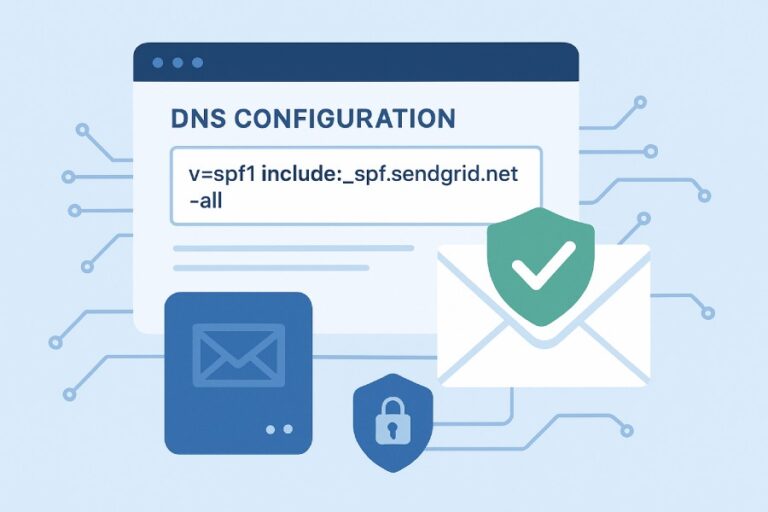
Sender Policy Framework (SPF) is an email authentication protocol designed to prevent email spoofing — a common tactic in spam and phishing attacks.
In today’s threat landscape, SPF plays a crucial role in cybersecurity by allowing receiving mail servers to verify whether an email claiming to come from your domain is actually authorized.
By implementing SPF, businesses not only strengthen their defense against impersonation attacks but also enhance email deliverability and build greater credibility with recipients.
How does SPF work?
SPF works by allowing domain owners to create a list of all the IP addresses and mail servers they trust and authorize to be used for sending official emails on their behalf. This list is stored in their domain’s DNS as a special SPF record.

This is what an SPF record looks like- v=spf1 ip4:192.168.0.1 include:_spf.google.com -all
So, when a receiving server gets an email from your domain, it queries the DNS and fetches the SPF record corresponding to your domain. It looks at the IP address of the server that sent the email and checks if that IP is listed in your SPF record.
The receiving server then makes a decision:
- Pass – IP is listed → email is likely legit.
- Fail – IP is not listed → email might be spoofed.
Now, depending on what action the domain owner has chosen, the email that fails the SPF check is either marked as spam or rejected altogether.
Why do you (a domain owner) need an SPF record?
An SPF record is a DNS entry that lists all the IP addresses and mail servers authorized to send emails on behalf of your domain. It acts as a permission slip, telling the world which sources can be trusted to use your domain for sending emails.

By implementing SPF, you reduce the risk of your emails being marked as spam or rejected altogether. This not only improves your email deliverability but also helps ensure that your legitimate emails reach the recipient’s inbox.
Keeping your SPF record updated is critical to protecting your domain’s reputation. Without it, cybercriminals can spoof your domain to send phishing or spam emails—damaging both trust and deliverability.
If you’re using third-party services like Google Workspace or Mailchimp to send emails, SPF allows recipient servers to verify that these services are permitted to send on your behalf. Without an SPF record, receiving servers may flag your messages as suspicious.
And since most people rarely check their spam folders, failed SPF checks can lead to missed opportunities or important communications.
While platforms like Gmail, Yahoo, and Hotmail have SPF for their own domains, if you’re using a custom domain, it’s your responsibility to configure SPF correctly in your DNS settings to keep your email ecosystem secure and reliable.
Limitations of an SPF record
There are some shortcomings of SPF that should be considered before its deployment-
1. DNS limitations
When an email is received, the recipient’s server checks the SPF record by performing DNS lookups, especially for include, a, mx, and redirect mechanisms.
To avoid abuse and maintain email processing speed, SPF enforces a hard limit of 10 DNS lookups per domain. This means:
- Only 10 external DNS queries can be made while evaluating an SPF record.
- Anything beyond that will trigger a “PermError”, causing SPF to fail and your email to be treated as suspicious.
This limit prevents DoS attacks while also encouraging domain owners to keep their SPF records streamlined and updated.
2. Restrictions on characters
The 255-character limit comes from DNS protocol restrictions — each single string in a DNS TXT record can’t exceed 255 characters. However, SPF records can be split into multiple quoted strings if needed, and the overall DNS response can be up to 512 bytes.
Here’s how you can stay within the limit-
- Avoid unnecessary include mechanisms (e.g., don’t include services you don’t use).
- Use IP ranges instead of listing multiple IPs individually.
- Flatten your SPF record using a tool — it replaces include with actual IPs.
- Remove obsolete or duplicate entries.

3. Possibility of multiple SPF records for large companies
Large companies with too many employees often end up having multiple SPF records, which is wrong. There should only be one SPF record per domain. If the DNS retrieves multiple SPF records for a specific sending domain, the entire verification process gets affected.
4. Unstructured email forwarding
SPF authentication can be disrupted by unstructured email forwarding. An email may fail SPF authentication if it is sent via a server that is not authorized in the SPF record.
The bottom line
Phishing attackers often fake the sender’s email address to slip past security filters. SPF helps stop this by verifying which servers are allowed to send emails from your domain. By implementing SPF as part of their email security strategy, organizations can prevent email spoofing, enhance message deliverability, and safeguard their domain’s reputation.
If you need our help in setting up or re-configuring SPF for your domain, then contact us or book a demo.