During the 2024 Black Friday to Cyber Monday (BFCM) period, Mailchimp customers sent billions of emails. Notably, on Black Friday alone, over 133 million emails were dispatched in a single hour. On the other hand, SendGrid claims to send 148+ billion emails every month. And at the same time, there has been a massive 202% increase in email-based attacks! If we look at these big numbers, then one thing is clear— email is the backbone of the corporate world. But it’s also true that the email pool is unsafe..
While Google, Yahoo, Outlook, and groups like PCI and DORA are pushing the adoption of SPF, DKIM, and DMARC, SPF is struggling to keep up. Many companies use multi-tenant email services, where lots of senders share the same system. SPF was built to be simple, but these shared setups are making it harder for SPF to work well.
This blog highlights the challenges SPF faces on platforms like MailChimp, SendGrid, HubSpot, etc., and how these platforms address the issue.

What is a multi-tenant email service provider?
A multi-tenant email service provider is a software architecture in which a single instance of the email platform and its underlying infrastructure serves multiple customers or tenants. Each tenant’s data is isolated and remains invisible to others, but they all share the same application, codebase, and resources—like servers, IPs, and databases (with logical separation). This creates problems for SPF.
SPF challenges in multi-tenant scenarios
SPF is a sensitive protocol— even a small mistake can invalidate the SPF record and stop it from properly checking emails. Here are the reasons why SPF struggles with email service providers’ platforms-
SPF alignment issues
One of the biggest problems SPF faces in multi-tenant scenarios is domain alignment, which is crucial for DMARC compliance. SPF functions by checking the Return-Path domain or the envelope sender, and not the ‘From’ address that recipients see. However, in a multi-tenant environment, the Return-Path mostly uses a shared domain. So, if the visible ‘From’ domain and the Return-Path domain are different, the SPF check might pass, but DMARC will surely fail. DMARC requires an exact match between these two domains.
But you may question how it is a problem if emails with misaligned domains are already passing SPF. Well, even if SPF is passing technically, you won’t get the protection (or deliverability boost) that DMARC enforcement promises.
SPF record limitations
The SPF record can only include 10 DNS lookups. Each include, a, mx, or ptr mechanism can trigger lookups. So, if a tenant tries to authorize multiple sending services, they might hit the 10-lookup limit, causing SPF to break silently.

What’s worse is that some tools automatically add entries to the SPF record, leading to unexpected lookup bloat or conflicts between services. This limit becomes a serious issue in shared environments where many IPs need to be covered.
A broken SPF record can potentially cause deliverability issues without the sender’s knowledge, which is what attackers look for.
IP reputation sharing
Multi-tenant platforms usually send emails from a shared pool of IP addresses, which can be a double-edged sword. If one tenant sends spam or violates best practices, it can harm the reputation of the shared IP. Since SPF only checks if the IP is authorized to send for a domain, it doesn’t distinguish between different senders (tenants) using the same IP.
What this means is that even if your content is clean and compliant, your emails might land in spam because someone else on the same IP misbehaved. This can also trigger reputation systems like Gmail’s spam filters to penalize the whole IP, and not just the threat actor! So, in such a case, you can be harmed by a ‘threat neighbor.’
Long-term solutions and best practices
We understand that relying on email service providers is feasible, and you can’t stop doing that. Therefore, here are some things that you can do to ensure you do not expose your business to email risks emerging from the use of multi-tenant SaaS platforms-
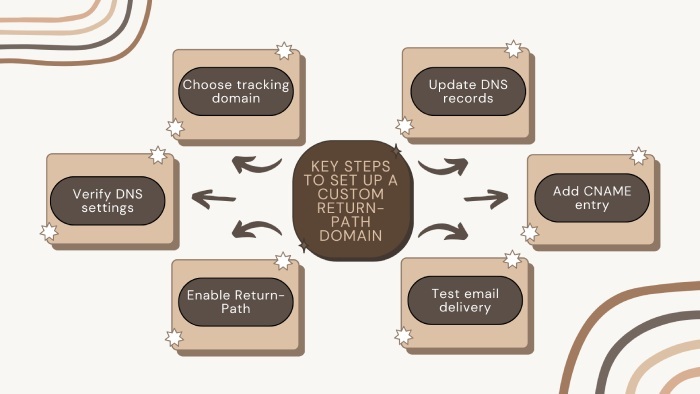
1. Set up custom Return-Path and DKIM
Ask your provider to set up a custom Return-Path domain to align SPF with your domain, further improving DMARC compliance.
Also, most ESPs offer a custom domain option, which allows your domain to appear as the signer rather than the provider’s domain. This not only helps with DKIM alignment but also strengthens your brand’s authenticity in the inbox.
2. Implement DMARC with monitoring mode
When you begin SPF implementation, it’s best to start with the monitoring mode (p=none) so that the flow of email delivery is not hampered. Also, carefully evaluate DMARC reports showing which emails are failing SPF and DKIM checks and whether they align with your domain. Monitoring lets you fix issues safely before enforcing stricter policies (p=quarantine or p=reject), reducing the risk of accidentally blocking your own legitimate emails.
Monitor SPF flattening
SPF records in a multi-tenant environment are more likely to exceed the DNS lookup limit of 10. To fix this issue quickly, use an automatic SPF flattening tool. This tool replaces complex data with a single record.
Contact AutoSPF to know more about it.