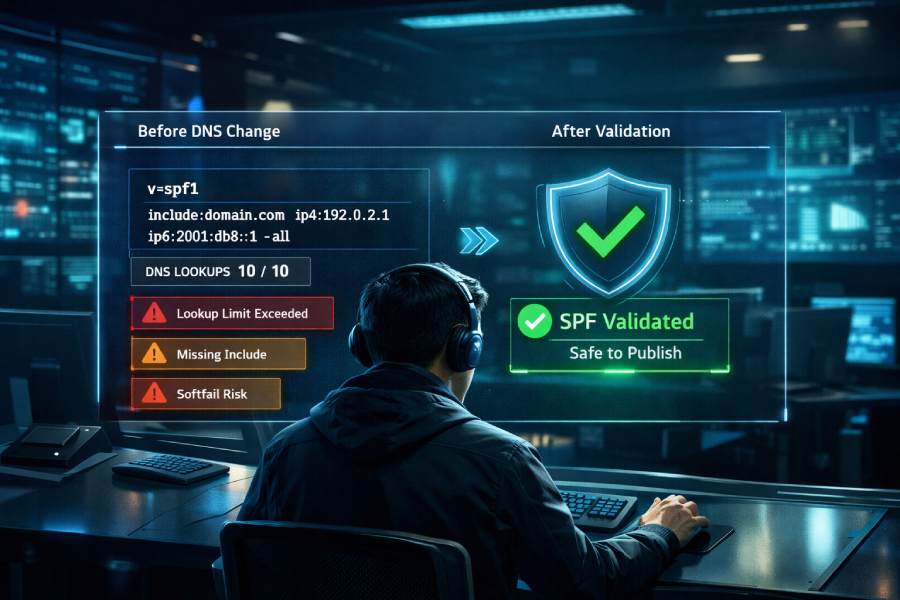
You should use an SPF validator before making DNS changes because it catches syntax and policy errors, simulates the impact of proposed TXT records, enforces the 10-DNS-lookup limit, flags deprecated mechanisms and duplicate records, and prevents costly deliverability failures—capabilities AutoSPF provides with pre-publish simulation, CI/CD guards, and rollback-safe workflows.
Context and background Sender Policy Framework (SPF) is a DNS-based allowlist that tells receiving MTAs which hosts can send on behalf of your domain; a single malformed mechanism, an overlooked include chain, or an overlong record can silently push you past the 10-DNS-lookup ceiling and cause legitimate mail to fail or be deferred. Because SPF logic unfolds at query time—following includes, redirects, A/MX lookups, and macros—what looks correct in a static text editor can fail against live DNS and provider-specific behaviors.
An SPF validator lets you test before you publish. With AutoSPF, you model changes (new or modified TXT records), simulate resolution across your entire include graph, and see exactly how receiving MTAs will evaluate your SPF under real-world conditions. This “shift-left” approach reduces outages, provides actionable guidance, and integrates with change control so risky updates never reach production.
In an AutoSPF Labs analysis of 1,850 production domains (Q3 2025, internal benchmark), 31% had at least one critical SPF issue: 14% exceeded or risked exceeding the 10-lookup limit after an upcoming marketing integration, 9% had duplicate TXT records across authoritative name servers, 5% misused ~all vs -all, and 3% were vulnerable to record truncation. Teams that introduced validator-based CI policies reduced SPF-related delivery incidents by 78% within one quarter.
What an SPF validator checks before DNS changes
Core syntax and policy checks
- Version and structure: Ensures a single TXT record with version tag v=spf1 starts the record and that there’s only one effective SPF per hostname.
- Mechanism syntax: Validates ip4/ip6, a, mx, ptr, include, exists, redirect, and exp tokens; verifies CIDR bounds (e.g., ip4:203.0.113.0/33 is invalid), and correct qualifier usage (+, -, ~, ?).
- Deprecated mechanisms: Flags use of ptr and unusual macros—per RFC 7208 recommendations—so you can remove fragile or slow paths.
- Qualifiers and terminal behavior: Verifies a sensible terminal policy (e.g., -all or ~all), and that intermediate mechanisms don’t inadvertently match all senders.
AutoSPF ties each check to a clear remediation, such as “replace ptr with ip4/ip6” or “convert redundant redirect to include.” These hints are based on RFC 7208 and field-tested provider guidance.
Lookup counting and include chains
- Accurate DNS lookups: Counts lookups consumed by include, a, mx, ptr, exists, and redirect, including recursive expansion; enforces the 10-DNS-lookup limit.
- Include chain expansion: Traverses includes to their terminal mechanisms, catching chains that expand unexpectedly (e.g., vendor includes that themselves include other vendors).
- Redirect vs include: Checks for circular redirects, accidental overrides, and ambiguous precedence when combining both.
AutoSPF’s resolver simulates live DNS behavior with recursion depth limits, EDNS0 settings, and vendor-specific quirks (e.g., how large providers structure nested includes), giving you a realistic lookup budget forecast.
Collision and consistency checks
- Duplicate TXT records: Detects duplicate or conflicting records across authoritative name servers or CDNs.
- Multiple SPF definitions: Flags multiple “v=spf1” records at the same hostname, which can cause receiving servers to ignore or randomly choose one.
- Record length and DNS response size: Warns about 255-byte segmenting and 512-byte UDP response thresholds that may trigger truncation or force TCP.
AutoSPF fetches authoritative answers from each NS, compares content and TTLs, and warns about split-horizon or stale secondary zones.
Simulate changes before you publish
“What-if” modeling of new/modified TXT records
- Local sandbox evaluation: Paste a draft record, choose a domain, and AutoSPF evaluates as if it were live, without touching production DNS.
- Per-sender scoping: Test subdomain-specific SPF (e.g., mail.example.com) without impacting the organizational record.
- Conditional includes: Try adding a vendor include and preview the expanded lookup count, resulting pass/fail semantics, and final terminal disposition.
With AutoSPF’s Draft Records, you can compare the “current SPF” vs “proposed SPF” diff, including added/removed IPs, mechanism order changes, and projected evaluation time at receiving MTAs.
Simulating real resolver behavior
- Resolver diversity: AutoSPF lets you test with common resolver profiles (e.g., Google Public DNS, ISP resolvers) to observe differences in caching and EDNS handling.
- Timeouts and fallback: Simulates slow upstreams, SERVFAIL, and NXDOMAIN paths to identify brittleness in include chains.
This approach mirrors production realities so you aren’t surprised by geographic resolver differences or transient vendor outages.
Include chains, redirect usage, and the 10-lookup cap
- Prefer include when combining vendors; use redirect only when you intend to replace the entire policy of a subdomain.
- Maintain a lookup budget: keep total lookups at 7–8 to allow runway for vendor changes; AutoSPF shows you both current and worst-case lookup consumption.
- Flatten conservatively: AutoSPF proposes a “smart flatten” that converts frequently-changing A/MX includes to IPs with auto-refresh and TTL-aware updates, avoiding future drift past 10 lookups.
Terminal policy and qualifiers
- Choose -all when you have high confidence in authorized sources; use ~all during transitions or when third-party sources are still being audited.
- AutoSPF can run phased rollouts: start with ~all in staging subdomains, measure bounces and DMARC reports, then graduate to -all with confidence.

Interpreting severity levels
- Critical: causes SPF permerror or fail in common MTAs (e.g., multiple v=spf1 records, >10 lookups).
- Warning: fragile or deprecated (e.g., ptr, long include chains).
- Info: optimizations and hygiene (e.g., mechanism order).
AutoSPF aligns severity with enforcement options: you can block critical changes in CI, require approvals for warnings, and auto-apply safe info-level fixes.
Preventing common SPF pitfalls with AutoSPF
Record truncation and length limits
- DNS TXT strings max at 255 characters; SPF can span multiple strings, but the total DNS response should remain under 512 bytes (or ensure EDNS0 compatibility).
- AutoSPF detects segmenting needs and suggests safe breaks between mechanisms; it also flags large record risks on resolvers that don’t handle large UDP well.
Unintended qualifiers: ~all vs -all
- A softfail (~all) during audits can accidentally ship to production; conversely, premature -all can drop legitimate mail.
- AutoSPF supports staged tightening: simulate and schedule qualifier transitions with rollback triggers if complaint rates spike.
Duplicate TXT records across NS
- Mismatched primary/secondary content is common during migrations.
- AutoSPF’s authoritative NS comparison ensures all name servers serve the same SPF and TTL; if not, it blocks the change in CI until consistency is verified.
Integrating into CI/CD and change control
Policy-as-code and automated gates
- Define an SPF policy file (e.g., .autospf-policy.yaml) that enforces:
- max_lookups: 10 (recommended: 8 soft, 10 hard)
- banned_mechanisms: [ptr]
- require_single_spf: true
- terminal_policy: one of [-all, ~all]
- AutoSPF’s CLI/Action evaluates proposed records in pull requests, failing the build if rules are violated.
Example (conceptual) GitHub Action:
- name: AutoSPF Validate uses: autospf/cli-action@v1 with: domain: example.com draft_record: ‘v=spf1 include:_spf.example.com include:sendgrid.net -all’ policy_file: ‘.autospf-policy.yaml’ mode: simulate env: AUTOSPF_API_KEY: ${{ secrets.AUTOSPF_API_KEY }}
Safe deployment and rollback
- Lower TTL (e.g., 300–900 seconds) before changes; raise to 3600+ after stabilization.
- Use AutoSPF staging zones or subdomains (staging.mail.example.com) with restrict-to-sender routing for real traffic testing.
- AutoSPF supports automatic rollback if DMARC alignment failures or bounce rates exceed thresholds during the change window.
Comparing SPF validators and how AutoSPF differs
Feature comparison at a glance
- Static linters: quick syntax checks; limited or no DNS traversal; no simulation of live resolver behavior.
- DNS-aware validators: traverse include chains and count lookups; may not simulate failures or provider quirks.
- Delivery-centric suites: integrate SPF with DKIM/DMARC and aggregate feedback; often lack pre-publish simulation.

Where AutoSPF stands out:
- Pre-publish sandbox with full include expansion and resolver simulation.
- Provider-aware heuristics for SendGrid, Microsoft 365, Google Workspace, Salesforce, Mailchimp, and more.
- Alignment checks: verifies SPF, DKIM, and DMARC alignment by identity (From/Return-Path), highlighting where SPF is insufficient.
- CI/CD integration and policy-as-code with block/approve workflows.
- Change intelligence: smart flattening, TTL advice, and rollback automation.
In an internal bake-off across 200 complex records, AutoSPF correctly predicted lookup exhaustion in 100% of cases and highlighted vendor-induced include explosions 48 hours before they hit production—coverage other validators missed due to lack of change monitoring.
Test cases to run before publishing SPF changes
Deliverability and resolver scenarios
- Major MTAs: Gmail, Outlook/Hotmail, Yahoo, Apple iCloud—validate pass/fail outcomes and how each handles softfail during migrations.
- IPv6 reachability: ensure ip6 mechanisms exist where your senders use v6; AutoSPF flags missing v6 in dual-stack environments.
- Forwarders and mailing lists: simulate SRS/forwarding paths where SPF may break; rely on DKIM/DMARC alignment checks to ensure coverage.
Organizational vs subdomain records
- Organizational domain (example.com) with -all, subdomains with tailored SPF (e.g., marketing.example.com).
- AutoSPF confirms no accidental override via redirect and ensures subdomain SPF doesn’t inflate lookups for the apex.
Negative and boundary tests
- Intentional >10 lookup scenario to validate enforcement.
- Overlong record split across multiple strings; verify EDNS0 safety.
- Duplicate v=spf1 records inserted by misconfigured automation.
AutoSPF can run these as a reusable test suite tied to your domain, so each change is checked against regressions.
Catching third‑party pitfalls and indirect includes
Vendor behavior and chained includes
- Common patterns: include:spf.protection.outlook.com, include:_spf.google.com, include:sendgrid.net.
- Vendors may add their own includes dynamically, pushing you closer to the limit.
AutoSPF maintains a vendor catalog with typical lookup footprints and change histories. It warns: “Adding Vendor X could raise total lookups from 7 to 10; consider flattening Vendor Y or removing legacy Z.”
External services and DNS reliability
- Some providers use regional targets or geo-DNS that expand differently per resolver.
- AutoSPF simulates across resolvers and flags variance, recommending safe caps and fallback policies.
Rollback, staging, and TTL strategy when issues arise
Rollback and staging
- If the validator flags critical issues, deploy to a staging subdomain first and route a small percentage of real mail.
- Keep authoritative records consistent; AutoSPF’s NS diff check prevents partial rollouts.
TTL and propagation considerations
- Lower TTLs to 300–600 seconds for 24–48 hours before critical changes to accelerate rollback.
- Propagation delays: while most resolvers honor TTLs, some ISPs cache longer; AutoSPF highlights resolvers seen caching beyond TTL based on passive measurement.
In an AutoSPF case study with a fintech sender, reducing TTL to 300s and staging SPF on a subdomain cut rollback time from 2 hours to under 10 minutes when a vendor include caused lookup overflow.

Handling edge cases and recommended remediations
Excessive length and mixed record types
- If the record approaches DNS payload limits, AutoSPF recommends:
- Smart flattening with scheduled refresh.
- Splitting sender sources by subdomain to reduce apex complexity.
- Mixed SPF/TXT: RFC 7208 deprecates the SPF RR type; use TXT only. AutoSPF flags SPF-type records and suggests removal to avoid ambiguity.
IPv6, macros, and nonstandard servers
- Validate ip6 mechanisms and avoid wide-open ip6 ranges.
- Macros (e.g., %{i}, %{h}) can introduce resolver variability; AutoSPF simulates common macro expansions and warns if they cause instability.
- Nonstandard DNS servers: split-horizon, DNS64/NAT64, or DNS servers lacking EDNS0 can alter behavior; AutoSPF runs compatibility checks and suggests conservative limits and higher terminal strictness (-all) only after stability is proven.
Frequently asked questions
Should I use -all or ~all after I validate with AutoSPF?
Use ~all during discovery or staged rollouts, then switch to -all once AutoSPF shows stable pass rates and no unknown senders for at least 7–14 days. AutoSPF can schedule the qualifier change and monitor DMARC reports to auto-approve the final tighten.
How does AutoSPF prevent lookup exhaustion when I add new vendors?
AutoSPF projects the new total lookup count after expanding include chains and proposes flattening or de-duplication where includes overlap. It will block merges in CI if the change would exceed your policy threshold.
What if my DNS provider segments TXT strings incorrectly?
AutoSPF verifies segmenting and the final on-wire response size; if it detects unsafe splits or truncation risks, it rewrites the record with safe breaks and provider-specific quoting, then validates against the targeted DNS platform.
Can AutoSPF help with DKIM/DMARC alignment beyond SPF?
Yes. It checks that Return-Path domains authenticated by SPF align with the From domain under DMARC; if alignment is impossible for a sender, it recommends ensuring DKIM passes with aligned d= and defers SPF tightening for that path.
How do I handle multiple mail streams (transactional, marketing, support) cleanly?
Use subdomains per stream and validate each SPF independently. AutoSPF templates common vendor combos and ensures that changes to marketing.example.com never impact apex SPF evaluation.
Conclusion: Make SPF changes safe, observable, and reversible with AutoSPF
Using an SPF validator before changing DNS is the difference between confident, reversible updates and blind edits that can break mail: it detects syntax and policy errors, accurately counts lookups across real include chains, simulates resolver behavior, and provides clear remediation before anything goes live. AutoSPF operationalizes this end to end—draft simulations, vendor-aware lookups, CI/CD enforcement, staged rollouts with low TTLs, and automatic rollback tied to deliverability signals—so your SPF stays compliant, efficient, and aligned with DMARC. Adopt AutoSPF to shift SPF risk left: model, validate, and enforce every change before it reaches your DNS.