AutoSPF’s Complete Guide: How to Add an SPF Record in Namecheap
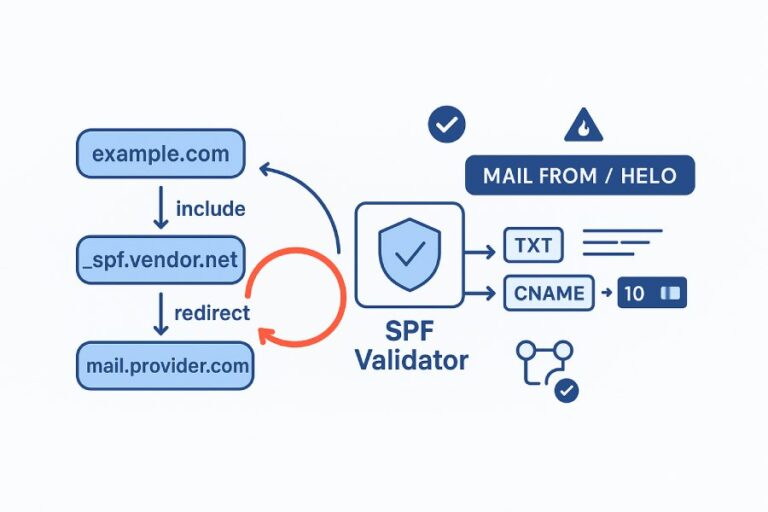
In today’s digital world, securing your email domain against spoofing, phishing, and spam isn’t just a technical best practice — it’s essential for protecting brand reputation, ensuring deliverability, and preserving trust with your customers and partners. One of the foundational email authentication protocols that every domain owner should implement is SPF, or Sender Policy Framework….