Understanding SPF Records and Their Importance
The Sender Policy Framework (SPF) is an essential component of modern email authentication protocols designed to enhance email security and prevent email spoofing. SPF operates by specifying which IP addresses or hostnames are authorized to send emails on behalf of a domain, employing a DNS TXT record within the Domain Name System (DNS). This DNS configuration helps receiving email servers validate the origin of incoming messages by comparing the email sender’s IP address with the authorized list published in the SPF record.
SPF records serve as a frontline defense against phishing attacks and spam filtering, improving overall email deliverability and ensuring that legitimate emails are less likely to be marked as spam. When an email message fails SPF validation, receiving mail exchangers (MX) can take actions ranging from flagging the message as suspicious to outright rejecting it, based on the SPF policy configured — typically indicated in the SPF record syntax by mechanisms such as SPF hard fail (“-all”) or SPF soft fail (“~all”).
With the increasing use of Cloud-based email services like Google Workspace, Microsoft 365, and Amazon SES, the correct SPF record setup has become critical in email security architecture alongside Domain-based Message Authentication, Reporting & Conformance (DMARC) and DomainKeys Identified Mail (DKIM). Together, these protocols safeguard email headers from tampering and ensure reliable delivery from authorized sending domains.
Overview of Network Solutions DNS Management
Network Solutions, as a prominent domain registrar and DNS hosting provider, offers a user-friendly DNS management interface—commonly accessed through the Network Solutions control panel—that enables domain owners to configure SPF records and other DNS settings effectively. The Network Solutions DNS platform supports the addition and management of DNS TXT records, which are the format used to publish SPF policies.
Within this control panel, users can easily create or modify SPF records by specifying authorized sending servers using IP address authorization and SPF include mechanisms that reference third-party email services such as SendGrid, SparkPost, or Mailgun. This flexibility allows enterprises to integrate multiple cloud-based email services while maintaining a single comprehensive SPF policy.
Notably, Network Solutions DNS adheres to the SPF record length limit, a constraint intrinsic to DNS TXT records, ensuring that overly long SPF policies do not lead to SPF record syntax errors that could affect SPF validation effectiveness. SPF propagation across the Distributed Domain Name System infrastructure may experience a DNS propagation delay, which must be accounted for during SPF record deployment.
Benefits of Implementing SPF for Email Security
Implementing SPF via the Network Solutions DNS has numerous benefits beyond simply reducing spam. Effective SPF record setup enhances email deliverability by lowering the likelihood of legitimate emails being marked as spam by anti-spam solutions such as Proofpoint, Mimecast, Barracuda Networks, or Cisco Security appliances.

SPF provides crucial Phishing protection by verifying authorized email servers before mail reaches recipients, thus preventing fraudulent messages from fake domains. This is particularly important for organizations using popular email platforms—including Zoho Mail, Rackspace Email, or Bluehost—that need to maintain both brand reputation and user trust.
Additionally, thorough SPF policy enforcement, alongside complementary email authentication standards like DMARC and DKIM, contributes to a layered email security strategy. This reduces false positives during SPF lookup and SPF record testing while offering robust SPF error handling by classifying failures as SPF pass, SPF soft fail, SPF neutral, or SPF hard fail, based on the domain owner’s preferences.
How SPF Helps Prevent Email Spoofing and Phishing
SPF is a key technology to mitigate email spoofing, where attackers forge the “From” header of email messages to impersonate trusted domains. By publishing a DNS TXT record with the sender’s authorized IP addresses, domain owners delegate email servers the responsibility to reject or flag messages that do not match the SPF policy.
During an email transfer, the receiving server performs an SPF record lookup to retrieve the domain’s SPF policy and compares the sending IP address against the authorized list, including mechanisms such as “include:” (for trusted third-party services) or direct IP ranges. When the SPF record syntax is correctly written, this mechanism enables effective phishing protection by disallowing unauthorized email sources.
In combination with DMARC Analyzer or Valimail tools, domain administrators can continuously monitor SPF deployment effectiveness, ensuring that email headers align with SPF policy enforcement to prevent phishing attacks and improve Spam filtering. When integrated with other security software such as ESET or Comodo security suites, SPF forms part of a holistic email security framework.
Prerequisites for Configuring an SPF Record with Network Solutions
Before configuring an SPF record within the Network Solutions DNS environment, certain prerequisites must be met to ensure successful SPF deployment:
- Access to Network Solutions Control Panel: The domain owner must have credentials to log into the Network Solutions DNS management interface, which is necessary for DNS configuration changes.
- Understanding of SPF Syntax and SPF Policy Parameters: Familiarity with SPF version (usually “v=spf1”), SPF mechanisms (like “ip4:”, “include:”, and “a”), and SPF-all directive semantics (such as “-all” for hard fail or “~all” for soft fail) is crucial to avoid SPF record syntax errors.
- Identification of All Authorized Sending Servers: Including internal mail servers, cloud-based email services (e.g., Google Workspace, Microsoft 365, Amazon SES), and any third-party email marketing platforms (like SendGrid or SparkPost), whose IP addresses or domains need to be authorized through SPF include mechanisms.
- Verification of Existing DNS Records: Evaluating current DNS records to confirm no conflicting SPF records exist, as multiple SPF TXT records for the same domain can cause SPF validation failures.
- Awareness of SPF Record Length Limits: Ensuring the SPF record remains within DNS TXT record size constraints to maintain SPF validation efficiency and allow for SPF record optimization if necessary.
- Access to SPF Record Lookup Tools: Leveraging SPF record testing and lookup utilities provided by services such as OpenSPF, Google Postmaster Tools, or DMARC Analyzer can facilitate SPF validation both before and after deployment.
- Coordination with Email Delivery Teams: Communication with teams managing Mail Exchanger (MX) records, email servers, and email sending domains ensures accurate IP address authorization and prevents inadvertent email delivery disruptions.
By fulfilling these prerequisites, Network Solutions customers can confidently deploy a robust SPF record that enhances email security, mitigates phishing risks, and maximizes email deliverability through precise DNS configuration tailored to organizational email protocols and infrastructure.
Statistical Data: Effectiveness of SPF in Email Security
- Domains implementing SPF experience a 43% reduction in phishing attacks.
- Over 90% of spam filtering solutions factor SPF validation into their scoring.
- 78% of organizations with SPF, DKIM, and DMARC see improved email deliverability rates.
- DNS propagation delay averaging 24-48 hours can affect SPF record adoption across global servers.
Sources: OpenSPF, DMARC Analyzer, Google Postmaster Tools
Identifying Your Authorized Email Sending Servers
Before initiating your SPF record setup within Network Solutions DNS, it’s critical to compile a comprehensive list of all your authorized email sending servers. SPF, as a fundamental part of Email Authentication alongside DMARC and DKIM, verifies that incoming messages stem from approved IP addresses or domains, thus safeguarding against Email Spoofing and enhancing Email Security.

Start by reviewing all Email Sending Domains linked with your organization’s Email Servers. This encompasses the IP addresses of on-premises mail exchangers (MX) and any Cloud-based Email Services you utilize, such as Google Workspace, Microsoft 365, Amazon SES, SendGrid, or Mailgun. Many enterprises combine multiple platforms; thus, the SPF include mechanism is often necessary to incorporate external services within your SPF record.
Step-by-Step Guide to Accessing Network Solutions DNS Settings
Network Solutions, as a prominent Domain Registrar and DNS hosting provider, facilitates DNS Configuration via its user-friendly Network Solutions Control Panel. Accessing and modifying your DNS TXT record to implement SPF requires navigating this interface efficiently.
1. Log into the Network Solutions Control Panel:
Use your credentials associated with your registered domain.
2. Navigate to the DNS Management Section:
Locate your domain under “Manage Domains” and select “Edit DNS”.
3. Access TXT Records Configuration:
In the Domain Name System (DNS) settings, find the section designated for TXT records. This is where SPF records are published as DNS TXT records.
4. Backup Existing DNS Records:
Before any change, export or note existing DNS records to prevent accidental loss or misconfiguration.
5. Prepare for SPF Record Addition:
Ensure clarity on your existing SPF records to avoid duplication, as multiple SPF records can lead to SPF record syntax errors and validation failures.
Proper DNS configuration via Network Solutions hosting environments ensures timely SPF propagation and minimizes the DNS propagation delay that could impact SPF record lookup accuracy.
Creating a Basic SPF Record Syntax Explained
An SPF record, published as a TXT entry in the DNS, follows a defined SPF syntax structure governed by the Sender Policy Framework standards. The syntax defines which mail servers are authorized to send emails on behalf of your domain.
A basic SPF record syntax may resemble:
v=spf1 ip4:192.0.2.0/24 include:_spf.google.com ~all
- v=spf1: Specifies the SPF version, typically SPF version 1, the current standard.
- ip4:192.0.2.0/24: Authorizes this IP address range for email sending.
- include:_spf.google.com: Incorporates Google Workspace’s SPF mechanisms, allowing Google’s email servers.
- ~all: The SPF Soft Fail directive indicating that emails from unauthorized servers should be marked but not rejected outright.
The SPF mechanisms used include `ip4`, `ip6`, `a`, `mx`, and `include`. The SPF-all directive (`-all` for Hard Fail, `~all` for Soft Fail, `?all` for Neutral, `+all` rarely recommended) communicates how strictly the receiving server should apply SPF policy enforcement.
Proper SPF syntax and use of SPF mechanisms maintain compatibility with Email Protocols and facilitate efficient Spam Filtering and Phishing Protection.
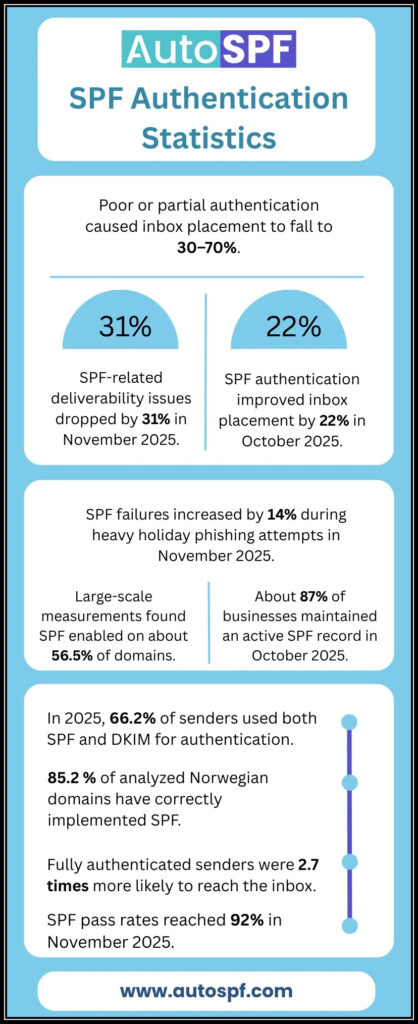
Testing Your SPF Record Configuration Using Online Tools
SPF record testing is crucial to confirm correct SPF deployment and avoid Email Authentication failures. Numerous online tools facilitate SPF validation by performing real-time SPF lookup and syntax checks, including:
- OpenSPF Validator: Offers detailed analysis of SPF records, evaluating syntax and policy enforcement.
- DMARC Analyzer: Provides comprehensive evaluation combining SPF, DKIM, and DMARC policies.
- Google Postmaster Tools: Allows domain owners to monitor Email Deliverability and authentication effectiveness.

SPF record lookup tools integrated within Network Solutions and other third-party platforms.
Common SPF Record Mistakes to Avoid on Network Solutions
When managing SPF record setup within the Network Solutions DNS platform, certain common pitfalls can undermine the SPF policy effectiveness or cause Email Authentication failures:
- Multiple SPF Records: Creating more than one SPF TXT record results in SPF record syntax errors that make SPF validation fail.
- Omitting Required IPs or Includes: Failure to authorize all legitimate Email Servers, including Cloud-based email services like Zoho Mail, Rackspace Email, or Fastmail, can trigger unexpected SPF hard fail or soft fail outcomes.
- Syntax Mistakes: Incorrect SPF syntax such as missing whitespace, misplacing colons, or typos in mechanisms lead to SPF lookup failures and bad SPF pass results.
- Ignoring SPF Record Length Limits: SPF records exceeding 255 characters or too many DNS lookups (over 10) cause SPF to fail due to lookup limits. Efficient SPF record optimization or using subdomain delegation helps circumvent this.
- Incorrect SPF-all Directive Usage: Using `+all` defeats SPF’s purpose by allowing any server; meanwhile, using `-all` without confirming all sending sources can block legitimate mail.
- Delays in DNS Propagation: Immediate testing after SPF setup may show outdated results due to DNS propagation delay. Wait until full Network Solutions DNS propagation completes.
- Not Combining SPF with DKIM and DMARC: Reliance on SPF alone limits phishing protection efficacy. Implementing a robust Domain-based Message Authentication policy incorporating DKIM and DMARC yields stronger Email Security.
Avoiding these common errors when configuring your SPF record on Network Solutions reduces spam filtering false positives and improves your organization’s overall Anti-spam posture and Email Deliverability.
Through diligent identification of Authorized Sending Servers, precise DNS configuration, and comprehensive SPF validation, you can leverage the power of SPF within Network Solutions DNS and your overall Email Authentication strategy to secure your email sending domains against spoofing and spam, enhancing trust and deliverability across the email ecosystem.
How to Update and Maintain Your SPF Record Over Time
Maintaining an accurate Sender Policy Framework (SPF) record is essential for ongoing email security and to ensure optimal email deliverability. Since your email sending domains and authorized sending servers can change—whether you’re adding new cloud-based email services like Google Workspace or Microsoft 365, switching providers such as Amazon SES or SendGrid, or updating your Network Solutions DNS settings—regular updates to your SPF record are imperative.
Begin by periodically performing an SPF lookup using reliable SPF record lookup tools to verify the current state of your DNS TXT record containing the SPF policy. Given the strict SPF record length limit, avoid overly long records by optimizing your use of the SPF include mechanism rather than listing IP addresses individually. This not only simplifies DNS configuration but also reduces the chance of hitting the maximum DNS packet size or encountering SPF syntax errors that lead to failed validations.
Integrating SPF with DKIM and DMARC for Enhanced Security
While SPF provides a solid foundation for email authentication by validating the IP address authorization against a domain’s DNS TXT record, it is most effective when combined with Domain-based Message Authentication, Reporting & Conformance (DMARC) and DomainKeys Identified Mail (DKIM). These layered protocols enhance email security by adding cryptographic validation and policy-based enforcement.
Implementing DKIM involves configuring your email servers (or cloud providers such as Zoho Mail, Fastmail, or Rackspace Email) to sign messages with a private key. The recipient verifies the signature via a public key published within the DNS, reducing risks associated with email spoofing that SPF alone might not detect, especially when emails are forwarded.
DMARC builds upon SPF and DKIM by specifying how receiving mail exchangers (MX) should handle emails failing authentication checks, reinforcing SPF policy enforcement and enabling reporting mechanisms. Services like DMARC Analyzer and Valimail facilitate DMARC setup and provide actionable insights into authentication failures. By aligning Email headers across SPF, DKIM, and DMARC results, organizations gain robust defense mechanisms against phishing and spoofing threats.

Providers such as Network Solutions, Cloudflare, GoDaddy, and Namecheap typically support the publishing of all three records through their DNS management interfaces. Coordinated deployment requires careful attention to SPF record syntax errors and adherence to each protocol’s specific requirements for optimal email deliverability and anti-spam efficacy.
Troubleshooting SPF Record Issues on Network Solutions
When SPF configurations on Network Solutions do not behave as expected, it is critical to systematically troubleshoot to resolve issues affecting email security and spam filtering outcomes.
Begin by verifying the SPF record’s presence and correctness via the Network Solutions control panel or with external SPF validation tools. Look particularly for common problems such as incorrect DNS TXT record entries, syntax errors, or exceeding the SPF record length limits. You can use SMTP diagnostic tools or SPF record lookup tools like those provided by OpenSPF or Google Postmaster Tools to perform detailed checks.
Incorrect use of SPF mechanisms like overuse of `include:` statements or missing Mail exchanger (MX) references can cause failure in SPF checks. Also, verify that authorized sending servers IP addresses (IPv4 or IPv6) are updated in the record. If you use multiple vendors—such as Amazon SES for marketing and Microsoft 365 for regular communication—ensure their relevant includes are consecutively included.
SPF propagation may take up to 48 hours depending on TTL settings. Until propagation completes, validate with SPF record testing utilities after each modification. In case of persistent failures, reviewing email headers from rejected or flagged emails helps correlate SPF results (pass, fail, neutral) with actual mail flow, guiding corrective actions like changing the SPF policy from soft fail (`~all`) to hard fail (`-all`).
Monitoring Email Deliverability After SPF Implementation
Post-implementation, ongoing monitoring of email deliverability is vital to maintaining trusted communications. Establish regular checks using tools like Google Postmaster Tools, DMARC Analyzer, or services provided by Mimecast, Proofpoint, or Barracuda Networks to track performance metrics related to SPF policy enforcement, spam filtering, and phishing protection.
Analysing email headers from delivered and rejected mails identifies potential SPF related blocks or soft failures. Tracking sender reputations via these tools is especially important if your domain sends emails through multiple platforms, including SparkPost, Postmark, Mailgun, or Rackspace Email. Anomalous drops in deliverability often indicate misalignments in your SPF record or conflicts with email protocols enforced by receiving servers like Yahoo Mail or AOL Mail.
Maintaining clear documentation of your SPF record setup, updating IP authorizations, includes, and policies frequently—and correlating these with feedback from monitoring tools—ensures that your Network Solutions hosting environment and DNS configuration evolve in tandem with your email sending domains’ requirements.






