At AutoSPF, we know that email authentication isn’t an optional add-on — it’s a foundational requirement for any business that wants reliable inbox delivery and protection from fraud, spoofing, and malicious impersonation. When you’re using an email security service like SpamHero, proper setup of Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) records is essential to ensure that your legitimate mail streams are trusted by recipient mail servers, pass modern authentication checks, and don’t get erroneously flagged as spam.
In this guide, we’re going to walk you through everything you need to know to configure SPF and DKIM for SpamHero — and why these records matter — from an AutoSPF perspective. By the end, you’ll understand both how to implement these records and why they’re essential for effective email authentication.
Why Email Authentication Matters
Before we jump into step-by-step configuration, let’s make sure the “why” is clear.
Modern mail systems like Gmail, Yahoo, Outlook, and others don’t just trust that an email claims to be from your domain — they verify using authentication protocols like SPF, DKIM, and DMARC. These protocols help receiving servers determine:
- That the sending source is actually authorized by you,
- That the message hasn’t been tampered with in transit,
- And that the sender’s domain isn’t being spoofed for phishing or spam attacks.
Without proper SPF and DKIM records in DNS, even legitimate messages sent through trusted platforms like SpamHero can be delayed, marked as spam, or rejected outright.

At its core:
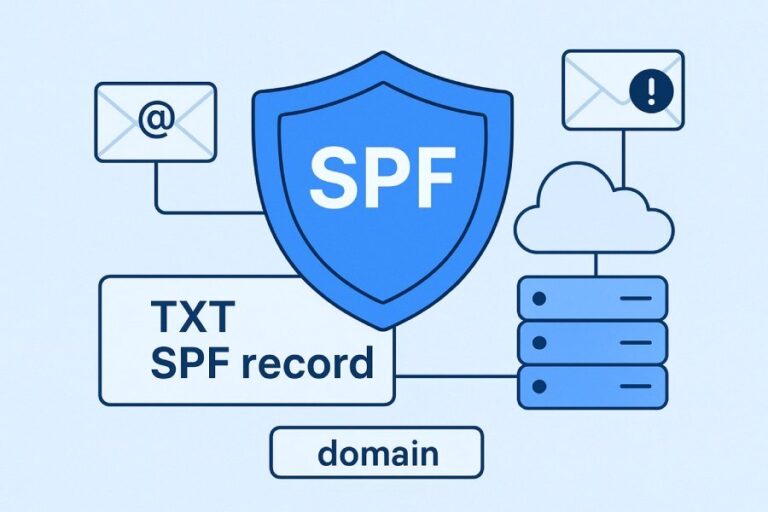
- SPF specifies which servers are allowed to send email on behalf of your domain.
- DKIM uses cryptographic signatures to verify that the content of your message hasn’t been altered and that it was legitimately sent by your sending domain.
The combination of these mechanisms signals to receiving mail servers and anti-spam systems that your emails are authentic — which improves inbox placement and protects your brand reputation.
SpamHero & Email Authentication: What You Need to Know
SpamHero is a powerful email security and outbound mail management platform, widely used for filtering inbound spam as well as handling outbound mail. But simply signing up for SpamHero isn’t enough — if your SPF and DKIM records aren’t configured correctly, SPF will fail and your mail can land in spam folders.
According to documentation from EasyDMARC, SpamHero currently does not support DKIM for outbound mail, which means SPF is the primary authentication protocol you can use for SpamHero and DMARC checks will rely on SPF passing successfully.
That makes setting up your SPF record correctly even more critical.
Step-by-Step: Configuring SPF for SpamHero
Let’s start with SPF, because this is the record SpamHero does rely on.
1. Access Your DNS Provider
Log into the control panel of the registrar or DNS hosting service that manages your domain’s DNS zone file. This might be services like Cloudflare, GoDaddy, AWS Route 53, or similar.
Find your DNS zone management page — this is where TXT records, A records, MX records, and SPF records are managed.
2. Create or Update the SPF TXT Record
You need a single TXT record for SPF per domain (only one is allowed — more than one will cause SPF to break). If you don’t already have an SPF record, you’ll create a new one. If you already have one, you’ll need to merge SpamHero into it (more on that below).
Here’s the SPF value you will use for SpamHero:
v=spf1 include:spf.spamhero.com ~allThis tells the world’s mail servers that SpamHero’s mail sending infrastructure is authorized to send on behalf of your domain.

Steps:
- Click “Add TXT Record” in your DNS dashboard.
- In the Name/Host field, enter your domain or use “@” to represent the root domain.
- In the Value or TXT Data field, enter:
v=spf1 include:spf.spamhero.com ~all- Save the record.
3. Merge with Existing SPF Records (If Needed)
Domains commonly already have SPF records from other email services — like Google Workspace, Microsoft 365, CRM platforms, marketing automation tools, etc.
However, DNS only allows one SPF TXT record per domain. If you already have an SPF record, you need to merge the SpamHero include into it — otherwise DNS will return a “PermError” and SPF won’t work at all.
Example:
Old Record
v=spf1 include:_spf.google.com ~allMerged Record
v=spf1 include:_spf.google.com include:spf.spamhero.com ~allMake sure all your email sources are included before the final ~all (which means “soft fail anything not listed here”). A good practice is to work with tools that can validate merged SPF values; AutoSPF provides automated merging so you don’t accidentally exceed DNS lookup limits or introduce syntax errors.
4. Wait for DNS Propagation
DNS changes don’t take effect instantly. In most cases, it can take up to 72 hours for the new SPF record to fully propagate across the global DNS network.
During this time, some mail servers will immediately start checking against the new record, while others will continue using cached DNS data.
5. Validate Your SPF Record
Once the DNS changes have had time to propagate, use SPF validation tools (such as AutoSPF’s SPF analyzer) to confirm:
- The record is syntactically correct,
- Your domain has only one SPF record,
- And that SpamHero is correctly included.
This helps ensure that email receivers will use the correct SPF policy for authentication checks.

What About DKIM with SpamHero?
Now let’s talk about DKIM.
According to documentation, SpamHero does not currently support DKIM signing for outbound mail directly, which means one of two things:
- If SpamHero did support DKIM signing, you would generate DKIM keys and publish a public key as a DNS TXT (or CNAME) record pointing to the key.
- But in this case, you’ll rely largely on SPF for DMARC alignment — which is fine if SPF passes and aligns with your domain.
However, it’s still good to understand what DKIM would do if available:
- DKIM signatures attach a cryptographic signature to the message headers,
- Receiving mail servers retrieve the public key from DNS,
- And they validate that the message was actually sent by your sender and hasn’t been altered in transit.
Because DKIM is widely recognized as a best practice, many ESPs and outbound mail platforms will sign on your behalf. If in future SpamHero adds DKIM support, you would:
- Enable DKIM signing from within the SpamHero control panel.
- Publish the DKIM selector and public key in your DNS (likely via a CNAME or TXT, depending on SpamHero’s instructions).
- Validate signatures with DKIM lookup tools.
For now, SPF remains your primary mechanism with SpamHero.
SPF, DKIM, and DMARC: How They Work Together
You may also be wondering how SPF and DKIM relate to DMARC.
DMARC stands for Domain-based Message Authentication, Reporting & Conformance and is a higher-level policy that sits on top of SPF and DKIM to tell receiving mail servers:
- What to do if SPF or DKIM fail, and
- Whether to send you reports on failures.
DMARC checks whether:
- SPF passed and aligned, or
- DKIM passed and aligned.
Alignment means that the domain in the “From” header matches the domain used for SPF or DKIM validation.
With SpamHero relying on SPF today, you’ll want to ensure your SPF record passes and aligns with your domain so your DMARC policy (if published) functions correctly.
If you haven’t published a DMARC record yet, you can do so with tools like DMARC generators, where you choose your preferred policy (none, quarantine, reject) and reporting options.

Troubleshooting and Best Practices
Even after setup, SPF issues can still occur. Here are common pitfalls and how to address them:
Multiple SPF Records
DNS allows only one SPF TXT record.
If you create a second record for SpamHero instead of merging — SPF fails entirely.
Fix: Merge all sources into one and validate with an SPF checker.
Exceeding DNS Lookup Limits
SPF records that include too many services can hit the DNS lookup limit (10 maximum).
AutoSPF can flatten records or optimize includes to stay within limits.
Delayed DNS Propagation
Sometimes it just takes time. If you’ve recently updated your DNS and authentication still isn’t passing, wait the full propagation window.
SPF Doesn’t “Align”
Even if SPF passes, DMARC can still fail if domains don’t align.
These alignment issues are why DKIM signing (when available) helps — the signature is tied to the domain in the header.