While many industries have progressed with zero-trust architectures and multi-factor authentication, it’s the banking industry that is still dealing with its hyper-vulnerability to email-based attacks. On the other hand, customers still believe that if an email has the bank logo, domain name, and a polished language, it must be real. This is the very assumption that threat actors take advantage of and create sophisticated email campaigns that are meant to steal credentials, authorize payments, or request confidential information.
Email remains the top attack vector. IC3 and industry reports estimate losses at $16.6B in 2024, yet many banks still lack strict enforcement of email authentication protocols. Considering such statistics and the growing number of phishing and spoofing attacks, regulators like the FFIEC, RBI, and EU are emphasizing secure customer communication. However, the sad truth is that despite the tightened expectations by the regulatory bodies, spoofed banking domains continue to circulate, tricking customers into approving fraudulent transactions or handing over OTPs.

SPF, DKIM, and DMARC work in tandem to help banks (and other industries) ensure that only legitimate emails sent from their domain land in the primary inboxes of the intended recipients. However, when these protocols are misconfigured, the entire email authentication exercise takes a toll, leaving room for false positives, false negatives, and other security gaps.
This blog discusses explicitly the common SPF misconfigurations that put banks and their customers at risk.
Common SPF misconfigirations
SPF misconfigurations are a common problem because it’s a sensitive protocol that has many rules to be followed. At times, email are delivered yet their protections are bypassed which ultimately leads to blind spots. For financial institutions with dozens of vendors and high customer interaction, small SPF mistakes can scale into systemic risks. Here’s what usually happens-

Too many DNS lookups
SPF policies allow a maximum of 10 DNS lookups. Large banks often exceed this limit because they use multiple third-party platforms, such as loan servicing vendors, marketing agencies, card promotion systems, and outsourced IT mailers. When this ceiling is crossed, DNS queries beyond the 10th are ignored, meaning critical mail servers may be left unverified.
Overly permissive +all or ~all
Some institutions configure SPF to accept all sources (+all) or to soft-fail mail from unauthorized servers (~all). While convenient during initial deployment, these weaken enforcement and effectively give attackers room to send phishing emails that appear compliant. Banks using permissive mechanisms reduce the deterrent value of SPF to almost zero.

Duplicate or outdated entries
In fast-changing vendor environments, old SPF entries are often left behind. Duplicate or stale records increase DNS lookup counts unnecessarily and may cause inconsistent evaluation across mail gateways. This not only reduces reliability but also complicates auditing during compliance checks.
Improper IP or third-party inclusion
Banks frequently rely on fintech partners, card processors, and global service providers. Failure to properly include their sending IPs or domains results in false negatives, where legitimate emails fail SPF validation. Customers may stop receiving transaction alerts or OTPs, undermining trust and operational continuity.

How misconfigured SPF records fuel phishing campaigns against banks?
Misconfigured SPF records not only create technical inefficiencies, but they also directly enable phishing campaigns targeting banks and their customers. Attackers thrive on gaps in email authentication, and every weak or broken SPF entry provides another opportunity to slip past filters. In a sector where trust defines customer relationships, even a handful of spoofed emails can escalate into large-scale fraud.
Spoofed bank domains
When SPF enforcement is weak or absent, attackers easily impersonate a bank’s domain to send ‘secure alerts’ about suspicious logins, blocked cards, or account verification. These messages often carry links to credential-harvesting sites that closely resemble the bank’s portal. Because the spoofed email header looks authentic, customers are more likely to respond.

Fraudulent transaction approval emails
Attackers often exploit broken SPF checks to send fraudulent approval requests. A spoofed email asking customers to verify a wire transfer or approve a card payment can slip into inboxes unchecked. These attacks bypass customer skepticism because they appear to come from legitimate, trusted addresses and often mimic real workflows.
Internal spoofing risks
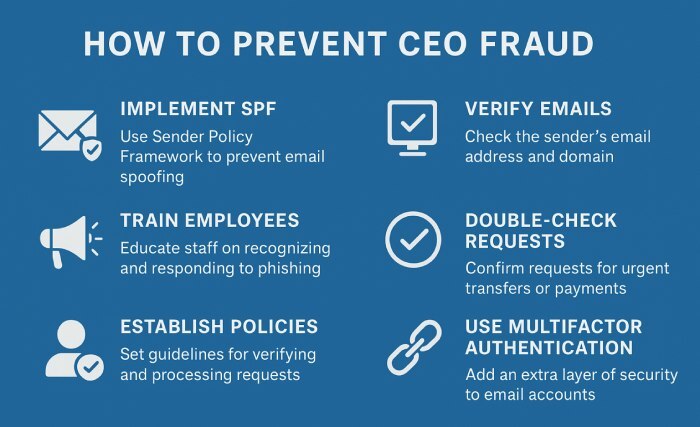
Weak SPF records also expose banks to internal spoofing. Threat actors mimic executives or department heads, sending fake requests for urgent transfers, payroll changes, or vendor payments. Known as CEO fraud, these scams exploit authority and urgency. Without strict SPF alignment, internal systems may fail to flag these as suspicious.
Erosion of customer trust
Every successful spoofing attempt chips away at brand integrity. Customers quickly lose confidence when fraudulent bank emails repeatedly surface, even if they do not fall victim. Beyond reputational harm, banks risk regulatory scrutiny, lower security ratings, and potential fines for failing to safeguard digital communication channels.
To strengthen email security and minimize SPF misconfigurations, banks can adopt automated SPF flattening tools that ensure DNS records remain accurate, optimized, and compliant with policy requirements.






