Understanding SPF Records: A Primer
The Sender Policy Framework (SPF) is a foundational component of email authentication, designed to combat email spoofing and enhance email security. By defining an SPF record—stored as a DNS TXT record within a domain’s DNS zone—administrators specify which mail servers are authorized to send emails on behalf of their domain. This SPF record adheres to the SPF syntax and SPF specification RFC 7208, outlining an SPF policy that email receivers process during SPF evaluation to validate the sender’s legitimacy.
An SPF record follows a precise SPF record structure, beginning with an SPF version (commonly `v=spf1`) and consists of several SPF mechanisms (such as `ip4`, `include`, `a`, `mx`, `ptr`, and `exists`), SPF modifiers (notably `redirect` and `exp`), and qualifiers that determine how SPF checks respond to matching or non-matching conditions. For instance, SPF includes allow incorporation of external SPF records from trusted third-party senders—commonly mail service providers like Google Workspace, Microsoft Office 365, SendGrid, or Amazon SES—to enable proper SPF validation for delegated services.
SPF processing involves SPF record parsing and SPF evaluation mechanisms at the receiver’s end, which perform multiple DNS lookups to resolve these mechanisms. Any failures during DNS queries, such as SPF DNS failures or DNS timeouts, may lead to SPF errors or SPF validation issues, negatively impacting email deliverability.
What is SPF Lookup Count?
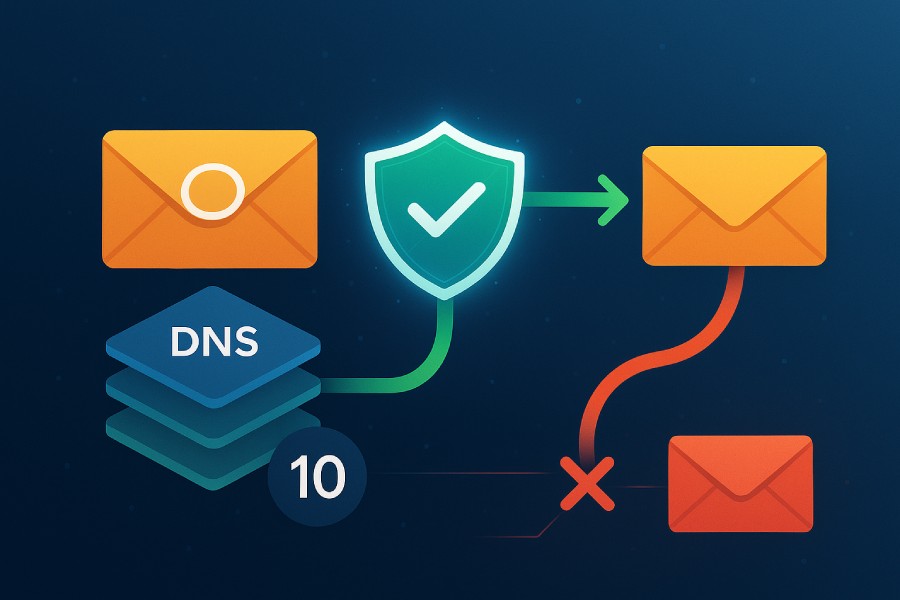
SPF lookup count refers to the total number of DNS TXT record queries made during the SPF evaluation process when parsing SPF mechanisms that require DNS lookups. Specifically, DNS query types triggered during SPF processing include queries to resolve SPF record in DNS zone, `include` directives, `a`, `mx`, and `exists` mechanisms. Each of these mechanisms may initiate additional DNS TXT record lookups.
Importantly, SPF lookup count includes recursive lookups caused by SPF includes and SPF recursive lookup through linked domains’ SPF records. Email gateways and receiving mail servers have a hard SPF DNS lookup limit set to prevent excessive DNS overhead and delay, commonly a threshold of 10 DNS lookups per SPF evaluation as mandated by the SPF specification RFC 7208.
Exceeding this SPF DNS lookup limit results in an SPF lookup count error or SPF record limit exceeded condition, causing SPF evaluation to fail or return a `PermError`. This in turn can lead to email rejection or classification as spam, significantly impacting SPF email deliverability.
The Technical Limitations of SPF Lookups
The SPF limit is fundamentally a safeguard against excessive DNS overhead and preventing performance degradation during email processing. The SPF DNS lookup limit enforces that SPF evaluation cannot exceed 10 DNS TXT record lookups per SPF authentication check. This means that if your SPF record includes multiple nested includes or complex SPF mechanisms such as nested includes or recursive lookups, the total DNS lookups cumulate quickly and potentially breach the SPF limit.
Furthermore, SPF recursive lookup multiplies the number of SPF DNS queries because each included domain in an SPF include undergoes its own SPF record parsing and DNS queries, increasing DNS overhead significantly. SPF macro expansion, used for dynamic domain evaluation, can also impact SPF DNS query counts but does not itself trigger additional lookups.

DNS caching mechanisms, employed by providers like Cloudflare, Google Public DNS, and DNS Made Easy, can reduce SPF DNS overhead by temporarily storing DNS responses. However, real-time SPF validation tools such as MxToolbox, UltraTools, or DMARC Analyzer, used for SPF record testing and SPF troubleshooting, often highlight SPF DNS lookup counts and potential SPF DNS recursion problems during SPF record optimization.
SPF record length and complexity—especially when multiple third-party services (e.g., SendGrid, Amazon SES, SparkPost, Postmark) are authorized via SPF includes—can contribute to surpassing SPF limits, causing SPF DNS timeout or SPF bypass attempts if the SPF DNS lookup limit is exceeded.
How SPF Lookup Count Affects Email Deliverability
The SPF lookup count is critical because exceeding the SPF DNS lookup limit results in SPF evaluation failure, which harms email deliverability by triggering SPF error conditions on receiving servers’ side. Email receivers, including major providers like Google Workspace and Microsoft Office 365, perform SPF validation as part of their email security policies. If SPF checks return a failure due to SPF DNS lookup limit exceeded, emails can be rejected outright or flagged as spam, undermining the protective intent of the Sender Policy Framework.
SPF email deliverability is often tightly linked with complementary email authentication protocols such as DKIM and DMARC. Misconfiguration in SPF that leads to SPF lookup count error can create vulnerabilities exploitable via SPF bypass or spoofing techniques, reducing overall email security. Organizations leveraging security services like Proofpoint, Mimecast, Barracuda Networks, and Trend Micro rely heavily on strict SPF evaluation mechanisms combined with DMARC Analyzer to enforce policy adherence.
Moreover, a long or improperly structured SPF record (i.e., poor SPF record structure and lack of SPF record optimization) increases SPF DNS queries and can slow down SPF processing, potentially causing SPF DNS timeout, further degrading the user experience. SPF flattening, a best practice technique to reduce SPF DNS queries by replacing includes with direct IP entries, has gained traction among large-scale email senders and cloud service providers such as Google Workspace or Amazon SES, effectively mitigating SPF lookup count issues while complying with SPF best practices.
Common Causes of High SPF Lookup Counts
Several common configurations and missteps contribute to increased SPF lookup counts, often observed during SPF record testing and SPF troubleshooting phases:
- Excessive SPF includes: Authorizing multiple third-party vendors and services like SendGrid, SparkPost, Postmark, Mailchimp, Mandrill, Zoho Mail, or Amazon SES via SPF includes exponentially increases SPF DNS queries. Each include leads to SPF recursive lookup, multiplying DNS lookups.
- Nested Includes: Some SPF records use nested SPF includes (an included SPF record that itself includes additional includes), aggravating SPF DNS recursion and raising SPF DNS overhead risks.
- Misconfigured SPF record structure: Overly long SPF records or poorly optimized records with redundant mechanisms increase SPF record length and require more DNS lookups during SPF evaluation.
- Reliance on mechanisms triggering DNS lookups: Using mechanisms like `mx`, `a`, `exists`, or `ptr` without care for their DNS query implications can escalate SPF lookup counts, as these require DNS TXT or A/AAAA record lookups.
- Use of SPF modifiers like `redirect` inappropriately: The `redirect` modifier causes an entire SPF evaluation against a different domain, adding multiple DNS queries to evaluate that domain’s SPF record.
- Lack of SPF record optimization and flattening: Not implementing SPF record optimization or flattening techniques causes repeated DNS queries for included services, escalating SPF DNS query types and causing SPF DNS overhead.

Email service providers including Microsoft Office 365, Google Workspace, Oracle, and cloud registrars like GoDaddy, Bluehost, or Namecheap play significant roles in SPF deployment and must educate users on SPF record limits to prevent SPF lookup count errors and maintain SPF validation integrity.
Through continuous SPF record testing using tools such as DMARC Analyzer, MxToolbox, UltraTools, or EasyDMARC, administrators can identify and correct SPF DNS lookup count issues before they cause SPF record limit exceeded errors or SPF DNS timeout conditions, ensuring robust email security and reliable SPF email deliverability.
Tools and Methods to Measure SPF Lookup Count
Monitoring and managing SPF DNS queries is critical for maintaining robust email authentication and ensuring SPF validation remains within the SPF DNS lookup limit specified in the SPF specification RFC 7208. Various tools and methods enable administrators to measure their SPF lookup count effectively.
SPF validation tools like MxToolbox and UltraTools offer comprehensive SPF record testing features. These platforms perform simulated SPF processing by parsing the SPF record structure and its SPF mechanisms, such as `include`, `a`, `mx`, `ptr`, and `exists`, to calculate the total number of DNS lookups executed during SPF evaluation. This count reflects the DNS TXT record queries triggered as part of SPF verification, exposing any SPF record limit exceeded issues.
Similarly, DNS diagnostic tools provided by DNS Made Easy, GoDaddy, and Namecheap include SPF record parsing and SPF checks within their DNS lookup utilities. Cloudflare’s DNS analytics also provide valuable SPF DNS query types insights, including SPF DNS recursion and SPF DNS failures, useful for diagnosing SPF DNS overhead in email workflows.
Likewise, SPF deployment solutions like Valimail, Agari, and EasyDMARC integrate SPF lookup count monitoring with DMARC Analyzer dashboards, correlating SPF validation results with SPF and DMARC policy compliance to maximize overall email security.
The Impact of DNS Lookups on SPF Evaluation
Every SPF evaluation involves executing multiple DNS queries to retrieve DNS TXT records containing SPF policies associated with authorized senders. Each SPF mechanism in the SPF record triggers potentially multiple DNS lookups, especially when SPF includes or SPF recursive lookup chains are present. These DNS lookups add latency to SPF processing and can affect SPF email deliverability if SPF DNS timeouts or SPF DNS failures occur.
The SPF DNS lookup limit is set at 10 per SPF evaluation to mitigate DNS overhead and prevent SPF bypass scenarios stemming from excessively complex or malformed SPF records. Exceeding this limit results in an SPF error or SPF lookup count error, causing SPF validation failure and possibly marking legitimate messages as unauthorized.

Moreover, SPF DNS cache performance plays a notable role in reducing the impact of DNS queries on SPF evaluation. Providers like Google Public DNS, Oracle DNS, and Cisco’s DNS infrastructure optimize SPF DNS responses through aggressive caching strategies, lowering DNS lookup latency and minimizing SPF DNS overhead for high-volume email platforms such as Microsoft Office 365, Google Workspace, and Amazon SES.
Best Practices for Managing SPF Lookup Count
Adhering to SPF best practices helps prevent SPF record limit exceeded errors and optimizes the SPF policy for effective email authentication without compromising DNS infrastructure.
- Keep SPF Record Length Reasonable: Avoid excessive SPF record length by removing redundant or deprecated mechanisms. SPF record optimization tools from providers like Barracuda Networks and Mimecast facilitate SPF record parsing to detect unnecessary SPF includes or SPF modifiers.
- Minimize Use of Recursive Lookups: SPF DNS recursion amplifies SPF DNS queries. Limiting SPF recursive lookup chains ensures compliance within the SPF DNS lookup limit.
- Avoid Excessive Include Mechanisms: Each `include` triggers at least one DNS query. Prefer consolidating authorization mechanisms when possible.
- Use SPF Macro Expansion Prudently: Overuse of SPF macro expansion increases DNS TXT record queries and complicates SPF syntax, potentially prolonging SPF processing time.
- Regular SPF Record Testing: Routine SPF evaluation mechanism testing via SPF validation tools is essential for early detection of SPF lookup count errors or SPF DNS timeouts.
Industry leaders like Proofpoint, Trend Micro, and Symantec provide managed SPF troubleshooting services that contribute to maintaining strong SPF records and enhancing overall email security posture.
Simplifying SPF Records to Reduce Lookups
A critical step in controlling SPF DNS lookup count is simplifying the SPF record structure by reducing unnecessary SPF includes, qualifiers, and mechanisms. Many organizations using email services such as SendGrid, SparkPost, Mailchimp, Mandrill, and Postmark encounter complexities induced by multiple third-party sending sources necessitating expansive SPF records.
Strategies for simplification include:
- Consolidate IP Address Ranges: Merge IP ranges under fewer `ip4` and `ip6` directives rather than relying heavily on `a` or `mx` mechanisms, thus decreasing the number of DNS lookups triggered by these mechanisms.
- Remove Redundant SPF Includes: Identify overlapping or obsolete SPF includes using DNS TXT record lookups and SPF record parsing for cleaning the SPF policy.
- Limit Use of `ptr` and `exists` Mechanisms: These mechanisms are notoriously DNS-intensive due to recursive lookups, often resulting in elevated SPF DNS overhead.
Providers like Zoho Mail and Microsoft Office 365 recommend auditing mail flow infrastructure periodically to update SPF records reflecting only active mail sources, effectively reducing SPF DNS queries.
Role of Include Mechanisms and Their Impact on Lookups
The `include` SPF mechanism is pivotal to the Sender Policy Framework, allowing organizations to authorize external third-party senders by referencing their SPF record in DNS. While highly flexible, SPF includes substantially contribute to SPF DNS query counts due to:
- Additional DNS TXT Record Lookups: Each `include` triggers a DNS lookup to fetch the referenced SPF record, potentially traversing SPF recursive lookup chains.
- Compound SPF Record Structures: Frequently nested `includes` amplify DNS query volume, increasing the risk of SPF record limit exceeded scenarios.
For example, integrating email services like Amazon SES, SendGrid, and SparkPost often involves including their respective SPF records in the domain’s SPF record. Since these service providers frequently update their SPF records to maintain email security, these dynamic references require robust SPF record management to prevent SPF lookup count errors.
To mitigate this impact, entities such as DMARC Analyzer and EasyDMARC advise combining SPF includes cautiously and using SPF record optimization to flatten or simplify inclusion chains.
Using SPF Flattening Techniques Effectively
SPF flattening is a method used to transform an SPF record containing multiple includes or mechanisms into an equivalent SPF record consolidating IP addresses, thereby reducing the number of DNS queries required during SPF evaluation.

This technique involves:
- Performing DNS lookups for all `include` statements upfront.
- Extracting IP addresses enumerated in those referenced SPF records.
- Replacing `include` mechanisms with `ip4` and `ip6` directives listing the resolved IP addresses.
- Updating the DNS TXT record with this flattened SPF record.
SPF flattening significantly decreases SPF DNS queries during normal SPF processing, lowering SPF DNS overhead and mitigating SPF DNS timeout and SPF DNS failures risks. However, it carries challenges:
- Maintenance Overhead: Since third-party services update their IP ranges frequently, relaxed SPF record optimization without regular SPF record testing can lead to out-of-date IP lists and SPF validation errors.
- SPF Record Length Limit: Flattening may increase the SPF record length beyond DNS TXT record or DNS packet size limits.
Valimail and Agari provide advanced SPF flattening tools with automation features to refresh flattened SPF records regularly, adhering to SPF best practices and avoiding SPF record limit exceeded issues.
Moreover, SPF flattening aligns well with accompanying email authentication frameworks such as SPF and DKIM and SPF and DMARC, helping maintain email security while balancing SPF DNS lookup count constraints.
By leveraging appropriate tools and implementing strategic SPF policy management, organizations can optimize their Sender Policy Framework deployments to ensure effective email authentication, mitigate SPF errors, and improve SPF email deliverability across leading email platforms and security infrastructures.
Case Studies: SPF Lookup Count and Delivery Failures
Several organizations have encountered challenges related to the SPF DNS lookup limit, which directly impacts email deliverability and email security. For example, a case study involving a multinational corporation utilizing Microsoft Office 365 and Amazon SES revealed that their SPF record, which incorporated multiple SPF includes, rapidly approached the maximum of 10 DNS lookups as specified in the SPF specification RFC 7208. This excess in SPF DNS queries triggered SPF record limit exceeded errors, resulting in SPF evaluation failures and causing legitimate emails to be rejected or flagged by recipient servers.
Similarly, a mid-sized marketing firm using SendGrid alongside Google Workspace experienced SPF lookup count errors during SPF processing due to recursive SPF DNS lookups from chained SPF includes. This increased SPF DNS overhead led to SPF DNS timeout issues and SPF DNS failures, ultimately affecting SPF email deliverability. By employing SPF record optimization techniques such as SPF flattening, they reduced SPF DNS queries and improved SPF validation performance across their DNS TXT record. Utilizing SPF validation tools like MxToolbox and UltraTools allowed for better SPF record testing and SPF troubleshooting throughout deployment.
Moreover, a cybersecurity vendor leveraging Cisco and Proofpoint solutions highlighted the risks of overly complex SPF record structures, which often invoke recursive SPF DNS recursion and SPF macro expansion, causing increased SPF DNS cache pressure and DNS query load. This case emphasized the importance of adhering to SPF best practices, including minimizing SPF record length and avoiding redundant SPF modifiers, to ensure stable SPF checks without surpassing the SPF limit.
The Relationship Between SPF Lookup Count and DMARC Alignment
Sender Policy Framework (SPF) and Domain-based Message Authentication, Reporting & Conformance (DMARC) operate in tandem to enhance email authentication and protect domains from spoofing and phishing. DMARC alignment requires the domain used in the SPF evaluation mechanism to match the envelope sender domain, which influences SPF record deployment strategies.
However, excessive SPF DNS queries triggered by complex SPF includes or numerous SPF modifiers can lead to SPF DNS lookup limit breaches, causing SPF bypass and failed SPF validation. When SPF fails, DMARC relies more heavily on DKIM for authentication; in cases where DKIM signatures are absent or misconfigured, DMARC alignment failures increase, undermining email security.
Enterprises using DMARC Analyzer and EasyDMARC have leveraged insights from SPF record parsing and SPF evaluation results to streamline SPF records. Simplifying the SPF policy reduces SPF lookup count errors and ensures SPF and DMARC outcomes are consistent, preserving SPF email deliverability and overall email authentication integrity. Combining SPF and DKIM correctly enhances DMARC’s efficacy, as cloud email security providers like Mimecast and Barracuda Networks recommend optimizing SPF records alongside DKIM signatures for stronger authentication results.
Future Trends in SPF and Email Authentication
The ongoing evolution of email security suggests that Sender Policy Framework will continue adapting to meet increasing demands for scalability, reliability, and ease of management. One notable trend is advanced SPF record optimization techniques, including intelligent SPF flattening and the use of programmatic SPF record generation tools from providers like Valimail and Agari. These approaches aim to reduce SPF DNS overhead and prevent SPF DNS query floods, preserving SPF DNS cache efficiency and minimizing SPF error occurrences.

There is a growing interest in integrating machine learning and AI into SPF troubleshooting and SPF record testing processes, facilitated by platforms such as DMARC Analyzer and SparkPost. Predictive analytics could pre-emptively identify SPF DNS failures and SPF record limit exceeded issues, helping administrators maintain compliance with the SPF specification RFC 7208 while maximizing SPF email deliverability.
Moreover, emerging standards may introduce enhancements to the SPF syntax or SPF mechanism to accommodate more complex SPF policies without breaching the SPF DNS lookup limit. Cloudflare and Google Public DNS’s innovations in DNS query management—particularly efforts to reduce DNS lookup latency and recursive SPF DNS lookups—are poised to improve SPF processing speeds significantly.
Finally, the consolidation of SPF, DKIM, and DMARC into unified email authentication frameworks could enhance policy correlation and reporting capabilities, offering more resilient protection against SPF bypass and fostering a higher level of trust in email communications worldwide.