The one-word answer to the above question is ‘yes.’ Here’s a detailed answer to it.
SPF breaks when you forward emails because it encounters SPF validation issues. This happens because when you resend an email, it uses its own IP address and not the one used by the original sender. Since SPF relies on checking if the sending IP address is part of the SPF record, the forwarded email fails the authentication check because the forwarder’s IP address is not mentioned in the SPF record.
In easier words, if an email is forwarded, the forwarding server (let’s name it as Server B) sends the email to the recipient’s server (Server C) but typically does not change the ‘From’ address. This means that the recipient’s server (Server C) sees an email from the original sender’s domain (Domain A) coming from the IP address of the forwarding server (Server B).
In the case of mailing lists, when the mailing list server receives an email to distribute to the list members, it changes the envelope ‘From’ address. This modification triggers SPF to fail because the IP address of the mailing list server does not match the IP addresses authorized in the SPF record of the original sender’s domain.
Mitigation strategies
These approaches will help you mitigate these issues-
Use of DKIM and DMARC
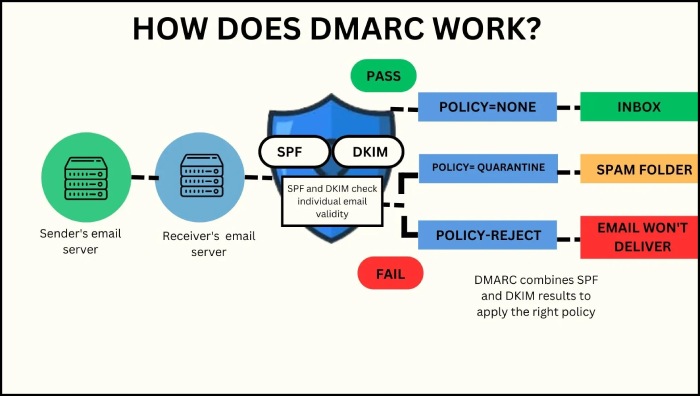
DKIM and DMARC are email authentication protocols that let recipients’ servers determine if an incoming email is legitimate or fraudulent. DKIM allows the original sender to sign the email, and this signature remains intact through forwarding. DMARC can provide policies for how to handle emails that fail SPF or DKIM checks. You can instruct the recipients’ servers to either mark such emails as spam or reject their entries altogether. In either case, the recipient’s chances of replying to an illegitimate email are minimized.
SPF ‘redirect’ mechanism
Some forwarding services use the ‘SPF redirect’ mechanism to include the forwarding server’s IP in the SPF record of the sender’s domain. However, this requires coordination between the sender and the forwarding service.
Use SRS or Sender Rewriting Scheme
SRS is a cybersecurity technique in which the sender address is altered to preserve SPF alignment, enabling the forwarded email to pass the SPF authentication check. This is done by instructing the forwarding server to rewrite the sender address to reflect that it is forwarding the email.
Use ARC or Authenticated Received Chain
ARC is a relatively new standard that resolves this problem by preserving the original email authentication information at the email service. This allows the recipient’s server to determine whether the email is legitimate or potentially fraudulent. This strategy ultimately minimizes email authentication failures for forwarded emails.
Read here to learn how to configure trusted ARC sealers for your domain.
Final words
The listed solutions are not always foolproof and require proper implementation, but they help mitigate the challenges SPF faces with email forwarding and mailing lists.
To get started with SPF, DKIM, and DMARC, for better email security contact us here.


