
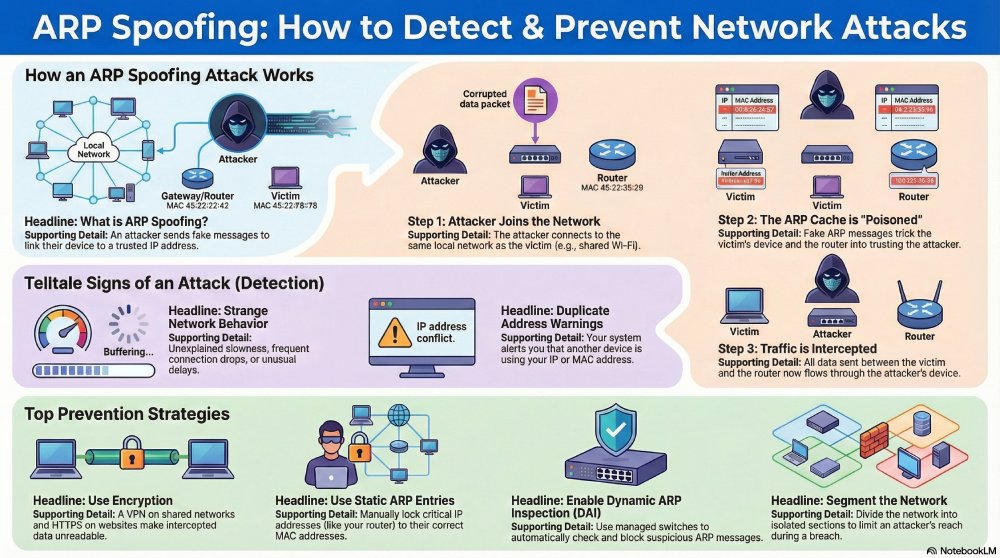
ARP spoofing, also known as ARP poisoning, is a type of network attack that targets how devices communicate inside a local network, such as a home or office Wi-Fi network.
To understand ARP spoofing, it helps to know what ARP does. The Address Resolution Protocol (ARP) connects an IP address to a physical device address, called a MAC address. This mapping allows devices on the same network to find and talk to each other. Each device stores these mappings in a temporary list, called the ARP cache, and accepts ARP responses without verifying them.
Since ARP was not designed with security in mind, any device on the network can send an ARP reply, even if no one asked for it. Devices automatically trust these replies.
In an ARP spoofing attack, an attacker sends fake ARP messages that link their own MAC address to a trusted IP address, such as the router or default gateway. When the network accepts this false information, traffic intended for the real device is redirected to the attacker.
How does an ARP spoofing attack occur

To understand ARP spoofing, it helps to look at what happens step by step inside a local network:
Step 1: The attacker joins the network
An ARP spoofing attack can only happen if the attacker is already connected to the same network as the victim. This could be through shared Wi-Fi, an open network, or a hacked device. Once inside, the attacker checks which devices are active on the network. The main targets are usually a user’s device and the router.
Step 2: Fake ARP messages are sent
Next, the attacker sends fake ARP messages to both the user’s device and the router. These messages lie and say that the attacker’s device is linked to the router’s IP address. Because ARP does not check if this information is real, both devices believe it and save it in their ARP cache. This step is called ARP cache poisoning.
Step 3: Network traffic passes through the attacker
After the ARP cache is poisoned, data sent between the user and the router is routed through the attacker’s device first. The attacker can now watch the data, change it, or block it without the user noticing. This is how ARP spoofing is used to carry out man-in-the-middle attacks and other network abuse.

Common targets of ARP spoofing attacks
ARP spoofing mostly affects networks where many devices are connected together and trust each other without checking. Offices and businesses using local IPv4 networks are common targets because a single compromised device can put the entire network at risk. Public Wi-Fi networks, like those in coffee shops, hotels, airports, or co-working spaces, are also easy targets, as attackers can join them with little effort.
Remote and hybrid workers are at higher risk when they use home or public Wi-Fi to access work systems. Small businesses are especially vulnerable because they often do not have strong network security or monitoring in place. In simple terms, any shared network that does not verify devices properly can be affected by ARP spoofing.
Ways to detect ARP spoofing

Here are some common clues that can help you notice the early signs of ARP poisoning:
Strange network behaviour
The internet may feel slower than usual, internal tools may take longer to load, or websites may open with delays. These issues can happen for many reasons, but if they keep happening without a clear cause, it may mean network traffic is being redirected or watched.
Problematic ARP table
You can also look at the ARP table on a device. This table shows which IP address is linked to which MAC address. If the MAC address for the router or gateway keeps changing, it can be a sign of ARP cache poisoning. Sudden or repeated changes in this table should not be ignored.
Duplicate IP or MAC addresses
Sometimes, systems show warnings about duplicate IP or MAC addresses. This means more than one device is claiming the same identity on the network, which can happen during an ARP spoofing attack.
Unexpected connection drops
Another warning sign is unexpected connection drops. Calls may disconnect, sessions may time out, or connections may reset without any changes to the network. This can happen when an attacker is interrupting or delaying traffic while intercepting data.
Monitoring tools
For deeper checks, network monitoring tools are very helpful. These tools watch network traffic and ARP activity in real time. They can spot unusual ARP messages, frequent address changes, or mismatches between IP and MAC addresses. This is especially useful in larger networks where manual checks are not practical.

Ways to prevent ARP spoofing attacks
While ARP spoofing cannot be completely eliminated, the risk can be reduced with basic security steps and proper network settings.
Use static ARP entries
Static ARP entries lock an IP address to a specific MAC address. This prevents fake ARP messages from changing trusted mappings. These entries are best used for devices that rarely change, such as routers, firewalls, and core servers. They reduce attack risk but require manual updates if hardware is replaced.
Enable encryption
Encryption protects data while it is moving across the network. Even if an attacker intercepts the traffic, they cannot read or easily modify the information. Protocols like HTTPS, TLS, and SSH ensure sensitive data stays protected. This is especially important for logins, emails, and internal applications.
Use a VPN on shared networks
A VPN creates a secure, encrypted tunnel between the device and a trusted server. This keeps data hidden from attackers on the same local network. VPNs are highly effective for remote employees and travelers using public Wi-Fi. They prevent local attackers from viewing or tampering with network traffic.

Apply packet filtering
Packet filtering tools monitor network traffic and block suspicious or unauthorized ARP messages. This helps prevent devices from accepting fake address information. Filtering rules can limit which systems are allowed to send ARP responses. This reduces the chance of attackers injecting forged packets into the network.
Turn on dynamic ARP inspection
Dynamic ARP Inspection checks ARP messages against trusted sources before allowing them through. Invalid or mismatched ARP packets are blocked automatically. This feature is commonly available on enterprise-grade switches. It provides real-time protection without relying on manual checks.
Use managed network switches
Managed switches provide better control over network traffic. They support security features that prevent devices from impersonating trusted systems. These switches allow administrators to monitor ARP activity across ports. This makes it easier to detect and stop suspicious behavior early.
Segment the network
Network segmentation divides the network into smaller, isolated sections. If ARP spoofing occurs in one segment, the attacker cannot easily move further. This limits the impact of an attack and protects critical systems. Segmentation is especially useful in office and industrial environments.
Keep systems and firmware updated
Regular updates fix known security issues in operating systems and network devices. Updated firmware often includes protections against ARP-based attacks. Outdated routers and switches are easier targets for attackers. Keeping systems updated reduces exposure to known weaknesses.
Train users
User awareness is an important defense against ARP spoofing. Teaching users to avoid unknown or unsecured Wi-Fi reduces attack opportunities. Users should also report unusual network behavior quickly. Early reporting helps security teams respond before serious damage occurs.
ARP spoofing tricks networks to intercept data, but using AutoSPF, SPF, DMARC, and DKIM strengthens cybersecurity and helps detect and prevent attacks.
Conclusion
ARP spoofing is a simple but dangerous network attack that takes advantage of trust inside local networks. Because it works quietly, many users and organizations do not notice it until real damage is done. Understanding how ARP spoofing works, how to detect early warning signs, and how to apply basic protections can greatly reduce risk.
Simple steps like encryption, network monitoring, and secure configurations make a big difference. While ARP spoofing cannot be fully eliminated, its impact can be controlled with the right security practices. A well-protected network makes it much harder for attackers to intercept data or disrupt communication.






