?
Clearly, you cannot let your parked domains sit without proper protection. You need to safeguard them with basic email authentication measures, and SPF is the first step.
SPF, or Sender Policy Framework, is a simple way to tell email providers which servers are allowed to send emails on behalf of your domain. For parked domains, you can use SPF to say exactly that.
While implementing SPF, remember that you don’t have to list any servers or IPs because there are none sending emails on your behalf. But you do have to make that explicit by adding a hardfail rule. Your SPF record should look like this:

v=spf1 -allBy setting your SPF record to hardfail (-all) qualifier, you’re essentially telling the mail servers that no emails should ever come from this domain and if an email does come in, it should be rejected immediately.
The hardfail (-all) qualifier isn’t usually recommended for domains that send legitimate emails, unless you’re absolutely sure all sending sources are correctly listed. But for non-email-sending domains, a hardfail is exactly what you need. It’s a simple but strong way to block spoofed emails and protect your brand from silent abuse.
What are the common mistakes to avoid while setting up SPF for parked domains?
Here’s what you should not do while implementing SPF for your parked domains:

Using the wrong qualifiers
This is one of the most common and overlooked mistakes. Using ~all (softfail) or ?all (neutral) doesn’t offer strong protection. For a parked domain, always use -all to ensure that any email pretending to come from that domain is rejected immediately.
Adding multiple SPF records
Regardless of whether you’re implementing SPF for an active or a parked domain, you should never publish more than one SPF TXT record. If you have multiple SPF records, email servers may treat them as invalid and ignore them completely, leaving your domain unprotected. So, for non-email sending domains, all you need is a single record like “v=spf1 -all”.
Forgetting to publish SPF for all owned domains
Most organizations add an SPF record to their primary domain, but forget about the others they’ve bought. Even if you are not using the domain, you still need to protect it because attackers can use it to send fake emails that look like they’re from you. Leaving these domains unprotected is like leaving the doors open for spoofing.
Not testing the SPF record after publishing
Just adding the SPF record isn’t enough; you need to check if it’s working. Sometimes, small mistakes in the setup can make the record invalid. So, once you have published the SPF record for your parked domains, make sure to use online tools. These tools will show whether your SPF record is valid and doing what it’s supposed to — blocking emails from unauthorized sources.

Wrapping up
Your parked domains might be quiet, but they’re not invisible, especially not to cybercriminals. If you leave these domains unprotected, attackers can easily use them to send fake emails that look like they’re coming from your organization. Setting up a simple SPF hardfail record (v=spf1 -all) is one of the easiest and most effective ways to stop that.
To get started, reach out to us today!