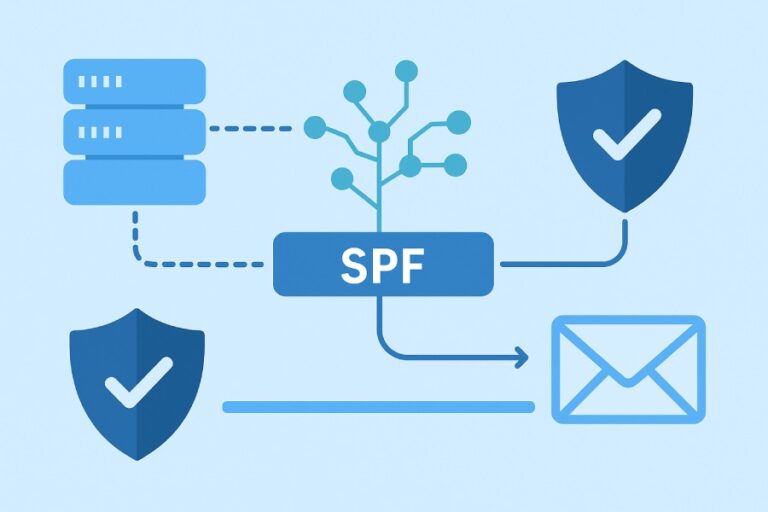
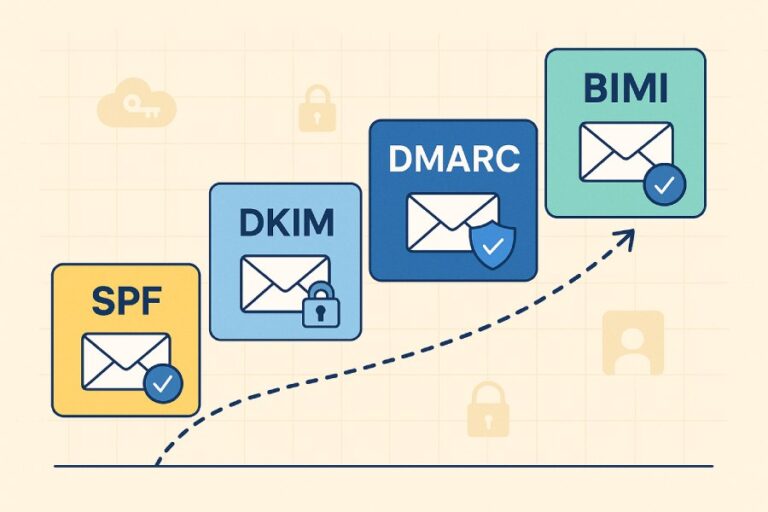
Complete Guide to Setting Up FreshMail DKIM and SPF Records
In today’s email ecosystem, ensuring your messages are authenticated and trusted by recipients isn’t just a nice-to-have — it’s essential. Every day, millions of emails are sent for marketing, notifications, and transactional purposes. But without proper authentication, your carefully crafted messages could land in spam folders — or worse, be blocked entirely. At AutoSPF, we…